10 Popular SCA Tools to Protect Your Code in 2025
Updated June 3, 2025

Software Composition Analysis (SCA) tools have been around since 2002, and they are now more critical than ever for identifying vulnerabilities in your codebase's libraries, frameworks, and third-party components.
According to a Capterra report, 61% of businesses have been affected by a supply chain threat in the last year. If you’re one of the lucky 39%, Capterra suggests it really came down to luck - as nearly all companies use at least one third-party vendor.
This article explores the best SCA security tools to protect your code. But before you make the investment, let’s understand what SCA is and what features to look for in these tools.
Top 10 SCA Tools to Protect Your Code in 2025 at a Glance
- Best overall SCA tool to protect your code in 2025: Jit
- Best tool for accurate commit-level scanning: OSV Scanner
- Best SCA tool for secret detection: Spectral
- Best tool for cloud-native SCA: Wiz
- Best SCA tool for hybrid testing: SOOS SCA
- Best tool for enterprise SCA security: Snyk
- Best SCA tool for node.js security: npm-audit
- Best tool for embedded SCA: TimeSys
- Best SCA tool for license compliance: Mend.io
- Best SCA tool for portfolio analysis: Cast Highlight
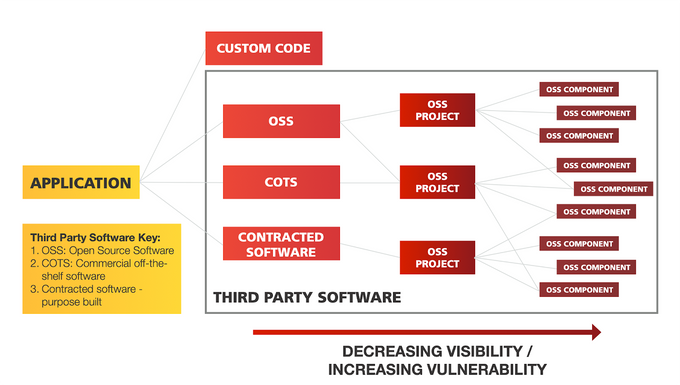
What is Software Composition Analysis (SCA)?
So, you're coding away, building something extraordinary, and then you realize you're standing on the shoulders of giants—using other people's open-source libraries and frameworks. Have you ever wondered how safe all that borrowed code is?
Enter Software Composition Analysis, or SCA for short. Think of it as a more specialized form of Static Application Security Testing (SAST) but with a focus on your project's package.json, Gemfile.lock, or similar dependency files.
SCA tools cross-reference your project's dependencies against various vulnerability databases like the National Vulnerability Database (NVD) and other proprietary databases. It then flags these issues in your CI/CD pipeline or even directly within your IDE, offering recommendations for mitigation.
Key features to look for in SCA tools
- AI agents to offload manual AppSec tasks: Modern SCA platforms embed AI assistants—such as GitHub Copilot for Security, the Jit AI Engine, or Snyk AI Advisor—that automatically scan dependency graphs, flag outdated packages, and even draft secure upgrade PRs. These agents can bulk-fix version bumps or suggest code changes, freeing developers and AppSec engineers from repetitive triage.
- Contextual prioritization of vulnerabilities: Best-in-class tools go beyond CVSS scores by asking “Is the vulnerable code actually reachable?” and “Does it touch sensitive data or an internet-facing path?” Jit’s reachability analysis correlates call-graph data with live traffic to surface only exploitable flaws, while Snyk’s Priority Score weights network exposure, popularity, and exploit maturity. This context focus slashes alert noise and directs teams to the risks that truly matter.
- Seamless CI/CD integration: Effective SCA solutions plug directly into pipelines—GitHub Actions, GitLab CI, Jenkins, Azure DevOps—so every pull request runs dependency scans and blocks high-severity issues pre-merge. Jit’s GitHub App adds status checks and Snyk’s native GitHub Action auto-generates fix PRs. Tight integration ensures vulnerabilities are caught early without slowing delivery.
- Developer-centric UX: An intuitive experience drives adoption. For example, inline IDE pop-ups (VS Code, JetBrains) that highlight vulnerable imports, one-click fix suggestions, and clean dashboards that map risks to owners. By meeting developers where they work, these tools turn security chores into quick, confident tasks rather than post-release firefights.
Top 10 SCA Security Tools to Protect Your Code in 2025
Benefits of SCA tools
- Fortified security: SCA tools intensify your application's security by auditing third-party components and recommending patches or safer alternatives. In 2022, application layer attacks were up by 165% compared to the previous two years, so closing security gaps should be up there on your priority list.
- Streamlined compliance: Laws like GDPR and CCPA impose strict data protection standards, and compliance is non-negotiable. SCA automates this by flagging components that fall short of regulatory norms, a vital feature for industries like healthcare and finance.
- Accelerated development: You receive instant security feedback by integrating SCA into your CI/CD pipeline. This allows developers to fix issues on the fly, boosting efficiency and conserving resources.
- Enhanced transparency: SCA tools offer detailed insights into your project's dependencies, fostering team-wide understanding and informed choices on component use. This clarity is also invaluable for audits, whether for regulatory compliance or M&A due diligence.
Fortify your software supply chain for 2023 and beyond
When supply chain attacks are surging, having a fortified defense strategy is the minimum you can do to protect your code and, eventually, your app’s users. Software Composition Analysis (SCA) tools are indispensable allies in this battle, providing you with the critical capabilities to scrutinize every element that interacts with your codebase.
Whether you aim for streamlined compliance, instant vulnerability alerts, or continuous monitoring, the right SCA tool is out there to meet your specific needs. Jit kicks things off with a unified DevSecOps platform that seamlessly integrates SCA and many other security tools into your CI/CD pipeline- helping you achieve Minimum Viable Security with no operational overhead.