6 Essential Steps to Using OWASP ZAP for Penetration Testing
Penetration testing is an effective way of identifying the vulnerabilities in your cybersecurity. Now it can be done with simple open-source tools like OWASP ZAP.
Updated November 5, 2024.

There's no doubt that no organization wants to be the victim of a cyber attack, but even the most security-minded entity can find itself caught off-guard or exposed when a zero-day exploit is discovered.
In addition, with the complexity of our systems (apps, networks, and websites) and the increase in various vulnerabilities discovered daily, it's becoming harder and harder to stop them all.
Today, we are much more well-positioned to overcome security challenges, with many excellent open-source security tools, knowledge, and awareness to support better security hygiene.
One excellent tool that has been a game changer for simplifying security detection and remediation is OWASP ZAP, an open-source community project that provides great out-of-the-box DAST for your web apps. Here's our tutorial to help you get started.
What Is Penetration Testing?
The purpose of a penetration testing tool is to identify security vulnerabilities like SQL injections that attackers could exploit to gain access to sensitive data or systems. It can help a business protect against bad actors by identifying security weaknesses and providing recommendations for improving the organization's security posture.
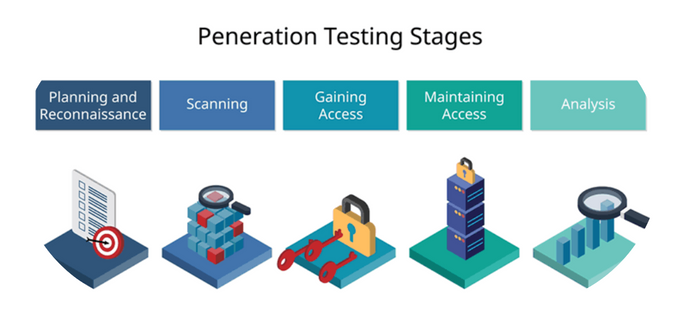
5 Stages of Penetration Testing
Phase 1: Planning and Reconnaissance
Planning and reconnaissance are the first steps in pentesting your website. It helps the tester understand the target environment and identify potential vulnerabilities, allowing them to create a plan of attack and choose the appropriate tools and techniques for the test.
Phase 2: Scanning
The scanning stage is the process of identifying the systems and services that are running on a network to determine which are vulnerable and which are not. The scanning stage also allows the penetration tester to choose the best way to attack the systems on the network.
Phase 3: Gaining System Access
In this phase, the attacker tries to gain access to the system by exploiting vulnerabilities, brute forcing passwords, or social engineering. This stage is crucial because it highlights when the attacker can gain access to the system and start to compromise it.
Phase 4: Persistent Access
This is where the attacker attempts to maintain access to the system after the initial compromise. Persistent Access can be done through some methods, such as installing a backdoor, setting up a persistent reverse shell, or adding a user to the system with elevated privileges.
This stage allows the attacker to maintain a foothold on the system even if initial access is lost. This can impact your business by enabling the attacker to monitor your system continually, collect sensitive data, or launch further attacks against other systems.
Phase 5: Analysis and Reporting
This is when the tester analyzes the data gathered during the OWASP ZAP assessment and creates a report detailing their findings for the client to understand the impact of vulnerabilities and take appropriate action to mitigate any risks.
How to Use OWASP ZAP for Security Penetration Testing
ZAP is short for "Zed Attack Proxy", which is leveraged by many testers to find security vulnerabilities in web applications, understand and fix security issues, and maintain long-term security hygiene by creating a baseline security assessment of a web application.
1. Install ZAP
The first step in our penetration testing guide is downloading the latest version from the OWASP ZAP website for your operating system to install ZAP or reference the ZAP docs for a more detailed installation guide.
Once completed, follow the prompts to install OWASP ZAP on your machine.
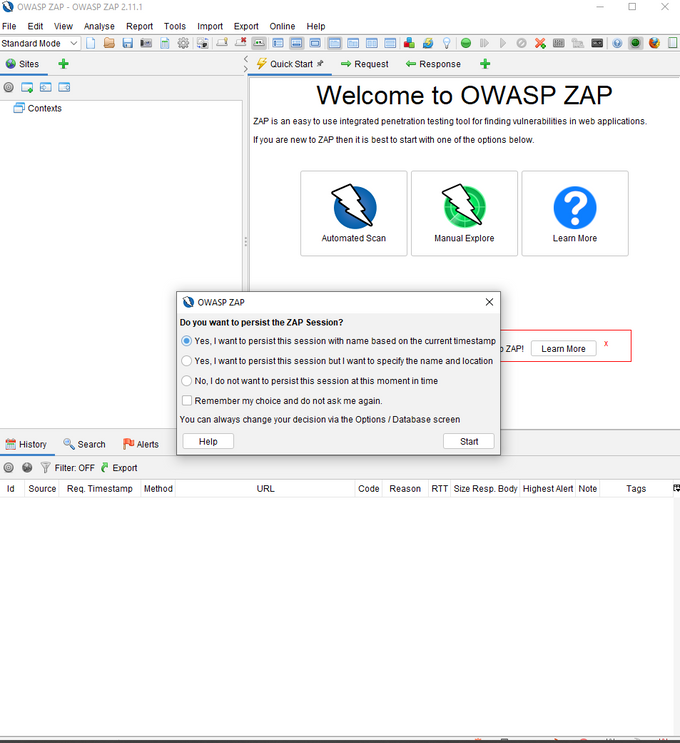
2. Persist a Session
Persisting a session means that the session will be saved and can be reopened at a later time. This is useful if you want to continue testing a website or application at a later time.
Once you’ve started the application, you'll see this screen:
The prompt gives two options to persist in the session. You can use the default to name the session based on the current timestamp or set your name and location.
Alternatively, you can persist a session by going to ‘File’ and choosing ‘Persist Session…’. Give your session a name and click ‘Save’.
3. Run an Automated Scan
Running an automated scan is a way to check for common security vulnerabilities in web applications without manually initiating the analysis. This is done by sending requests to the application and analyzing the responses for signs of common vulnerabilities. It can help to find security issues early in the development process before they are exploited.
With OWASP ZAP, you can use a ZAP spider or the AJAX spider. So what’s the difference?
ZAP spider is a web crawler that can automatically find security vulnerabilities in web applications. Meanwhile, the AJAX spider is a web crawler designed to crawl and attack AJAX-based web applications.
Clicking on the ‘Tools’ option will give you a list of available penetration testing tools provided by OWASP ZAP.
To run an automated scan, you can use the quick start “Automated Scan” option under the “Quick Start” tab. Enter the URL of the site you want to scan in the “URL to attack” field, and then click “Attack!”.
4. Interpret Test Results
Interpreting test results in OWASP ZAP is vital to understand the scan findings and determine which issues require further investigation. Additionally, it can help to prioritize remediation efforts.
You can view alerts by clicking on the 'Alerts' tab. This tab will show you a list of all the alerts that have been triggered during your testing, sorted by risk level, with the highest risk alerts at the top of the list. You can also see details of the discovered vulnerabilities and suggestions on how you can fix them.
5. View Alerts and Alert Details
Viewing alerts and alert details in OWASP ZAP is a way to see what potential security issues have been identified on a website. It can help security and administrators understand what needs to be fixed to improve the app's security.
If you can't find your ‘Alerts’ tab, you can access it via the ‘View’ menu along with other options. Once you have your ‘Alerts’ tab, you can navigate the various vulnerabilities discovered and explore the relevant reports.
6. Explore an Application Manually
Exploring an application manually in OWASP ZAP is a process of manually testing the application for security vulnerabilities. Doing this can help ensure that the application design is as secure as possible.
The manual scan complements the automated scan by providing a more in-depth analysis of the application and allowing you to navigate the penetration test process.
The automated scan may miss some vulnerabilities, but the manual scan may pick up missed issues at the cost of extra time, making it potentially unsuitable for larger data sets.
To explore an application manually, select 'Manual Explore.' Select your browser, which will launch a proxy in your browser. Here, you will be given penetration testing tools such as spiders, and if a vulnerability is discovered, an alert flag will be added to the alerts panel.
Other Types of Security Testing
As security continues to evolve, so do the methods used to test the security of systems and networks.
Security testing is more necessary than ever to identify vulnerabilities and have a real-time understanding of the risks posed to your organization through its code and systems. This is where continuous security comes in.
To stay ahead of would-be attackers, we can employ different types of scans and tests to get the most coverage for our stacks. Some of the most popular types include:
- Vulnerability assessment: Analyzing a system or application to identify security risks is an essential method as it can help to prevent attacks by identifying and fixing security vulnerabilities.
- Runtime testing: Testing software during its execution to reveal errors that may not be apparent during design or compilation.
- Code review: Inspecting code for potential errors, vulnerabilities (like malicious code), and compliance issues to safeguard your business systems from malicious attacks before they occur. Code reviews can also help ensure compliance with industry and government regulations.
Where to From Here?
Having a developer perform a penetration test checklist with OWASP ZAP is one way to do a security audit. However, manual processes often sacrifice efficiency. This is where Jit comes in.
We know that pen testing is essential, but it can be cumbersome, mainly if your development team is already preoccupied with finishing features and needs to release the next cycle of updates for your applications. In addition to this, OWASP ZAP only covers one part of the pipeline.
With Jit, your team can quickly implement full code-to-cloud security coverage, including DAST, across your repos. Security doesn’t have to be the last port or forgotten thought.