AWS Security Token Service (STS): 7 Essentials to Save You Time
AWS STS supports your company's data security by enabling you to use temporary security credentials across your entire cloud infrastructure—and with these essentials, you will save time and enhance your AWS security.
Updated February 28, 2024.
Sharing is caring. But when it comes to sharing security credentials, you can’t be too generous. Issuing long-term security credentials to users or clients could open the door to a litany of security problems, from data loss to malicious (and costly) attacks.
As corroborating evidence, 82% of data breaches involve human elements related to poor access management, such as credential theft by employees (with legitimate access permission), misusing or mishandling information, or falling victim to phishing.
Enter Security Token Service—Amazon Web Services's offering. This service dynamically creates security tokens with a short life span so that access is given only on a necessity basis, considering zero trust principles. In this article, I’ll dive into AWS STS and share essential tips on managing AWS STS more efficiently.
What Is the AWS Security Token Service (STS)?
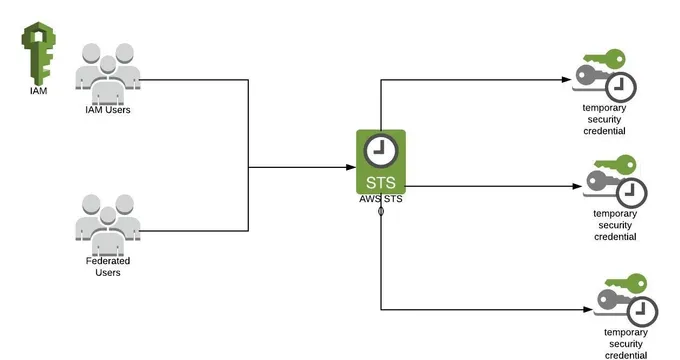
Amazon Web Services (AWS) Security Token Service (STS) is a tool that provides temporary access to IAM roles with their own permissions. It generates credentials (access key, secret access key, and token) for a short time (15m-36h). Users must request new credentials if they need access beyond the expiration time.
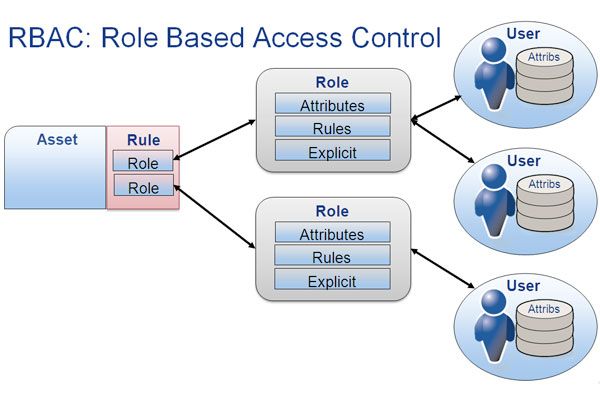
AWS STS works seamlessly with the Role-Based Access Control model, which determines that permissions are given to roles instead of users (similar to STS), enabling companies to gain more control over who is accessing what.
AWS STS helps you work with external personnel on your AWS infrastructure safely and efficiently. It aligns with the principle of least privilege, reduces your attack surface, and helps cover regulatory controls like AWS FTR and SOC2.
Jit is now FTR-approved and available on AWS Marketplace as an AWS partner. You can access our DevSecOps platform, build your Minimum Viable Security Product, or enhance your security capabilities with our open-source security tools.
» Take a look at our guide to AWS security tools
How Does AWS STS Work?
Established users request STS tokens without creating a new IAM user. The identification process involves 3 simple steps.
- Step 1: AWS identifies the IAM user and issues a temporary security token.
- Step 2: The user uses that token to assume a new role, usually one with more access than usual.
- Step 3: The client can now use this new role and timed session to access and manipulate the requested resources. A complete log of all this is created and maintained.
Non-recognized AWS IAM users can still get access without permission from a Cogito-recognized third-party identity provider.
AWS Security Token Service (STS): 7 Time-Saving Essentials
1. Bypass Public Internet When Accessing Your VPC
You can create a private connection between your Amazon VPC (Virtual Private Cloud) and AWS STS. Using this connection, you can bypass the public internet when connecting to the resources hosted on your VPC.
This provides better privacy since only authorized users can access it and improved security by limiting access through time-limited STS credentials that vary on a case-by-case basis.
2. Use STS to Streamline Cross-Account Access
A lot of businesses have multiple AWS accounts active. You can create user identities in one account and use those identities to access AWS resources in other accounts that are part of your business by using the roles with STS to allow cross-account access.
This process is known as Temporary Access Rights Delegation (TARD) scheme. One of its significant benefits is that it reduces the key management overhead for guest network devices.
3. Leverage Role-Based Access Control
Usually, in AWS, the users' access level is defined by their role. This is also the premise of Role-Based Access Control (RBAC), a popular access control method that is policy-neutral and restricts network access based on a user’s role within an organization. Users can assume these roles based on their access needs, and roles can be assigned and revoked anytime.
Imagine that your IT Helpdesk team needs access to a specific IT application to perform their tasks. Giving the same access controls to each user, one by one, would be an administrative nightmare (and potentially a security nightmare, too). Instead, this team could be assigned the same role with the same permissions and policies.
STS provides an additional level of security by temporarily allocating roles to users. This allows users to access certain privileges for a limited time and on a case-by-case basis. The code example below demonstrates how to create a user and assign a role to them using STS.
4. Use Regional STS Endpoints
STS is, by default, a global service with a single endpoint for all requests. Instead of using that single global endpoint, you should use regional STS endpoints to decrease latency, add redundancy, and extend session token validity.
For example, session tokens from AWS Regional STS endpoints are valid across all AWS Regions, while session tokens from the global STS endpoint are only valid in AWS Regions enabled by default. The versatility of regional tokens depends significantly on your AWS infrastructure and use case.
When working with AWS Regional STS endpoints, it is also important to ensure that your AWS Security Groups are properly configured to allow traffic to and from the appropriate endpoints.
5. Monitor Token Usage
You can’t talk about cloud security without mentioning monitoring capabilities. Amazon offers several handy tools to monitor your AWS resources and their uses.
First, CloudTrail records all console and API calls as events, including IAM and STS calls and use. CloudWatch can be used for real-time monitoring, including setting alarms when certain defined circumstances occur.
AWS IAM Access Analyzer, which helps keep track of all the resources shared with external identities. It identifies, automatically resolves, and alerts your team of an active finding (external access request)
6. Regularly Rotate Credentials
Rotating credentials regularly is good advice for both STS (that does it automatically, assuming the token is short-lived enough) and regular credentials.
Don’t be one of those companies that use the same admin pass no matter who that admin is or who gives several people the same security token to keep down costs and make everything more 'streamlined and efficient.’ It may seem efficient—but it’s bad security hygiene.
Even if you’re sure there are no IAM gaps, rotate all your passwords and tokens regularly, fostering continuous security.
Treat STS tokens as carefully as you would any long-term credentials. No matter how short-lived, tokens should be kept private and not made available via logs, source repositories, or plain text in conversations.
7. Use External Identity Providers
Why should you worry about managing your users and their identities? If you have lots of them (or hope to have them), let someone else do that for you. Companies that excel in identity management have better tools and track records than those trying to reinvent the IAM wheel.
Some options are Microsoft, Okta, and Salesforce—but you need to check all your options, pricing, and features to see which service provider works best for your organization.
» Estimate your team's coding speed with the cycle time metric
Adopt a ‘Security First’ Outlook
STS was designed to give you all the benefits of the AWS granular role system but with greater security. Being able to offer access to people without an AWS account (like your users) and gain the ability to track their token use better is a great bonus.
Keep your access limited and only hand it to the people who need it when they need it to avoid creating security gaps in your system. This approach fosters the security-first mindset when incorporating AWS offerings into your team.
If you want an even more granular view of your entire CI/CD security health, Jit’s DevSecOps platform takes security automation one step further by orchestrating and automating various open-source security tools.
You can manage them all under one platform and identify and remediate vulnerabilities on the go with the help of enriched real-time findings. Explore more here.