CVE 2023-2033: What is it, and how to fix it?
Published April 8, 2024.

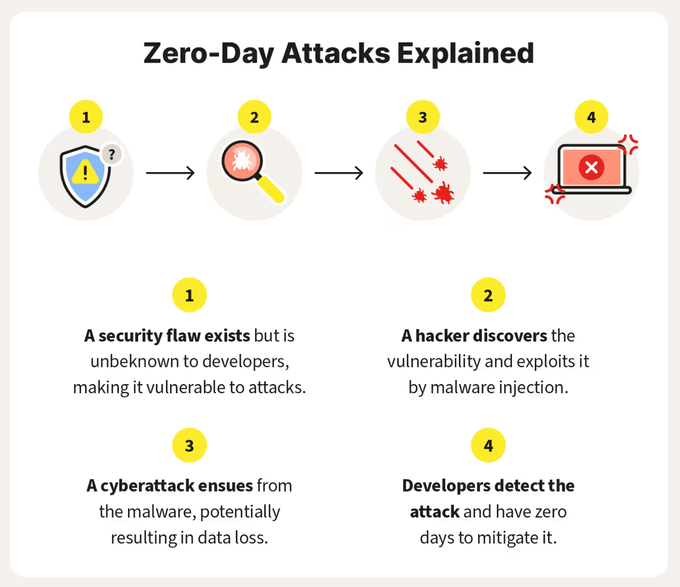
Zero-day vulnerabilities are the surprise no developer wants to get. Because these security flaws are unknown to developers, they have zero days to prepare or mitigate the vulnerability before an exploit can occur.
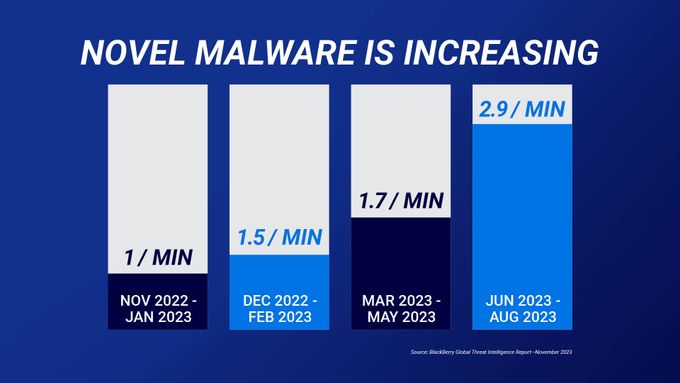
62% of vulnerabilities were first exploited as zero-day vulnerabilities, so they are far more prevalent than we think. Even Google Chrome can attest to that after discovering a series of zero-day vulnerabilities that left its billions of users at risk in 2023.
Among these was CVE 2023-2033, a zero-day threat that opened the Google Chrome doors to user data theft, malware propagation, financial loss, and legal ramifications.
What is CVE 2023-2033?
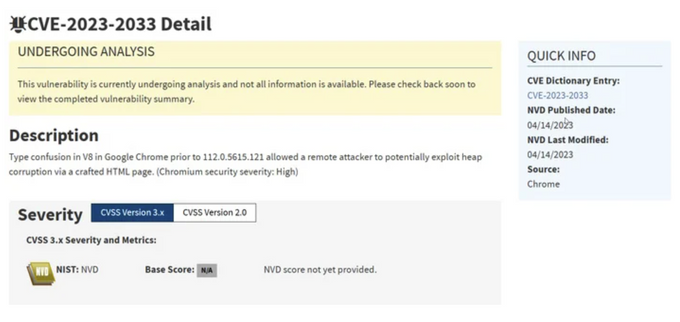
CVE-2023-2033 is a type confusion vulnerability that Google publicly disclosed on April 17, 2023. It resides within the V8 JavaScript engine, a critical component responsible for processing JavaScript code used by many applications.
This vulnerability allows attackers to bypass security measures and execute malicious code on a victim's device.
Its severity is underscored by the fact that it was actively exploited before a patch was available, classifying it as a zero-day threat. These zero-day threats are particularly dangerous as they expose users and systems to attacks until a fix is developed and released.
Quick discovery and patching of zero-day vulnerabilities is crucial, as vulnerabilities of this type could potentially compromise your sensitive data. Luckily, Google promptly addressed CVE-2023-2033, releasing a security patch (Chrome version 112.0.5615.121) on May 5, 2023.
CVE 2023-2033 exploitation and risks
Attackers could exploit CVE-2023-2033 in Google Chrome by tricking users into actions such as visiting malicious websites or opening booby-trapped email attachments. These seemingly harmless actions could trigger the vulnerability and grant attackers access to the victim's computer.
Tricking the user into visiting a malicious website could allow the attacker to execute malicious code designed to steal data, install malware, or take control of the system for cryptojacking.
By bypassing security restrictions, attackers could gain unauthorized access and move laterally within the compromised system, using it as a springboard to attack other devices.
The severity of this vulnerability was high due to its widespread exploitation, as attackers could develop various methods to exploit the vulnerability, potentially targeting a large user base.
Due to its zero-day nature, no patch was initially available, leaving users vulnerable until a fix was released.
How to fix the CVE 2023-2033 vulnerability
Fortunately, fixing the CVE-2023-2033 vulnerability and protecting yourself from its dangers is quick and straightforward.
The most crucial step is to update your browser to the latest version to ensure you benefit from the security patch that addresses the vulnerability. Head to the browser's settings menu and navigate to the update section to initiate the update process.
Once the update is complete, restart your browser to ensure the changes take effect. This step allows the updated version to load and fully implement the security patch.
What are the challenges of finding and fixing vulnerabilities like CVE-2023-2033?
1. Limited Information
The initial discovery of a zero-day vulnerability often comes from observing attack patterns or suspicious behavior.
This limited information makes it difficult to pinpoint the exact nature and location of the vulnerability within the code, hindering the investigation and delaying the patching process.
2. Stealthy Exploitation
Attackers often employ advanced techniques to evade detection, making identifying the vulnerability and its exploitation methods challenging. Such techniques involve obfuscating malicious code, using novel attack vectors like web spoofing or IoT botnets, or targeting specific systems to remain hidden for an extended period.
3. Short Window of Opportunity
The window between discovering a zero-day vulnerability and patching it is critically short. Security researchers must quickly analyze the vulnerability, understand its exploitability, and report it responsibly to the software vendor.
Simultaneously, developers must scramble to develop, test, and distribute a patch before attackers can further exploit the vulnerability.
4. The Trust Factor
Addressing zero-day vulnerabilities relies on responsible disclosure, where security researchers report the vulnerability to the software vendor privately instead of publicizing it.
This allows developers time to fix the issue before widespread exploitation occurs. However, this reliance on responsible disclosure can be risky, as there's always a chance the vulnerability might be leaked or discovered by malicious actors before a patch is available.
5. Need for Advanced Security Measures
Traditional security solutions are often insufficient to solve ever-complex zero-day threats. Teams must leverage more advanced cybersecurity controls and measures, such as:
- Behavior analysis and anomaly detection: These techniques can detect suspicious activities and potential zero-day attacks, even without specific signatures.
Endpoint detection and response (EDR) solutions: These tools can provide real-time visibility into potential threats and enable rapid response to security incidents.
- CI/CD pipelines with security testing: Tools like Jit can incorporate security testing across your CI/CD in a matter of minutes. This shift-left security approach helps you identify and address vulnerabilities before production.
How to protect against zero-day vulnerabilities
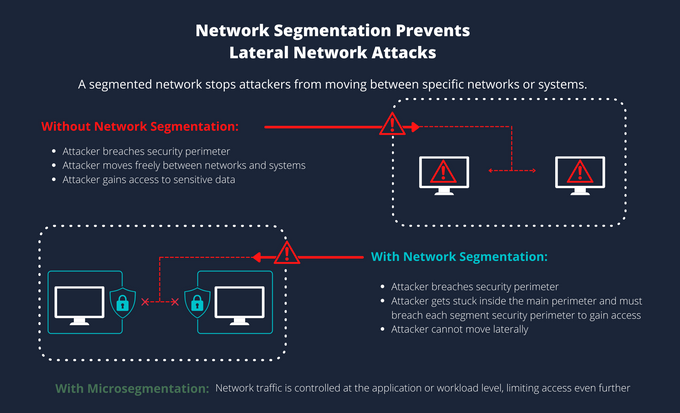
1. Network segmentation
Network segmentation involves dividing your network into smaller, logically isolated segments based on security requirements, functionality, or department. This approach minimizes the potential blast radius of a breach caused by vulnerabilities like CVE-2023-2033, preventing attackers from quickly pivoting across the entire network and accessing critical systems.
Here are some critical technical considerations for implementing network segmentation for zero-day protection:
- Micro-segmentation: Further subdivide segments for finer-grained control and further lateral movement restriction.
Access Controls: Restrict communication between segments based on the "need-to-know" principle.
Segmentation Firewalls: Enforce policies and restrict traffic flow with stateful firewalls, Web Application Firewalls (WAFs), and access control lists (ACLs).
Zero Trust Network Access (ZTNA): Continuously authenticate and authorize all access attempts regardless of their network location.
- Data Monitoring and Detection: Continuously monitor activity for suspicious behavior and deploy and implement intrusion detection and prevention systems (IDS/IPS) at segment boundaries.
2. Software Composition Analysis (SCA)
SCA scans can significantly reduce your attack surface. They analyze third-party open-source and commercial components used in your software development process to identify and address potential vulnerabilities before they become exploits.
Jit integrates and enhances powerful SCA security tools like OVS-scanner and NPM-Audit so you can automate them to run for every PR.
Plus, if you want to fortify your security plan and add other testing types like SAST, secrets detection and DAST, Jit can seamlessly connect these different security tools to your CI/CD so that you can implement and manage them all from one place with centralized monitoring.
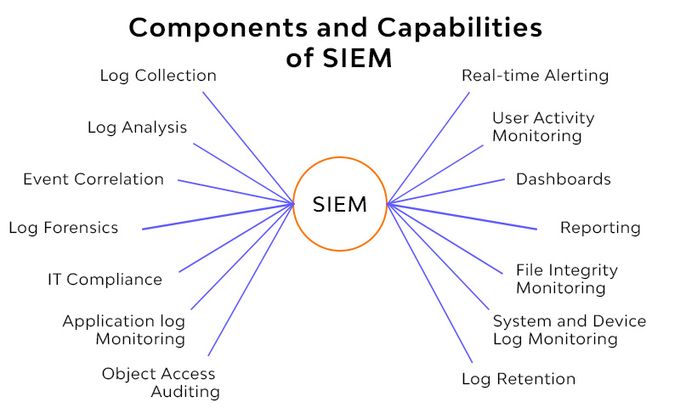
3. SIEM integrated with SCA
Integrate your Security Information and Event Management (SIEM) with your SCA tool. SIEM is a centralized platform that collects, aggregates, and analyzes security events from various sources across your IT infrastructure.
This capability enables you to identify and respond to potential security incidents effectively. For example, It can highlight activity caused by a malicious actor who is exploiting a CVE-2023-2033 vulnerability.
SIEM mainly watches your network for threats, and SCA identifies weaknesses in your software. Combining these two enables faster response, as when the SIEM sees suspicious activity linked to a known weakness (from SCA), it can alert you immediately. It also allows for better prioritization, as you can prioritize fixing vulnerabilities based on real-world threats, not just a list.
4. Prioritize Patch Management
Patch management involves the timely identification, acquisition, and deployment of security patches that address known vulnerabilities in software. Implementation steps in patch management include:
- Inventory and classification: Develop a detailed inventory of your organization's devices, software, and operating systems. Prioritize patching by classifying them based on criticality.
Vulnerability management: Regularly scan systems for vulnerabilities and prioritize patching based on factors like exploitability, severity, and potential impact on critical systems.
Patch acquisition and testing: Obtain security patches from trusted vendors and perform thorough testing in a non-production environment before deploying them to production systems.
- Deployment and verification: Deploy patches to all identified systems promptly and consistently. Verify successful patch deployment and address any deployment failures.
Tools like SCCM, WSUS, IBM BigFix, Ivanti, and Qualys can help you automate patch management. Also, whenever possible, enable automatic updates for all devices and software to minimize manual intervention and ensure systems are protected with the latest security patches.
5. Incident response plans
Develop a comprehensive and well-tested incident response plan specifically tailored to address zero-day vulnerabilities, incorporating these key elements:
Define roles and responsibilities for individuals and teams in the incident response process, including decision-makers, investigators, IT support, and communication personnel.
Implement intrusion detection and prevention systems (IDS/IPS) to identify suspicious activity.
Establish Communication Protocols for internal and external stakeholders during a security incident, specifying recipients, information, and communication methods.
Create a restoration plan to recover affected systems and data securely.
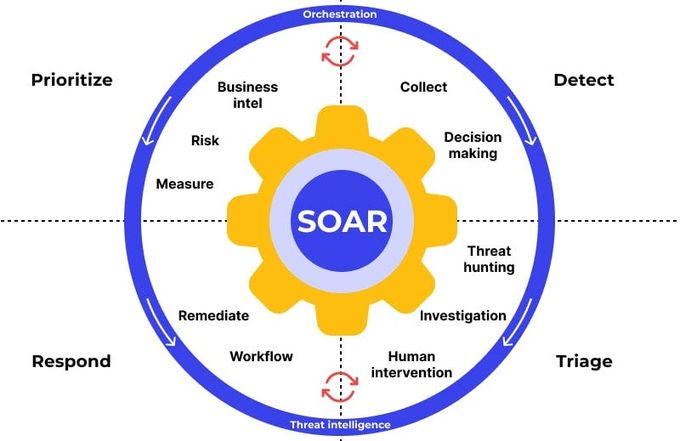
6. Security orchestration
Use security orchestration and automation (SOAR) platforms to automate routine security tasks and streamline incident response processes. These tools can help you:
Improve efficiency by automating workflows, streamlining incident response processes, and speeding up resolution times for CVE-2023-2033 and other vulnerabilities.
Reduce human error in repetitive tasks, leading to a more consistent and reliable security posture.
Enhance collaboration between security tools by connecting various security tools and sharing information seamlessly.
Protect Your Application From Zero-Day Vulnerabilities
Zero-day vulnerabilities like CVE-2023-2033, impacting millions of Chrome users, showcase the urgency for proactive security.
While patching is vital, organizations need a multi-layered defense that involves continuous monitoring, regular and integrated security assessments, and real-time vulnerability remediation guidance.
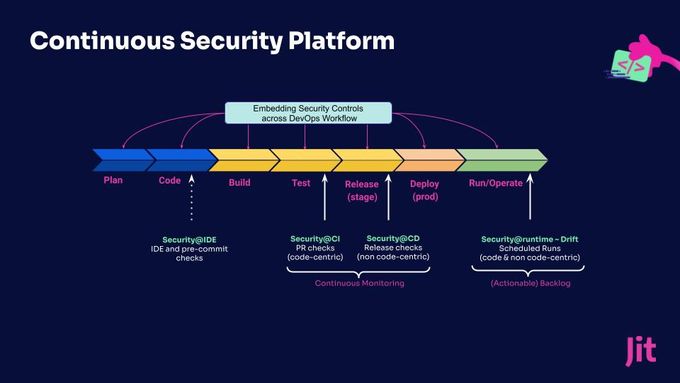
Jit’s DevSecOps platform allows dev teams to implement security tools and controls in their CI/CD, easily embedding and automating vulnerability scanning and detection across any pipeline stage.
Simplified security management enables developers to take a proactive approach to security without compromising code quality or development speed. Explore more about Jit here.