The Developer's Guide to DevSecOps Tools and Processes
Updated May 17, 2024.

How many security tools do you use daily? If you’re like 35% of developers, it’s probably too many for your liking. Building a DevSecOps toolchain is key to making DevSecOps a success and reaping all of its benefits. However, knowing where to start with so many different tools and processes can be overwhelming.
This article will explain the key DevSecOps tools and processes, while providing a guidance for building a software security program that works for you. We'll cover the different categories of tools you should consider and how to assess and improve your current processes.
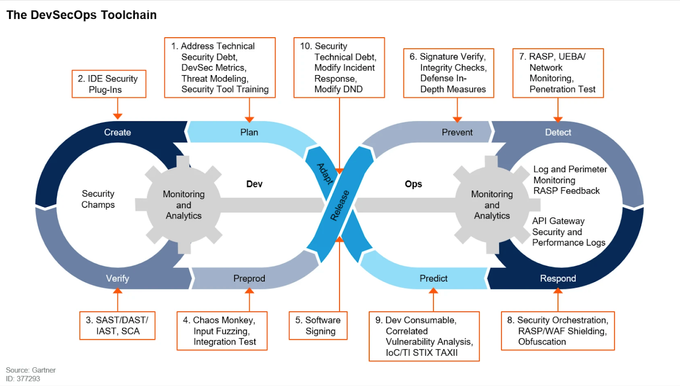
Debunking the DevSecOps Toolchain
The concept of a DevSecOps toolchain can be misleading, as it suggests that there is a single tool or set of tools that can address all security concerns throughout the software development process.
In reality, the DevSecOps tools comprises a range of tools specific to each stage of the development process, from code creation to deployment. These tools help to identify and mitigate security risks and are essential for ensuring the security and stability of your software.
There is no one-size-fits-all solution for DevSecOps. Different tools are needed for different stages of the development process, and the tools that a company chooses to implement will depend on its specific needs and resources.
Some popular technologies include static code analysis tools, web application scanning, and infrastructure-as-code scanners. Let’s explore them in more detail.
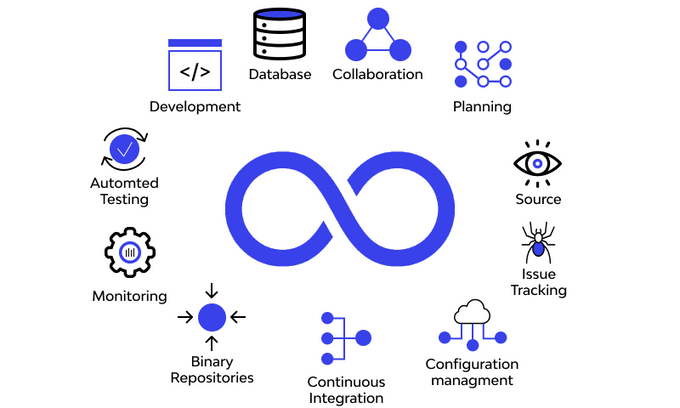
The Key Categories for DevSecOps Tools
DevSecOps tools can be broadly categorized into the following categories.
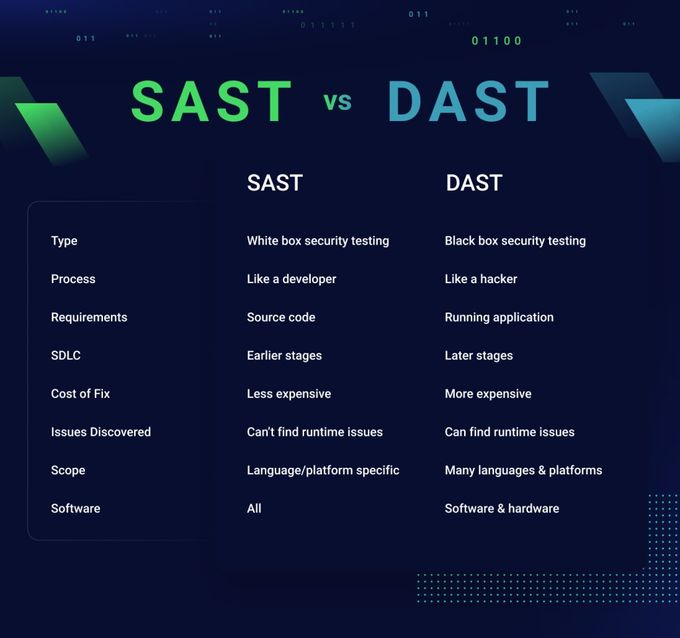
Static Application Security Testing
Static Application Security Testing (SAST) is a type of security testing that analyzes your source code for vulnerabilities and other issues without executing the code.
SAST is typically performed during development and can help you catch issues early on before they become more significant problems: a core pillar of DevSecOps processes. It also provides detailed information about the vulnerabilities found, including the specific lines of code where they occur.
One example of a SAST tool is Bandit. Bandit is a Python-specific tool that checks for various security issues, including insecure use of subprocesses and os calls, hardcoded passwords, and more.
- Pros: SAST is easy to integrate early in the SDLC, so software vulnerabilities can be surfaced and resolved before production. For those interested in automated security within their SDLC, a common first step is to implement SAST.
- Cons: all SAST tools will generate some amount of false positives. Consider tools that incorporate the context of your specific environment to help you prioritize which vulnerabilities matter most, like Jit.
Dynamic Application Security Testing
Dynamic Application Security Testing (DAST) is a type of security testing that analyzes your application for vulnerabilities and other issues while the app is running. DAST is typically performed after the application has been deployed in a real-world environment, and it tests not only the application but also any third-party integrations or dependencies.
One example of a DAST tool is OWASP ZAP (short for Zed Attack Proxy). OWASP ZAP is an open-source tool that can scan web applications for various vulnerabilities, including cross-site scripting (XSS) and SQL injection.
Note that while DAST can be considered black box security testing (a type of testing that doesn’t look at the internal workings of a system), this isn’t always the case. When authenticated, DAST can also be grey box and white box.
- Pros: DAST analyzes your application in runtime, so when it surfaces a vulnerability, there is a good bet its a true positive.
- Cons: rather than finding vulnerabilities early in the SDLC (like in the IDE or pull request), DAST can only surface security issues in runtime, which means developers need to figure out the root cause of the vulnerability and redeploy the service, which can be time consuming.
Secrets detection
Its self explanatory why you'd want to protect secrets like passwords and API keys, but sometimes secrets are accidentally hardcoded, which can leave them exposed to hackers. There are great open source tools available to automate the task of scanning your code for hardcoded secrets early in the SDLC, so you can catch them before production.
We recommend open source secrets detection technologies like Gitleaks and Trufflehog for the task, which are free to use.
- Pros: open source libraries make up the bulk of many modern applications, so SCA can provide broad coverage of your application security.
- Cons: like the other tools described in this post, secrets detection tools scans code and lists potential vulnerabilities in a backlog outside of the PR or IDE, which can take developers out of their flow state and overwhelm them with findings that aren't related to their current change. Some technologies can provide easier DevSecOps processes for developers to adopt. For example, Jit can provide secrets detection (alongside the other tools described in this post) entirely within the IDE or PR, so developers never need to leave their environment.
Open-source vulnerability scanning (SCA)
Open-source vulnerability scanning tools - also known as Software Composition Analysis - can help you identify vulnerabilities and other issues in your open-source dependencies. These tools typically work by identifying the dependencies your code is using and determining whether they introduce any known vulnerabilities or issues.
Some examples of open-source vulnerability scanning tools include OSV-Scanner and npm-audit. Jit can help you easily integrate open-source vulnerability scanning tools into your development process, making it easier to identify and fix vulnerabilities in your open-source dependencies.
- Pros: open source libraries make up the bulk of many modern applications, so SCA can provide broad coverage of your application security.
- Cons: many SCA tools rely on the National Vulnerability Database, which documents which vulnerabilities exist within specific open source components. Many of these vulnerabilities don't contain much remediation guidance, which can leave developers unsure of how to fix the issue. Tools like Jit, can provide auto remediation for such vulnerabilities, so developers can quickly solve the issue.
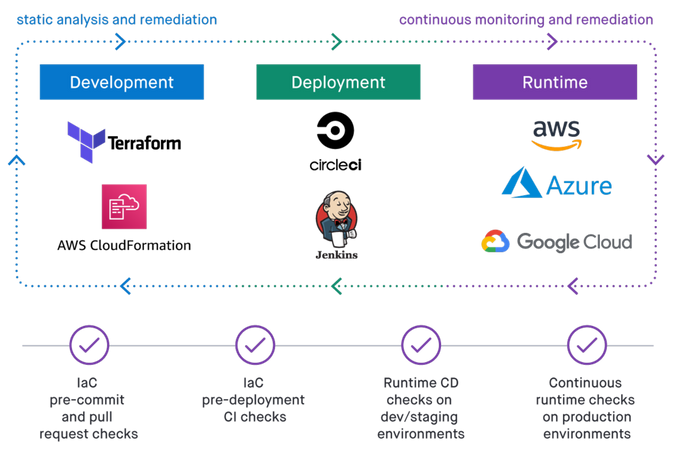
Infrastructure-as-code (IaC)
Infrastructure-as-Code (IaC) is a practice that involves using code to manage and provision your infrastructure. It can include everything from servers and storage to networks and load balancers.
Using code to manage your infrastructure ensures that your environments are consistent and that changes are predictable and controlled. Infrastructure code can serve as documentation for your environment, making it easier for new team members to understand how things are set up. Multiple people can seamlessly work on the same infrastructure codebase using version control and other tools.
Some examples of IaC tools include Terraform, CloudFormation, and Ansible. Some open-source tools can also help you scan your infrastructure code for issues, such as Checkov and KICS.
Learn about the benefits of using IaC scanning to fix security misconfigurations early in the SDLC in the video below:
- Pros: IaC scanning surfaces potential cloud misconfigurations before the change is actually made, which makes it fast and easy to fix security issues in your infrastructure.
- Cons: the nature of IaC scanning is to surface vulnerabilities in static IaC files, which will miss vulnerabilities caused by configuration drift, or other issues caused by infrastructure changes made in the CLI or the cloud console.
Observability and monitoring
DevSecOps tools can also include observability and monitoring technologies. These tools help you understand what's happening in your system, identify issues as they arise, and take corrective action promptly.
Using tools like Security Incident and Event Management (SIEM), you can better understand what's happening in your system and get notified when something goes wrong. Real-time alerts allow you to take corrective action before issues have irreversible consequences. With tools like distributed tracing, you can identify the root cause of bugs and fix them more quickly without impacting the app’s functionality.
- Pros: real time visibility into the user behavior in your system is needed to surface ongoing attacks.
- Cons: to understand user activity in your environment, you'll need to capture telemetry data generated from your system that describes system events and performance metrics. This can be technically complex, and often requires code changes.
DevSecOps processes to enable strong developer adoption
If you're looking to improve the security and stability of your software, adopting DevSecOps tools is a great place to start. But how do you begin? And how do you ensure that these tools are actually embraced by your developers in their day-to-day routines?
We'll break down some essential steps and DevSecOps processes to answer these questions.
Accessing your current processes
Before improving your security processes, you must know where you stand. Assess and audit your current processes to identify weaknesses and areas for improvement.
If you're looking for a fast way to understand which vulnerabilities are prevalent throughout your codebase (i.e. hardcoded secrets? SQL injections? Vulnerabilities in your open source components?), you can activate Jit within your GitHub account. This will automatically implement DevSecOps technologies across your repos in minutes, and scan each one.
This assessment will give you a baseline from which to work and allow you to prioritize your efforts. Some things to consider when accessing your current processes include the following:
- How are security concerns addressed in your current strategy?
- Are there any bottlenecks or inefficiencies in your current plan?
- Are there any security tools or practices that you're currently not using but might be beneficial?
By answering these questions, you'll better understand your current security posture and be better equipped to make improvements.
Automate, automate, automate
Once you have a handle on your current DevSecOps processes, the next step is to start automating as much as possible. Automation can help you streamline your security processes and make them more efficient. Some benefits of automation include the following:
- Reducing the risk of human error
- Allowing you to scale your security efforts more easily
- Freeing up your team to focus on more critical tasks
There are several different ways you can automate your DevSecOps process, like integrating security scanning for each PR or scanning your runtime environment after each deployment.
Learn about automating security processes in the SDLC below:
Create a security plan that works for you
There are many different categories of tools to consider, each of which serves a different purpose. Start with your requirements - such as gaining compliance with a specific set of standards or meeting customer requirements - and work backwards from there.
You can also use prebuilt and codifed Security Plans that are custom-made for specific use cases, and can be implemented across your repos quickly. They include all the technologies needed for your objective, as well as all of the automations and integrations needed to implement the plan.
Adopt the right tools: Embrace the Power of DevSecOps with Jit
DevSecOps tools and processes can significantly improve the security and stability of your software. Following the steps outlined in this guide, you can build a program that works for your team and will help you deliver better software.
Whether you're just starting out or looking to take your security efforts to the next level, Jit can make integrating and managing your security tools a breeze. Don’t just take our word for it. Start building your toolchain today and see the benefits for yourself.