Kubernetes Security Posture Management: 7 Essentials to Know
Updated November 5, 2024.

Kubernetes offers unprecedented flexibility and scalability in deploying and managing modern applications. However, securing K8 clusters has become a significant challenge for developers.
Over half of Kubernetes users reported security incidents in the past year. The most recent example was the Google Kubernetes Engine (GKE) vulnerability discovered by cybersecurity firm Palo Alto Networks. This vulnerability involved potential security threats in FluentBit and Anthos Service Mesh (ASM) within GKE. When these vulnerabilities were chained together, they could lead to an attacker's complete takeover of a Kubernetes cluster.
If even Google isn’t immune to vulnerabilities, how sure can you be that your clusters are secure? Kubernetes Security Posture Management is an essential first step toward measuring and improving the security of your cloud infrastructure and applications.
What is Kubernetes Security Posture Management?
Kubernetes Security Posture Management (KSPM) is a strategy that ensures the security and compliance of Kubernetes resources. It focuses on four key areas:
- Configuration: Setting up and managing Kubernetes resources securely and efficiently. This includes scanning Kubernetes configuration files to avoid security misconfigurations, such as ensuring that Kubernetes pods are not running as root. It also involves enforcing least privilege access and protecting sensitive data by implementing secrets management strategies, like using Kubernetes Secrets or third-party tools like HashiCorp Vault.
- Policy management: KSPM enables policy enforcement, as you can set and apply security rules for Kubernetes resources and fix errors or breaches.
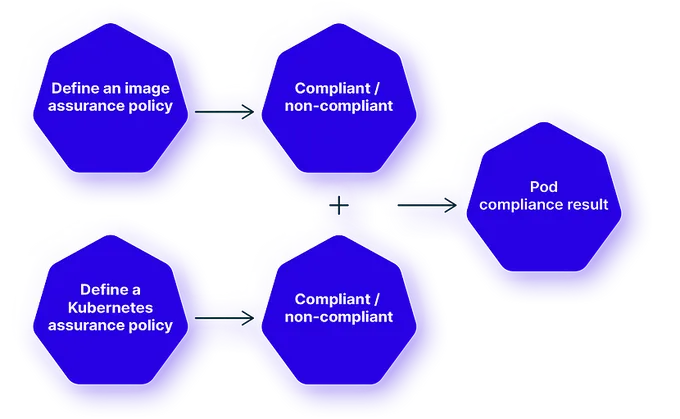
- Compliance: Following the rules and standards for Kubernetes environments. This involves auditing and validating Kubernetes configurations and activities against benchmarks and frameworks like CIS Kubernetes Benchmark or NIST SP 800-190.
- Surface vulnerabilities in containers: Addressing the risk of attacks targeting Kubernetes resources. This area involves scanning and patching Kubernetes images, containers, and code to identify and mitigate vulnerabilities.
- Runtime threat detection: This area refers to the ongoing operation and performance of Kubernetes resources, including monitoring and detecting anomalous or malicious activities.
In contrast to Cloud Security Posture Management (CSPM), which leverages cloud security tools and processes to protect a wide range of cloud environments, KSPM is a more focused approach explicitly tailored for Kubernetes. It zeroes in on these four criteria to ensure high security and compliance for Kubernetes clusters.
Why do you need Kubernetes Security Posture Management?
The increasing complexity and scale of Kubernetes clusters and their dynamic and declarative nature introduce novel security risks. For instance, Kubernetes’ default configurations often prioritize ease of use over security, leaving clusters exposed if not correctly configured.
Additionally, the ephemeral nature of containers can lead to security blind spots. Misconfigurations, such as overly permissive access controls or exposed dashboards, are common and can lead to severe breaches.
Kubernetes Security Posture Management (KSPM) is essential for any organization that uses Kubernetes for its cloud-native applications. You can check and report Kubernetes compliance status against relevant regulations such as GDPR, HIPAA, and PCI DSS. Automating compliance can help you ensure a solid compliance posture, strengthen your reputation and credibility in the industry, and avoid hefty fines.
KSPM also enables you to detect and respond to attacks or exploits targeting Kubernetes resources. Getting real-time alerts will aid you in ruling out an efficient incident response workflow, minimizing damage, and quickly restoring your Kubernetes environments.
Overall, KSPM allows you to optimize Kubernetes workloads, improving resilience, efficiency, and scalability. It seamlessly integrates with CI/CD pipelines, enhancing development and deployment processes. Ensuring security checks are performed after every deployment reduces the risk of deploying insecure applications.
How does Kubernetes Security Posture Management work?
KSPM is about identifying and managing the security risks associated with Kubernetes deployments. Its key components are:
Continuous discovery: Identifying and cataloging Kubernetes assets, including clusters, nodes, pods, and configurations. This process helps maintain a current view of the infrastructure landscape.
Configuration management and policy enforcement: Ensuring that all Kubernetes configurations adhere to security best practices and comply with regulations to minimize the risk of configuration-related vulnerabilities while flagging config files that don’t adhere to defined security policies.
Security visibility: Detailed view of the Kubernetes environment's security status, discovering potential weaknesses or breaches.
Compliance monitoring: Continuously monitoring against standard industry benchmarks, such as the CIS Benchmarks. It ensures ongoing compliance and quickly detects deviations or non-compliance.
Detection and Response: This involves monitoring Kubernetes API server audit logs, which record all activities and interactions within a Kubernetes cluster. Anomalies or malicious activities, such as unauthorized access attempts or unexpected changes in configurations, can be detected, and alerts can be generated. This allows for immediate response to potential threats, minimizing the impact and ensuring the security of the Kubernetes environment.
DevSecOps Integration: Integrating security into the development and deployment pipelines ensures that security scanning and remediation becomes a natural and embedded flow within the entire application lifecycle.
Kubernetes Security Posture Management: 7 Essentials You Need to Know
1. API Server Access Control
API Server Access Control involves managing who can access your Kubernetes API server and what actions they can perform. It's like the control panel of your cluster, and securing it is critical for cluster security.
Firstly, implement Role-Based Access Control (RBAC). Use YAML files to define roles and role bindings easily in Kubernetes.
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:namespace: defaultname: pod-reader
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "watch", "list"]
Customize the actions that need to be logged by editing the audit-policy.yaml file.
apiVersion: audit.k8s.io/v1
kind: Policy
rules:
- level: Metadata
resources:
- group: "" # Empty string indicates the core API group
resources: ["pods", "secrets"]
You should restrict API server access using network policies or WAF for Kubernetes. These security solutions enable you to only allow traffic from trusted sources.
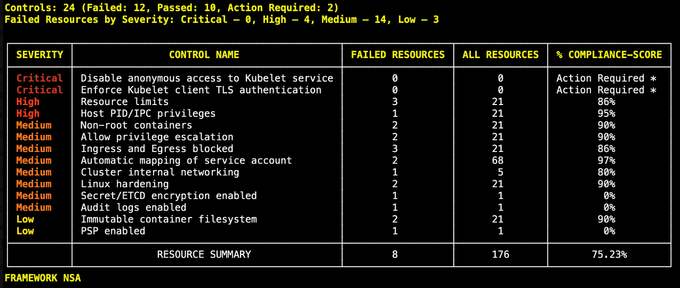
Lastly, you can use Kubescape to assess and improve these configurations. If you have Kubescape installed, you can quickly run a scan using the below command:
kubescape scan framework nsa --exclude-namespaces kube-system,kube-public
2. Pod Security Policies (PSP)
Pod Security Policies (PSP) control the security specifications that pods must meet in a Kubernetes cluster. Implementing PSPs helps prevent the deployment of vulnerable or malicious pods. Tools like Open Policy Agent (OPA) Gatekeeper can automate the management of these policies.
Use YAML to create PSPs tailored to your operational needs, like restricting privileged containers or access to host resources. Continuously update PSPs to adapt to new security challenges and organizational changes.
apiVersion: policy/v1beta1
kind: PodSecurityPolicy
metadata:
name: example
spec:
privileged: false # Disallow privileged containers
volumes:
- 'emptyDir'
hostNetwork: false
hostIPC: false
hostPID: false
runAsUser:
rule: 'MustRunAsNonRoot'
3. Network Policies
Network Policies allow you to control the traffic flow between pods at the IP address or port level. You can restrict which pods can communicate with each other, thereby limiting the potential impact of a compromised pod. Tools like Cilium’s NetworkPolicy can automate the creation and management of these policies.
Start with a default deny-all ingress and egress policy, then allow specific traffic as needed. Ensure you define detailed policies for different services to isolate them and minimize breach impacts.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny-all
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
4. Image Security
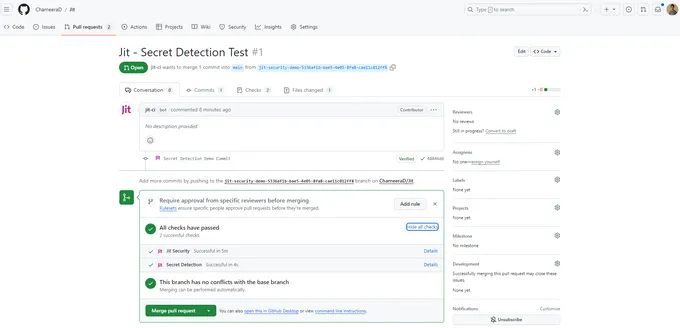
Securing container images is essential to prevent the deployment of containers with vulnerabilities or malicious code. You can leverage open-source tools like Trivy to scan container images and identify potential security threats. With Jit, you can seamlessly integrate Trivy into your CI/CD pipeline and automate it so that it runs for every PR.
Make sure to update images with the latest patches and use registries that support image scanning and signing to ensure image integrity.
5. Secrets Management
Kubernetes Secrets Management is crucial to securely store and handle sensitive data such as API keys, passwords, and tokens. It ensures these critical authentication elements are shielded from unauthorized access, maintaining the security of the K8 environment.
You can use specialized secret management tools like AWS Secrets Manager, Google Secrets Manager, and Azure Key Vault to store and manage secrets. While developers should avoid hard-coding secrets by retrieving them dynamically in their applications, secret managers can catch secrets that fall through the cracks.
You can use Jit’s integration with GitLeaks to automate GitLeaks secret scans and identify such flows in your codebase as developers write their code. Lastly, implement policies for regular secret rotation to enhance security.
6. API Server Hardening
Hardening the API server in Kubernetes minimizes the attack surface and ensures it can resist various cyberattacks.
Disable unnecessary features and endpoints using feature gates and admission controllers to control which Kubernetes features are enabled. Then, configure audit logs to track all activities and use admission controllers like PodSecurityPolicies and OPA/Gatekeeper to enforce security policies at the API level.
Ensure that audit logging is configured correctly to capture detailed information about API requests. The audit policy example logs detailed request and response data for pod and secret resources (Security Incident and Response (SIEM) tools can help aggregate these logs to investigate malicious activity).
apiVersion: audit.k8s.io/v1
kind: Policy
rules:
- level: RequestResponse
resources:
- group: ""
resources: ["pods", "secrets"]
7. Runtime Threat Detection
Runtime threat detection involves monitoring applications in real-time in Kubernetes environments to detect and respond to threats as they occur.
You can leverage DAST tools like ZAP to thoroughly assess the security of your running application. Jit can integrate ZAP seamlessly into your CI/CD for continuous security testing. It also offers real-time alerts and notifications, providing detailed insights into any discovered vulnerability.
ZAP is notoriously difficult to configure and deploy – consider Jit’s ZAP configuration wizard to simplify the onboarding process.
Elevate Your Kubernetes Security with Jit
Within the last few years, KSPM has become more than a set of best practices. Now, it's non-negotiable for the security and efficiency of your Kubernetes deployments. However, as you may have gathered from this article, KSPM processes can get complex.
Jit’s DevSecOps platform offers a complete ecosystem of tools and controls to improve the security of your Kubernetes clusters. For example, it supports Trivy for image scanning, ZAP for real-time threat detection, and Kubescape to automate scans of existing K8S manifest files and every newly created PR. Plus, it integrates with all the major cloud services and version-controlling providers. Explore Jit here and start simplifying your K8 security.