npm audit fix - Taking Node.js Security to the Next Level
Updated June 7, 2024.
At Jit, we love npm audit and its excellent capabilities, and have delved into some good practices for how it works under the hood. For those who are unfamiliar, npm audit is a best of breed OSS tool for the Node.js ecosystem, built to safeguard code against potential vulnerabilities. One of the great features that comes out of the box with npm audit, is the auto-remediation feature called npm audit fix. In this post, we’ll take a closer look at npm audit fix—that not only identifies security issues within your project's dependencies but also provides automated solutions to intelligently remediate these issues based on predefined criteria.
Understanding npm audit fix
When it comes to managing dependencies in a Node.js project, the package.json file serves as a blueprint, outlining the required packages and their respective versions that need to be used in order for your applications to properly run in production. Like many other programming languages, this comes with an additional and critical file called the package-lock.json file that further enriches this with metadata about these packages by detailing sub-dependencies—essentially, the dependencies of dependencies (what is also called your third-party supply chain - and where popular SCA scanning tools have been focusing their efforts).
This interdependency and hierarchy ensures that your project and applications function properly. The tight coupling though does introduce some complexities when it comes to security auditing. npm audit fix operates by analyzing both the package.json and package-lock.json files, comprehensively scanning for vulnerabilities within all dependencies, including sub-dependencies. Upon identifying security issues, npm audit fix employs semantic versioning constraints (which we will get to shortly) to automatically resolve them. Without constraints it will automatically upgrade vulnerable packages to safer versions and update the lockfile accordingly.
One of the key strengths of npm audit fix lies in its ability to autonomously address security vulnerabilities. By adhering to semantic versioning principles, it ensures that fixes are applied in a manner that preserves compatibility with your project's existing codebase. It also provides these fixes within developer’s native workflows, further simplifying auto-remediation and version patching.
How npm audit fix Handles Version Constraints
The great part of npm audit fix, being an OSS tool, that is community-driven, it’s understood by all developers that not all fixes and version upgrades can be made on a whim. Some of these introduce breaking changes, and require greater consideration than an auto-remediation tool will have the proper context for. That is why users have the flexibility to define constraints regarding major, minor, or patch updates, enabling granular control over the remediation process.
In scenarios where a fix is available in a subsequent major version, but constraints disallow major upgrades, npm audit fix will provide a workaround. By running `npm audit fix --force`, users can prioritize issue resolution over version constraints, effectively bypassing restrictions to address critical vulnerabilities promptly, when this is needed and with developer discretion.
How We Implement npm audit fix at Jit
At Jit, we prioritize security by utilizing npm audit to scan for vulnerabilities within dependencies. However, our approach extends beyond mere scanning—we generate a comprehensive lockfile that accurately reflects the dependencies and versions utilized in production environments. This ensures that our users receive the most accurate results, minimizing discrepancies between development and production environments.
In addition to supporting public packages, Jit also caters to projects utilizing private dependencies. By integrating with npm registry and other platforms like GitHub registry, we facilitate seamless version updates for private packages. This ensures that even proprietary codebases benefit from the security enhancements provided by npm audit fix when using Jit.
npm audit fix in Action
Below we’ll dive into a concrete example of npm audit fix works, with real code examples, so you can see it in action.
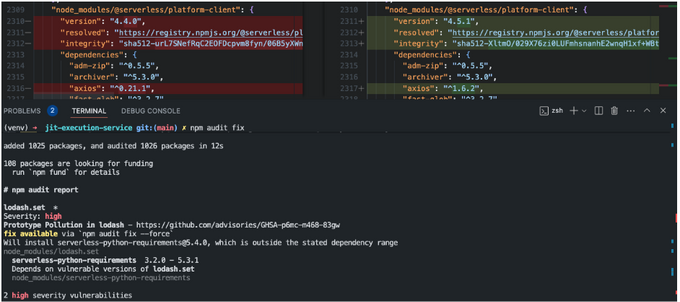
In the example below we can see the usage of ‘npm audit fix’ which upgrades the minor version of ‘@serverless/platform-client’ along with ‘axios’, a sub-dependency of it, in order to fix a security issue.
Note how it suggests the use of the –force flag, in order to fix another issue in ‘serverless-python-requirements’ which is outside of our semantic versioning range. This is because the upgrade is considered a Major version upgrade which was disallowed in the constraints, that may break certain functionalities
Check Out npm audit fix
In an era where cybersecurity threats are in every OSS package and evolving in complexity, proactive measures are going to continue being one of the important methods to safeguard software and instill application security during coding. npm audit fix is an excellent tool to have in your arsenal, as a Node.js developer, offering an in-developer workflow and native approach to identifying and resolving security vulnerabilities within dependencies. By integrating npm-audit into the Jit platform and augmenting its capabilities to align with development workflows, we prioritize the security and integrity of Node.js codebases, empowering developers to be more security-minded and build more robust and resilient applications from the first lines of code.