What the Heck is SSDLC (Secure Software Development Lifecycle), and why should devs care?
Updated September 17, 2024.

When we sit down to code, most of us are more concerned with functionality, speed, cost, and of course, making sure it works. But securing your development process is beyond just a ‘nice-to-have.’
Security is more than ensuring all your input data is sanitized at the end of the development process. If you don’t make it an integral part of your entire process, you might deliver a product with security vulnerability that open up injection or malware and backdoors.
This article will examine how the new SSDLC integrates into your current development life cycle and why you should care about it. Plus, we will leave you with some best practices and practical methodologies for integrating security into the development process, no matter how small or complex your project is.
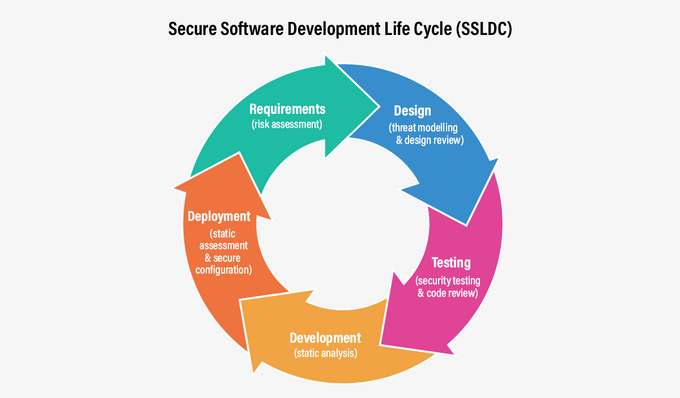
A Brief Overview of the SSDLC
The end goal of software development is to produce high-quality software. Over time, the process has been codified into phases. To ensure software development lifecycle security, you can implement security considerations and technologies to prevent potential vulnerabilities at each stage of the SDLC.
- Requirement analysis: If you need to meet specific compliance needs or security demands for customers, this stage required decisions around which technologies are needed to surface vulnerabilities that would violate your requirements.
- Planning: who is going to own the security requirements defined in the requirement analysis stage? How will they be implemented into the SDLC?
- Software architectural design: this is where you can make decisions around secure software architecture using these seven principles of secure software design.
- Software development and continuous integration: to shift security left, consider integrating tools like SAST, SCA, and secrets detection into your SDLC to surface vulnerabilities before they make their way into production.
- Testing: remember when quality testing was its own department? Now it feels like a part of the SDLC - security testing should feel the same way.
- Deployment: You can configure tools like CSPM or DAST to scan your environment after each deployment, which can catch vulnerabilities that may have slipped through the cracks earlier in the SDLC.
You may find yourself iterating through some of the phases more than once or in a different order (possibly in parallel). Still, this process would take you from an idea to deploying a solid working software product.
In the old days, securing the software was mainly the prerogative of the testing team (QA). They would examine the functionality and code to see if they breach security concerns (or break in general). Before and after deployments, the security team would review the application to ensure it met all security requirements.
The problem with this approach is that it leaves security in the hands of just a few key people who aren't directly responsible for delivering code. That means checking for security concerns may become a bottleneck for continued development. This process almost guarantees that the code would go back to development at least once for the dreaded refactoring, meaning that the project would take longer and cost more.
What does a Secure Software Development Lifecycle (SSDLC) encompass?
The idea behind secure software development is to embed security concerns into every process stage rather than just leaving it in one phase. Continuous security is present when you consider the project requirements, map out the design, the various building blocks and infrastructure needed, and sit down to write the code.
The strategy of spreading out security concerns across the entire development process and involving the developers in both the planning and implementation of security is called shift-left.
For developers who have never given security concerns much thought, the idea that it’s suddenly part of their responsibility may be daunting. Breaking the requirements into several well-defined best practices makes it much more manageable. It’s just like learning to use a new development tool.
Jit allows developers to define security requirements as code over their entire tech stack. Once you determine these requirements, Jit ensures they are continually kept.
Best practices for software security
Let’s look at a few security best practices that can help you maintain a secure code base and are easy to incorporate into your day-to-day development process.
1. Code reviews
Code review is about reviewing source code to identify potential security issues, coding errors, and other software defects. Code reviews are usually conducted by a more experienced developer than the one who wrote the code.
They can help ensure that the application is secure and the code is high quality. They also help maintain a unified standard and coding conventions (like variable and function names) across the entire code base.
It is considered a best practice to only merge code into the main branch with at least two sets of eyes having looked it over. The first set of eyes is, of course, the developer who wrote the code.
Even very experienced developers, including team leaders, can benefit from their code being reviewed by someone else.
2. Testing
You don’t need us to tell you how vital testing your code is to address security issues before they become a problem. Since most code projects are complex and interdependent, there is no way to predict how even a tiny gap might affect the code base security down the line.
When you write automated tests, consider the functionality of the piece you have just written and how it interacts with any other relevant part of the code base, both in the front and back end.
Security issues traditionally covered in testing could include vulnerabilities such as SQL injection, cross-site scripting, insecure data storage, or insufficient memory allocation (which could lead to Buffer overflows). Testing should also cover memory leaks, poor or slow performance, or usability issues.
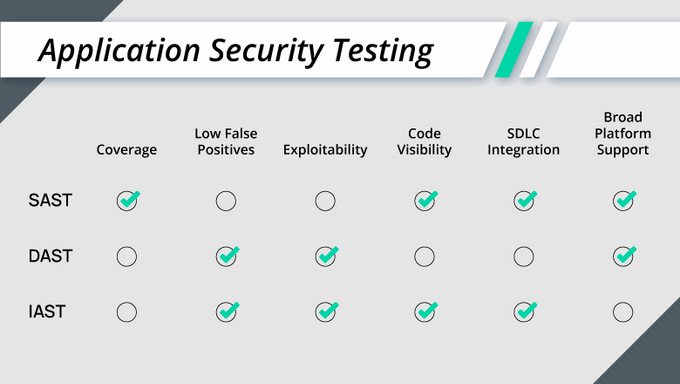
3. Scanning
Several kinds of scanning can be employed to increase the overall security of your code. These include static analysis, dynamic analysis, and interactive analysis.
Static analysis scans source code to identify potential security issues or obvious coding errors.
You can use static analysis to check for coding standards violations, insecure coding practices, and potential vulnerabilities. Since it only reviews the code’s syntax, it doesn’t account for anything that happens at run time.
Dynamic analysis scans the application while running to identify potential security issues, coding errors, and other problems. You can use it to spot memory leaks, poor performance, and potentially breaking inputs or processes.
Note that this kind of testing is done at a specific time with particular inputs, so the tests are only as good as the people who designed them. The goal is to find the problems before your users do.
Interactive analysis scans the application by interacting with it to identify potential security issues and other breaking defects. It can check for user interface issues, usability issues, and potential vulnerabilities.
Not all types of scanning fit all kinds of applications, so you must match the type of tests required to the code you wrote and its intended functionality.
4. Training
Part of the problem for many developers is they feel they are not sufficiently familiar with potential security issues and wouldn’t think to prevent them in advance or scan for them later.
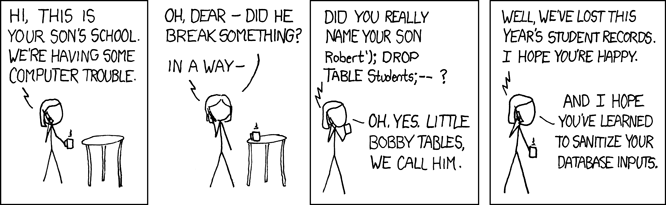
Most developers know that allowing unsanitized input data into your backend could lead to remote code activation - like the famous kid named ‘drop tables.’
However, not as many would know how to test for buffer overflow or check for vulnerabilities in transient dependencies.
Training helps developers fill in these knowledge gaps. The more developers know about security issues and potential vulnerabilities, the better suited they are to incorporate these concerns into their day-to-day coding and testing.
Why should developers care about SSDLC?
There are quite a few benefits to spreading the responsibility for creating secure code among all the development process participants, including the developers.
When everyone is security-aware and alert, more problems are caught earlier in the development process. It’s far better to be aware of issues earlier than wait for the tester or security expert to look for them.
Some problems caught in a later stage are already so entwined in the system that it’s almost impossible to root them out without extensive redesign, adding potentially substantial costs and time to your project.
With the developers actively scanning and fortifying their code, there would be less refactoring, reducing overall development costs and causing fewer roadblocks for planned release times.
Including automation in the process would make it easier and faster for the developers involved.
Make your development process more secure
Developers WANT to make their code more secure. Most developers wouldn’t intentionally write bad, buggy, or breachable code.
The lack of knowledge, tools and proper processes usually stops them from taking full ownership of the security of their code and the whole development process.
When planning, designing, development, and testing are done with the addition of code security lenses, the entire software development ecosystem benefits.
Working with the SSDLC methodology is more secure, cost-effective, faster, and agile than leaving security for last. And Jit makes it easier than ever to implement it by enabling you to embed security tools and controls for all layers of your app. Give Jit a go and start for free.