A Step-by-Step Guide to Using Kubescape to Protect Kubernetes Containers
Updated November 5, 2024.

Kubernetes has taken the tech world by storm. It is an innovative and powerful platform for container orchestration, enabling organizations to streamline the deployment, scaling, and management of their applications. But nothing in the tech world is immune to security attacks, and Kubernetes has seen its fair share of vulnerabilities.
According to a recent report, 93% of respondents experienced at least one Kubernetes-related security incident within the prior 12 months, and 31% suffered revenue or customer loss. Common security challenges range from misconfigurations to node, API, and data vulnerabilities.
To help you navigate this treacherous terrain, we’re discussing Kubescape, an invaluable tool to protect your Kubernetes Containers, and show you how to use it to monitor your Kubernetes’ security.
We'll also discuss ways Jit can automate the process of deploying Kubescape, while implementing continuous scanning so every code change is analyzed for Kubernetes misconfiguration issues.
What is Kubescape?
Kubescape, created by ARMO, is a powerful tool designed to protect Kubernetes containers by ensuring they adhere to security best practices and remain compliant. Its popularity has coincided with the rise of Kubernetes and the importance of Kubernetes Posture Management.
Its primary purpose is to analyze Kubernetes deployments against a predefined set of rules, known as the Kubernetes Hardening Guide, but you can also set your custom policies. Here are some key things to know about this technology:
- Designed to catch newly introduced vulnerabilities in your K8s configs: Kubescape can also help you improve performance metrics such as Mean Time to Detect (MTTD) and Change Failure Rate, strengthening your overall security posture. Jit now supports Kubescape - so you easily integrate this tool into your workflows and automate scans across various software lifecycle stages.
- Easy integration and reporting: You can integrate Kubescape with existing Continuous Integration/Continuous Deployment (CI/CD) pipelines and manually scan code or automatically trigger scans through IDE integrations. The results can be exported in various formats, such as JSON or HTML, allowing seamless integration into your existing reporting and auditing processes.
- Mature and widely used: Earlier this year, the Cloud Native Computing Foundation (CNCF) accepted Kubescape as a sandbox project. This recognition signifies that Kubescape is seen as a valuable addition to the CNCF ecosystem, aligning with its mission to foster and advance the adoption of cloud-native technologies.
How Kubescape works
Kubescape analyzes your Kubernetes deployment configurations against the Kubernetes Hardening Guide.
This guide is based on NSA and CISA guidelines, providing a comprehensive set of controls designed to help protect your Kubernetes infrastructure. The rules are divided into four main categories, each addressing specific areas of concern:
- Access Control ensures that authentication and authorization mechanisms within your Kubernetes clusters are correctly configured, limiting unauthorized access to your resources.
- Network Policies aim to establish proper network segmentation and isolation, preventing unauthorized access to sensitive data and services within your cluster.
- Pod Security helps enforce the principle of least privilege, limiting the capabilities of running containers to the minimum required for their intended function.
- Auditing and Monitoring improve the visibility and tracking of security-related events, enabling timely detection and response to potential threats.
Incorporating Kubescape into your security strategy complements other essential practices, such as Web Application Security Testing, ensuring comprehensive protection against various threats.
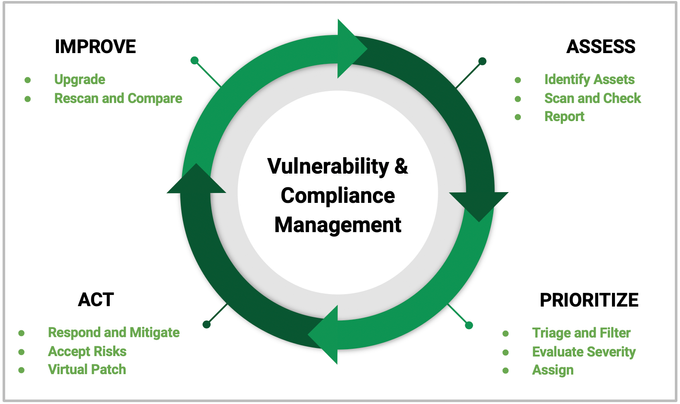
Using Kubescape to protect Kubernetes Containers
This short tutorial takes you through the end-to-end process of running Kubescape to effectively track security improvements and ensure your Kubernetes environment remains secure and compliant with the Kubernetes Hardening Guide.
If you're looking to automate this process and optionally unify Kubescape with other product security tooling like SAST, IaC scanning, and open source security, Jit can roll out these technologies across your repos in minutes.
Step 1. Initial setup
Before using Kubescape, you must install the Kubescape Command Line Interface (CLI) on your system. The installation process varies depending on your operating system:
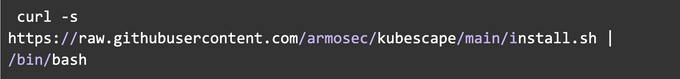
For Linux and macOS run the following command in your terminal to install Kubescape:
For Windows download the latest Kubescape release and run the command.
- Download the latest Kubescape release from the GitHub releases page. Choose the appropriate Windows executable (.exe) file for your system (32-bit or 64-bit).
- Extract the downloaded archive to a directory of your choice.
- Add the extracted directory to your system's PATH environment variable, making the kubescape command available in your Command Prompt or PowerShell.
After completing the installation, you can verify that Kubescape is correctly installed by running the kubescape --version in your terminal or command prompt. This command should display the current version of Kubescape.
Step 2. Running Kubescape on a cluster
To run Kubescape on a Kubernetes cluster, retrieve the current cluster configuration using the kubectl command and then pass it to Kubescape for analysis.
Ensure you have kubectl installed and configured to connect to your Kubernetes cluster. You can verify this by running kubectl cluster-info. This command should return information about your cluster.
Run the following command to fetch the entire cluster configuration and use Kubescape to analyze it against the Kubernetes Hardening Guide:
Let's break down the command and explain each part.
kubectl get all --all-namespaces -o yaml: This command uses kubectl, the Kubernetes command-line tool, to retrieve all resources (pods, services, deployments, etc.) from all namespaces within your Kubernetes cluster. The -o yaml flag specifies that the output should be in YAML format.
kubescape --format yaml: This command runs Kubescape, a Kubernetes security scanner, against the YAML output generated by the previous kubectl command. The --format yaml flag specifies that the results of the Kubescape scan should also be in YAML format.
You can scan your entire Kubernetes environment with Kubescape in one go and receive the results in a human-readable YAML format, making it easier to analyze and act upon any identified security issues.
Step 3. Examining the running cluster configuration
After running Kubescape on your cluster, you will receive an output report. To effectively explore the running cluster configuration, follow these steps:
- Navigate through the output report, divided into sections based on the four main control categories: Access Control, Network Policies, Pod Security, and Auditing and Monitoring.
- Identify the resources in your cluster that have failed controls using the resource type, name, and namespace provided in the report.
- Evaluate the severity of detected issues, prioritizing the most critical ones and considering your environment and application requirements.
- Document the detected issues and remediation recommendations to guide you when fixing and updating your cluster configuration.
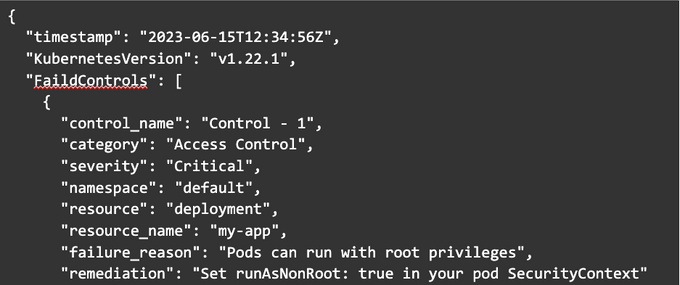
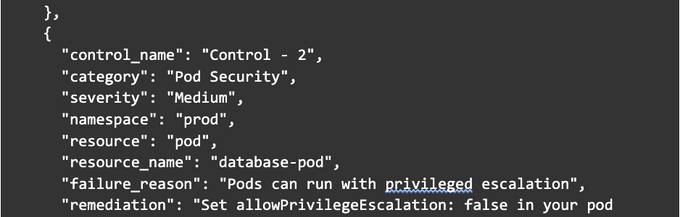
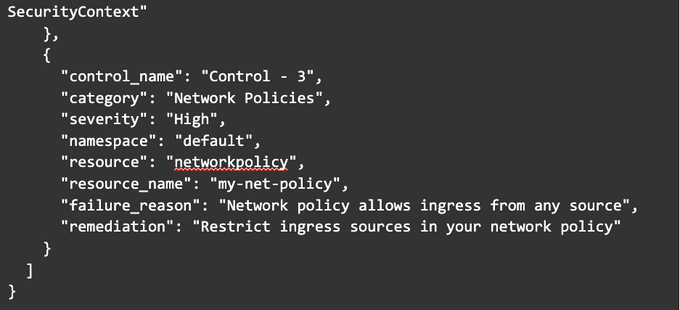
Here is an illustrative example of what a Kubescape output report might look like. Please note this is a simplified example, and actual output will vary based on your Kubernetes environment and any potential security issues it might have.
Lets break down the report to better understand what each component really means:
- "Control_name" indicates the name of the specific security control that failed.
- "Category" refers to the category of the control (Access Control, Network Policies, Pod Security, or Auditing and Monitoring).
- "Severity" signifies the severity of the failed control; this can be critical, high, medium, or low.
- "Namespace" represents the Kubernetes namespace in which the affected resource exists.
- "Resource" and "resource_name" represent the type and name of the Kubernetes resource that failed the control.
- "Failure_reason" explains why the control failed.
- "Remediation" offers suggestions on how to fix the security issue identified by the control failure.
This output can help you identify and prioritize security issues based on their severity and provide remediation recommendations to fix them. Remember, the above example is a simplified representation. The actual output could contain more detailed information depending on the complexity of your Kubernetes deployment and its security status.
Step 4. Scanning Kubernetes manifests
Scanning Kubernetes manifest files helps identify and fix security issues before deployment. To review your manifest files:
- Locate the Kubernetes manifest files (.yaml or .yml extension) containing configuration settings for resources like deployments, services, and config maps.
- Run Kubescape on each manifest file using the following command: kubescape --manifest <path-to-your-manifest-file> --format yaml
- Replace <path-to-your-manifest-file> with the file path, and Kubescape will analyze the configuration against the Kubernetes Hardening Guide, displaying results in the specified format (e.g., YAML).
- Review the output, implement suggested remediations, and test the updated manifests in a staging environment before deploying them to your production cluster.
Step 5. Analyzing the output
After implementing recommended remediations and running Kubescape on your updated manifest files or running cluster, follow these items to examine the new output:
- Compare the new output with the previous report, focusing on previously failed controls to check for improvements.
- If any failed controls persist, review recommendations again and adjust your implementation as needed.
- Document changes to your cluster or manifest files for future audits or assessments.
- Establish a regular schedule for running Kubescape to maintain a secure and compliant environment.
Empower your Kubernetes Security with Kubescape and DevSecOps
As Kubernetes doesn't inherently prioritize security, it's crucial to adopt a proactive DevSecOps approach and prioritize safety when managing your containers. This is where Kubescape can become an indispensable tool.
The steps in this guide work for many engineers and security professionals. If you're looking to automate the process of configuring and deploying Kubescape, you can get started with Jit for free.
Simply install the Jit app on GitHub Marketplace and activate the Kubernetes security control to automatically scan all your repos for K8s misconfigurations, while continuously scanning every PR or deployment to make sure no security issues fall through the cracks.
You'll be able to see all vulnerabilities in the Jit backlog, or within the PR in GitHub if your introducing new code.
Start your free account with Jit today to automate security and scan your K8s manifest files before deployment.