Yippee! We've Raised $38.5M!
Published November 21, 2023.

We’ve also launched a free public beta and are welcoming Abby Kearns onboard as an advisor...You'll want to read this 👇🏼
This week is a big one for us as we announce a $38.5 million seed funding round, the launch of our free public beta version of Jit, to empower developers to own product security without the pain, together with the appointment of Abby Kearns to the company’s advisory board. Abby comes with a wealth of experience in the open source ecosystem, having led the technology vision at Puppet most recently, and before that at Cloud Foundry, and we are looking forward to her insights and direction as we try to make a meaningful impact in the open source security world.
Jit converts security plans from static documents and spreadsheets into living and continuously running code in your favorite repository of choice. By bringing together best of breed open source security tools into a unified and self-serve platform, Jit makes security an integral part of the development pipeline and workflow, from the first line of code.
Minimum Viable Security
High velocity software delivery has changed the game across the board for development cycles from the code to security. The focus has shifted to short, iterative cycles, and these rapid deployment cycles no longer leave any tolerance in the dev cycles for security reviews. The ‘shift-left’ approach emerged to counter this known problem, and even that is now undergoing an evolution, and making room for the ‘born left’ trend where SecOps is now fully owned by the engineering unit.
The problem is that developers are becoming overloaded by suddenly needing to own domains that are not part of their core expertise. Today, the shift-left approach can’t really answer product security needs at the pace of evolving would-be hackers and the growing attack surface. In fact, there’s a growing sentiment that “shift left shifts a lot of bad stuff to developers”. A mindset shift is what’s needed first.
The minimum viable security (MVS) concept, just like the popular MVP concept we all know that has become the backbone of agile product delivery today, means that like any other aspect that the dev-team is working on, security should start small and improve in a continuous and agile manner ‘as code’.
Jit codifies Minimum Viable Security Plans that are aligned with leading industry compliance programs (or even custom internal security programs). These plans cover the threat landscape and the baseline security needed to protect the product from its earliest iterations. A checklist in a spreadsheet turns into code hosted in your repository. Next comes an automated orchestration of all the OSS security tools that engineers love, across the full tech stack: Code, Infrastructure, CI/CD, untime, APIs.
So what does this practically mean for developers?
Instead of having to research, configure, implement and do the work to integrate open source security tools into your stacks and CI/CD pipelines, the security research team at Jit has taken the time to curate and select the tools that will provide the first line of defense for your applications, without having to figure it out yourself.
This is particularly helpful if you aren’t a security domain expert, when this responsibility is newly shifted to your plate. Jit aims to be as easy as other as-code tools we all love, similar to Terraform Plan / Terraform Apply, you can now create a security plan and apply it to your specific stack through a few clicks in the UI.
Using Jit, you can apply different MVS security plans, and iterate on your security as your orgnization matures and evolves. Each plan is activated upon request in three simple steps:
- Choose a pre-made plan or create your own plan
- Select resources you want to apply the plan to
- Activate the plan
It seriously is that easy––three lines of config. Check out our docs.
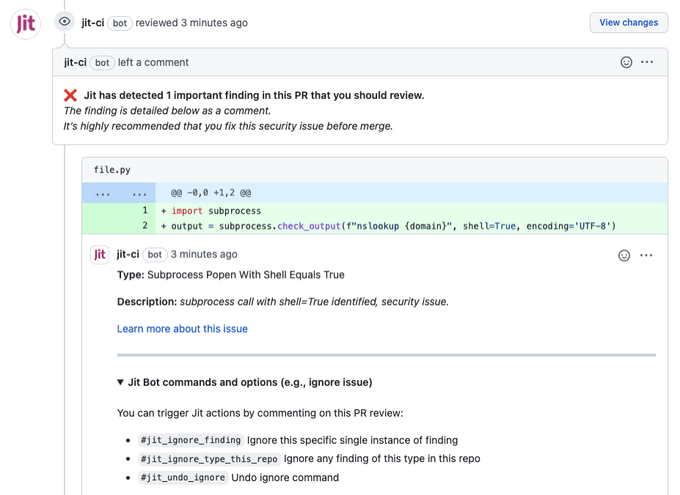
The MVS approach also means actionable insights and noise reduction by only alerting to the most relevant and important vulnerabilities, which you can choose to remediate or ignore inside your existing workflows. One example for the security of your code, is by automatically creating security reviews inside the pull requests in your repos. You can choose to ignore these by leveraging our built-in flags, all without leaving your typical coding context. By doing the work to filter only the critical alerts, we hope to minimize alert fatigue and ensure you only focus on what really matters, shipping code securely.
And this is true for the many other layers of your product security as well, whether it’s the infrastructure and runtime (there are controls for AWS misconfigurations through IaC misconfig), or security controls for third-parties (such npm-audit and OWASP Dependency Check). Each product layer has out-of-the-box security controls that you can choose to apply based on your stack. You get the idea.
By providing a self-serve platform for the best—and most popular—open source and cloud security tools, we are building an easy on-ramp for bringing security into DevOps, ensuring it integrates seamlessly into cloud-native development and CI/CD processes, as a first-class citizen, and not as an afterthought.
Remember the Gap Analysis for Compliance Programs?! Well…No More!
Companies that want industry accepted security certification often will undergo lengthy (and costly) compliance programs––SOC2, ISO:27001––that all start with the gap analysis to understand where you are versus the required standard. Jit makes this simple, by providing a unified dashboard that provides an inventory of your security controls and posture versus the most common security standards, and enables you to quickly understand how to reach your compliance goals.
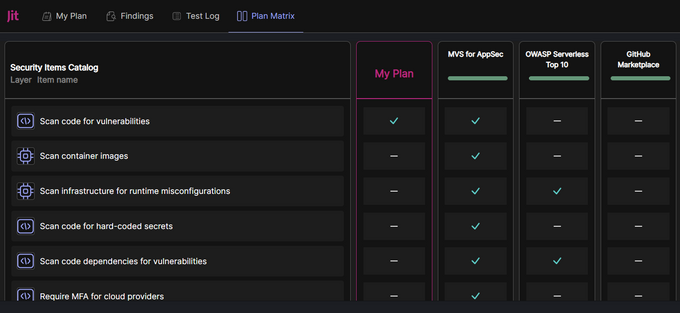
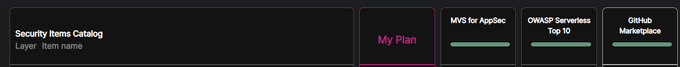
Images below: The Different MVS plans available, and the difference in security posture between them:
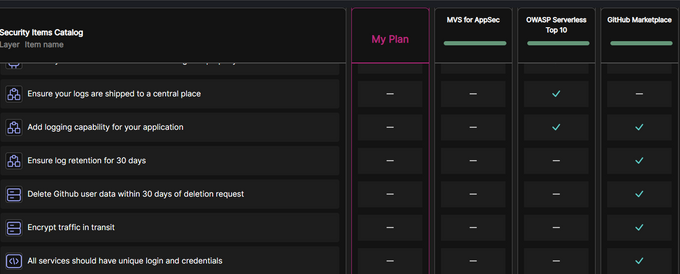
Image below: The inventory of security actions that are included in specific plans; some are shared across plans:
What’s up next for Jit
We will be using this funding to accelerate the shift for organizations to continuous security, allowing developers to break free from shift-left pains while maintaining real, technical security, not just the theatrical kind. We will continue to turn checklists into new codified security plans and add them to the Jit Security Catalog, and expand integration (and support) with many more open source security controls we believe in. And, of course, we want to integrate the tools the open source security community wants, so be sure to reach out and let us know which ones you'd like to see supported next.
In the meantime,we will continue to bring many of the Jit capabilities to developers for free.
Wrapping up
The most secure processes are meaningless if developers ignore them, or actively bypass them.
Jit is here to deliver the simplest approach to implementing DevSecOps building product security automatically into the software from the start, along with a way to continuously maintain it in the language developers understand: code.
And you can get started RIGHT NOW our public Beta has landed >> { GIVE IT A TRY }.