Layoffs and Access Control: How to Avoid Mass Misconfigurations
While revoking access when one employee leaves can be unpleasant, managing it becomes nearly impossible without a system in place when you lay off hundreds or thousands.
Updated September 17, 2024.

Mass redundancies are never easy for anyone. With economic uncertainty and the rise of AI and automation, tech giants are cutting thousands of their workforce at an unprecedented rate. Google, Microsoft, and Amazon combined dismissed over 70,000 employees in the past year.
Tools and processes are generally in place to enable efficient employee onboarding and operational expansion. However, this is different with mass offboarding and deprovisioning, as businesses rarely consider or prepare for the possibility of mass layoffs.
On the operational level, the cost of being unprepared for mass redundancies is well known. These include monetary losses (on annual service subscriptions, hardware, office, and rent), lowered employee morale, and a need to train and upskill the remaining workforce to fill skills gaps.
One of the consequences of mass layoffs that is rarely discussed is the cost of cybersecurity risk. A single disgruntled employee can cause a lot of damage.
The Security Risks of Layoffs at Scale
Mass layoffs pose various security risks. Consider the implications of that one disgruntled developer who realizes they are still logged into the corporate GitHub repository on their personal device. Alternatively, think of how easy it is for malefactors to get their hands on employee hardware in transit on its way back to HQ.
Another issue is the manual deprovisioning of resources granted to employees. Today, it’s not just about returning your laptop and office keycard. With so many SaaS and cloud-based services in everyday use, deprovisioning and offboarding can be lengthy and complicated.
For example, a senior developer in a medium-sized company is likely to have access with loosely set permissions to company code repositories, shared document drives, CI/CD and infrastructure components, production or development servers, cloud infrastructures, on-premises infrastructure with remote access via VPN or SSH and more.
Manually deactivating each account or adjusting its access permissions across so many tools and platforms can leave IT teams scrambling and leaves plenty of room (and time) for costly unauthorized access scenarios. While deprovisioning your systems upon the departure of one employee can be an unpleasant chore, when you lay off hundreds or thousands of employees, managing this process without suitable systems in place becomes nearly impossible.
Mass Misconfigurations: How Bad Can This Get?
In a word: bad. Employees dismissed as part of mass layoffs are not likely to remain loyal to the organization that fired them or be considerate of its data privacy or cybersecurity policies. According to a recent study, nearly one-third of employers have suffered a website hack due to ineffective offboarding.
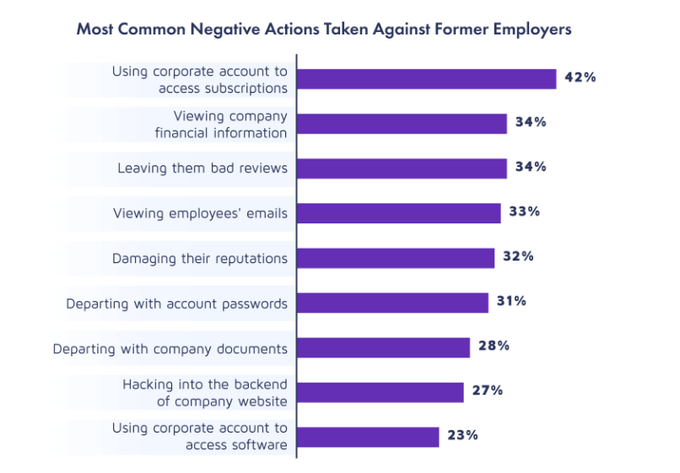
Even more worrying, ex-employees admitted to using a work account to access subscription services (42%), view other employees’ emails (33%) and almost a third (37%) admitted to hacking their former employers’ websites after being laid off or quitting.
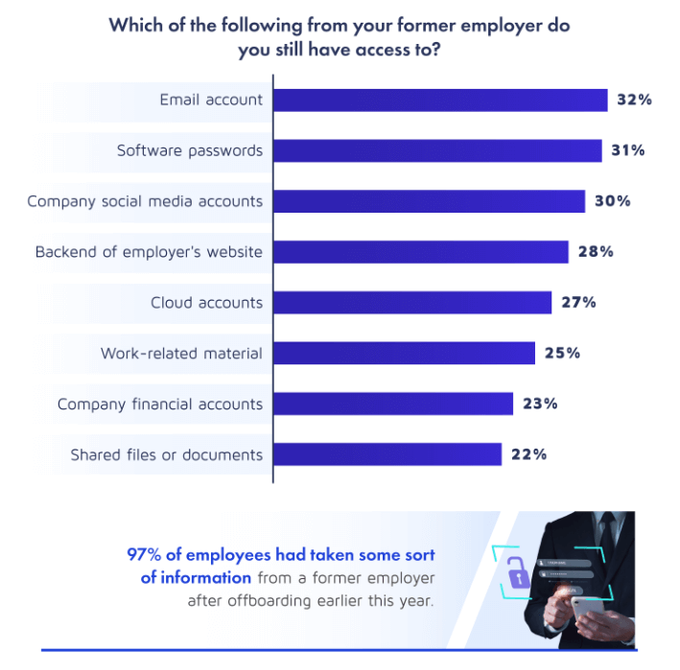
Most employers took little to no action to protect their digital assets from ex-employees. According to recently laid-off employees, many still had access to their former company’s email (32%), software (31%) and social media accounts (30%) for a whole year after being let go. Nearly one-quarter (23%) said they can still access company financial information. Of those, 27% admitted having taken financial information, and 26% have taken payment data.
In addition, cybercriminals have taken note of the recent mass layoffs in the tech sector. They know many companies neglect to deactivate employee access to company resources and data. Everyone has a price, and that of the recently unemployed may just be low enough for cybercrime syndicates to purchase credentials or access sensitive information from those ex-employees.
How to Avoid Mass Access Control Misconfigurations When Scaling Down
Adopt a Security-First Mindset
Trust is critical to collaboration. However, privileged access in the hands of laid-off employees extends the risk of insider threats beyond the currently employed workforce. The best approach to protect your systems from mass configurations of critical access controls is, as the old saying goes, “trust but verify.” This strategy entails, among others, adopting zero trust policies, automating credentials expiration and integrating the necessary tools to enforce the guidelines you set.
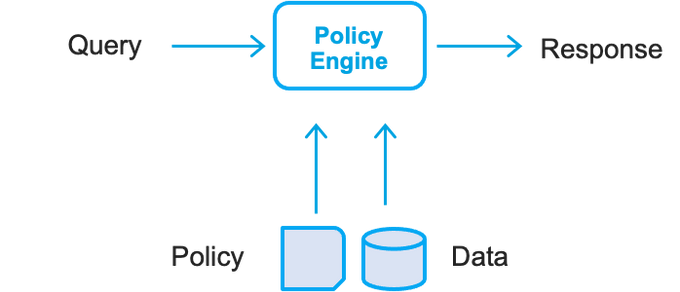
Automate Deprovisioning with Policy as Code
Policy as Code is an approach to policy management in which policies are automatically defined, updated, shared and enforced using code. Codifying security policies for digital employee offloading is easy for developers as most tools use intuitive DSLs (domain-specific languages) or support standard programming and markup languages. For example, your security policies may enforce access permission removal on deprecated features or unused microservices.
Scan your Infrastructure as Code (IaC) for Misconfiguration
Generally speaking, several common cloud misconfiguration errors can serve as attack vectors. Among them are defaults (including passwords and certificates), deprecated protocols and encryption, and overreaching access control permissions. Jit orchestrates the open source tool KICS for you, enabling you to automatically scan your IaC for misconfigurations and then get code-level remediation suggestions.
Mind Your Cloud Assets
Lack of visibility into the mercurial nature of corporate cloud resources is one of the leading causes of worry among CISOs and the source of cloud-based breaches. Constant and consistent privileged access management (PAM) and monitoring of your data, infrastructure, and their uses are the only way to protect your business against configuration drift, disgruntled employees, and honest (painfully frequent) human error.
In addition, you should reconsider your overall approach to access control with entitlements management, entitlement suspension, access reviews, and automated account deprovisioning.
Security That Scales from Day Zero
Protecting your business from insider threats and dismissed employees is not a pleasant activity, especially when you find yourself in the aftermath of a data breach or code leak where an ex-employee took vengeance effectively on your business.
Today, the best approach to developing applications in a cloud native environment is by ingraining data security throughout all business processes, from hiring to retiring or being let go.
At Jit, we believe that security first doesn’t have to mean velocity second. With our DevSecOps orchestration platform, you can scale application security throughout your software development life cycle with a reliable tool built with developers in mind