Cloud Computing Data Security: How to Approach the Risk Factors
Published February 10, 2025

Cloud environments are dynamic and complex, which makes data security a moving target. Misconfigurations, overly permissive access, and unencrypted sensitive data are just some of the risks that can quickly escalate.
Nearly half of all cloud-stored data is classified as sensitive. Yet, less than 10% of enterprises encrypt 80% or more of their cloud data. This showcases how few organizations understand basic cloud security risks and their relevant security controls. And without a solid understanding of the basics, defending against increasingly sophisticated attacks becomes nearly impossible.
By identifying the core risk factors and providing targeted practical solutions, we offer a way to strengthen your defenses and mitigate vulnerabilities.
What Does Cloud Computing Data Security Encompass?
Cloud computing data security is all about protecting the various types of information you store and manage in the cloud. This includes Personal Identifiable Information (PII), financial data, intellectual property, operational records, and customer details. These can be broadly categorized as follows:
Structured Data: Databases, customer information (including PII), intellectual property, electronic health records (EHR), and financial information.
Unstructured Data: Emails, documents, and media files.
Secrets and Credentials: API keys, access tokens, encryption keys, and sensitive information.
Source Code and Codebases: Proprietary applications, software repositories, and critical scripts.
Metadata and Logs: Information about user activities, system performance, and more.
Configuration Data: Settings for cloud infrastructure, virtual machines, containers, and other cloud services.
Backups and Snapshots: Archived data and system snapshots stored in the cloud for disaster recovery or versioning purposes.
Each category has unique security requirements to guarantee that data stays private, accurate, and accessible only to authorized users.
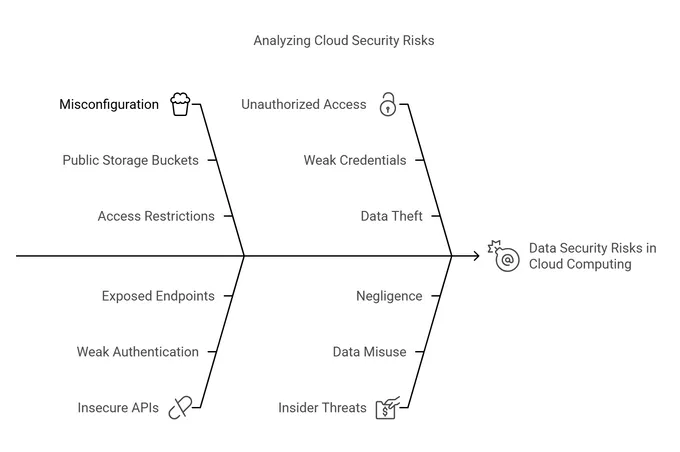
The Most Common Data Security Risks in Cloud Computing Today
- Misconfigured Cloud Storage: Simple mistakes, like setting storage buckets to public or not correctly restricting access, can leave sensitive data accessible to unauthorized users. These mistakes typically happen during setup or updates.
- Insecure APIs: Common issues like weak authentication, lack of rate limiting, and exposed endpoints can turn APIs into targets for malicious activity, including man-in-the-middle (MITM) attacks, where attackers intercept or alter data in transit.
- Data Breaches and Unauthorized Access: Unauthorized access remains a significant threat, often stemming from weak authentication practices or compromised credentials. Attackers who gain access can steal, alter, or delete sensitive data.
- Lack of Proper Identity and Access Management (IAM): Without stringent IAM policies, users may have more permissions than necessary, increasing the risk of insider threats and accidental data leaks.
- Insider Threats: Employees or contractors with access to sensitive information can misuse their privileges by intentionally stealing data for personal gain or inadvertently exposing information through negligence, such as falling for phishing attacks or misconfiguring security settings.
How to Approach Risk Factors in Cloud Computing Data Security
1. Understand Your Shared Responsibility Model With Your Cloud Provider
Cloud security relies on a shared responsibility model that divides tasks between your cloud provider and your organization. Usually, the cloud provider protects the actual data centers, the network equipment, and essential services like storage and computing power. They ensure the cloud environment is safe from unauthorized physical access and attacks targeting the infrastructure.
However, your organization is responsible for protecting the data you store in the cloud and managing how you use cloud services. Your responsibilities typically include encrypting data both when it's stored and while it's being transmitted, setting strong identity and access management (IAM) policies, and properly configuring your cloud resources. Verify the specifics of your provider’s security policies to guarantee that your team is aligned and understands the scope of their responsibilities.
2. Leverage Infrastructure as Code (IaC) Security
Infrastructure as Code (IaC) lets you automate cloud workflows, streamlining the setup and management of cloud resources through code. This approach keeps your environments consistent and scalable. To prevent configuration drift that may accumulate unintentionally over time, use version control and automated testing for your IaC scripts.
Jit’s Product Security Platform makes it easy to secure your Iac templates for vulnerabilities like hardcoded secrets, unencrypted storage, and excessive permissions before they’re deployed. Using tools like KICS and Kubescape, Jit provides comprehensive checks for Terraform, Pulumi, CloudFormation, and Kubernetes manifests.
Jit’s scanning is fully automated – new code changes are continuously analyzed. Alerts and detailed remediation guidance show up in your workflows so that you can take action quickly without needing deep security expertise.
3. Cloud Security Posture Management and Contextual Prioritization
Modern cloud environments operate at a scale and complexity where traditional security management falls short. You need to manage your security posture in a way that combines visibility, context, and prioritization. Without contextual insight and risk-based prioritization, critical risks tied to production systems or exposed resources can be buried in a flood of low-impact issues, leaving your team both overwhelmed and unproductive.
Jit’s Cloud Security Posture Management (CSPM) provides real-time visibility into your cloud environment, monitoring for misconfigurations, excessive permissions, and other vulnerabilities across AWS, Azure, and GCP. Jit connects the dots, incorporating runtime and operational context to highlight the vulnerabilities that matter most.
The Context Engine builds a knowledge graph that links assets, dependencies, and vulnerabilities, giving you a clear picture of how risks interact. With this level of insight, your team can allocate resources to resolve high-risk issues faster.
4. Automated Triage for Cloud Security Misconfigurations
Cloud misconfigurations are the leading cause of security breaches, but identifying them is only part of the challenge. The real value lies in getting the most critical issues to the people who can fix them quickly.
Automated triage makes this possible by prioritizing misconfiguration based on factors like exposure, runtime context, and business impact and routing them to the right teams. For example, a misconfigured public storage bucket containing sensitive data is far more urgent than an internal setting with limited access.
5. Monitor and Secure API Gateways and Endpoints
APIs drive your cloud operations but can be vulnerable to attacks if improperly secured. Start with robust authentication tied to your IAM policies to verify that only authorized users access your APIs.
Implement rate limiting to control the requests each user or IP can make within a set timeframe. Kong is an open-source API gateway and management tool that lets you set these limits (and much more), protecting your APIs from brute-force attacks and preventing service overload during traffic spikes.
Validate all inputs to block malicious data, such as SQL injections and cross-site scripting (XSS) attacks. Use tools like OWASP ZAP to automatically inspect and sanitize incoming data so only safe information reaches your backend.
6. Optimize IAM for Least Privilege
Reduce your organization’s attack surface by fine-tuning for Identity and Access Management (IAM) configurations. Instead of static permission sets, adopt dynamic access controls that adjust based on user behavior, context, and risk factors. For example, if a developer typically accesses specific resources during regular business hours but suddenly requests access outside those times, dynamic IAM can flag this anomaly for review.
AWS IAM Access Analyzer and Azure AD Privileged Identity Management streamline and strengthen access management by identifying and remediating overly permissive policies, detecting unusual access patterns, and enforcing the principle of least privilege.
Jit builds on this by integrating IaC scanning with Trivy, helping you detect and fix misconfigurations like overly permissive IAM roles or public-facing storage buckets. This integration ensures that the least privilege is embedded directly in your infrastructure configurations.
7. Implement Comprehensive Security Monitoring with SIEM Integration
Security Information and Event Management (SIEM) systems like SumoLogic collect and analyze data from every corner of your cloud setup, giving you a unified view of your security landscape.
Integrating identity threat detection into your SIEM setup is crucial. By focusing on user behavior and access patterns, you can spot suspicious activities like unauthorized login attempts, abnormal access to sensitive data, or privilege escalation—red flags that might indicate compromised credentials or insider threats.
Set up specific triggers and rules based on your organization’s threat profile, focusing on critical events like data exfiltration or unauthorized access to sensitive resources—Automate responses to common alerts to speed up incident response and reduce downtime.
8. Enforce Encryption for Data in Transit and at Rest
Attackers often target your cloud data as it moves between services, but with proper encryption, they can’t access it even if intercepted. Use TLS 1.2 or higher to secure all communications. For data that is being stored, apply encryption like AES-256. This keeps it confidential even if your storage systems are breached.
You’ll also need to protect the encryption keys because bad actors can decrypt your data if they gain access to it. Consider using a key management service (KMS) like Azure Key Vault to securely handle key creation, rotation, and storage. Techniques like envelope encryption, where each piece of data has its key encrypted by a master key, can add an extra layer of security and stability.
Mitigate Cloud Data Risks with Jit
Cloud data security is a complex but manageable challenge if you understand the key risk factors and have your bases covered. Automation and advanced tools are needed to navigate the scale and complexity of cloud environments. They streamline and accelerate vulnerability detection, triage, and remediation and make your security efforts more precise.
Jit’s Product Security Platform simplifies cloud security by combining 10 tools into one system, including SAST, DAST, IaC, and Kubernetes security. Its Context Engine prioritizes threats based on runtime impact, while GitHub and GitLab integrations provide automated fixes directly where developers work. Learn more here.