Top 10 Continuous Security Monitoring (CSM) Tools for 2026
Data breach attacks have led to billions of sensitive data records being leaked, stressing the importance of continuous cyber security monitoring tools.
Updated August 19, 2025

AI Summary
Data breach attacks are as explosive as it gets. In 2020, Microsoft suffered a massive leak involving more than 250 million customer support data. While 250 million certainly sounds like a lot, Keepnet Labs makes the record for over 5 billion records exposed. Companies that experience a breach end up underperforming by more than 15% on average over three years.
Enough bad news for the day? Thankfully, there is a solution for every problem, and implementing appropriate security tools will go a long way in protecting your systems. This article will guide you through the ten best continuous security monitoring tools for 2023.
Our Top Picks for 10 Best CSM Tools for 2026
- Best overall CSM tool: Jit
- Best for monitoring servers: Nagios
- Best patch management software: Syxsense
- Best for managing big data volumes: Splunk
- Best for debugging third-party libraries: Lightrun
- Best for remediating security misconfigurations: Spectral
- Best for overall website security: Cloudflare
- Best real-time website spoofing protection: MemcyCo
- Best for securely deploying IoT devices: FirstPoint
- Best for industrial IoT remote monitoring and management: Galooli
What Is Continuous Security Monitoring (CSM)?
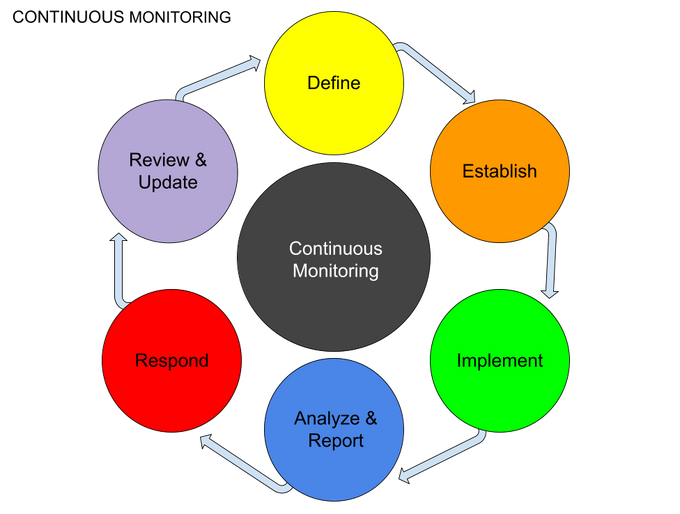
Continuous security monitoring (CSM) is a security practice that continuously assesses an organization's security posture and identifies security risks in real time.
CSM is a proactive approach to security that can help organizations identify and respond to security threats before they cause damage.
» Learn about the best open-source product security tools for developers
How Do Continuous Security Monitoring Tools Work?
Continuous Security Monitoring (CSM) tools enable developers to detect and respond to security threats in real-time.
CSM tools collect data from various sources, including network traffic, system event logs, and user activity. These tools then analyze the data for signs of suspicious or abnormal activity and generate an alert to take appropriate action.
To be effective, CSM tools must be constantly updated with the latest security intelligence and integrated with other security tools, such as intrusion detection systems (IDS) and firewalls.
Types of Continuous Monitoring
Continuous monitoring is the process of monitoring and assessing security controls on an ongoing basis and is an integral part of an organization’s security program.
There are three main types of continuous monitoring: infrastructure, application, and network.
1. Infrastructure Monitoring
Infrastructure monitoring is the process of monitoring the physical components of a system, such as servers, storage, and networking equipment.
The main benefit of infrastructure monitoring tools is that they can help identify problems with hardware or other physical components of the system. For example, a server constantly running at a high temperature may indicate a hardware issue.
2. Application Monitoring
Application monitoring is the process of monitoring the software components of a system, such as the application code, the application server, and the database.
Application monitoring can help identify problems with the application code, such as slow performance, memory leaks, and even malicious code.
3. Network Monitoring
Network monitoring is the process of monitoring a system's network traffic, including the router, switches, and other networking equipment.
Network monitoring can help identify problems with the network, such as high latency or packet loss.
Continuous Security Monitoring Benefits
Organizations are under constant attack from sophisticated cybercriminals. Active monitoring and cyber security tools are required to defend your organization against malicious acts.
Here are the significant benefits of CSM:
- Helps identify potential security risks and vulnerabilities early before they can be exploited
- Reduces the impact of a security breach or attack by providing timely detection and response
- Improves an organization’s security posture by providing visibility into potential risks and vulnerabilities
- Can save time and resources by automating the monitoring process
- Can improve compliance with security-related regulations and standards
Whatever You Choose, You Still Need a Security Plan
CSM tools are essential to respond to threats in real time. However, to ensure maximum protection across your entire CI/CD system, you need to integrate with various tools and have a solid security plan in place. This can easily get overwhelming for your DevOps team.
That’s why Jit offers a Minimum Viable Security plan that makes it simpler to protect all stages of your software development. We also work as an orchestration layer to facilitate integrations with all the relevant security tools you need for each stage. Book a demo and continuously protect your product with minimum hassle.