How to Enable Shared Responsibility for Product Security Across Dev Teams
Updated December 31, 2024.

As applications in the cloud become increasingly common targets for cyber attacks, customers and auditors are asking companies to fulfill increasingly expansive application and cloud security requirements.
Whether the objective is gaining SOC2 compliance, generating reports for customers, or passing a penetration test, security leaders will need to align the development team around the initiative – as developers are the only ones who can make the technical adjustments needed to fulfill security and compliance requirements within the application.
Aligning development teams around security-related outcomes presents technical challenges, but the more complex challenges can be social. Required security controls can slow developers down, which directly contradicts the core developer mandate to deliver new features quickly.
So how can security and development teams share the responsibility of driving security and compliance initiatives forward? In this post, we’ll explore key considerations and Jit’s solutions to do just that.
The task at hand: Building and implementing a developer-centric plan to achieve security and compliance objectives
Implementing security and compliance strategies requires technology and process decisions that will impact the day-to-day routines of developers.
To ensure developer buy-in and progress toward the objective, security and development leaders will need answers to questions like:
- Which tools are needed to satisfy the specific objective?
How will these security tools work together to achieve a shared objective?
How will specific controls be integrated and enforced throughout the SDLC?
Who is going to own the configuration, implementation, and maintenance of these controls?
How can we incorporate security tools into developer routines without hampering developer velocity?
How can we stay notified if vulnerabilities enter production?
Who will be held accountable for the results these tools generate?
How will these results be reported and presented in a way that satisfies customers, auditors, and leadership?
How will we know we’re on the right track?
All of these decisions require extensive research and deliberation, while executing them can be manual and time-consuming.
With so many moving parts and potentially competing interests between development and security teams, driving a developer-centric security initiative can be incredibly complex. Plus, slow implementations and burdensome security processes in the SDLC can erode developer buy-in, which can jeopardize the security or compliance initiative altogether.
These challenges are what inspired Jit. Let’s examine how Jit’s Security Plans and developer security experience can simplify the process of implementing and executing a developer-centric security initiative.
Enable Shared Responsibility for Product Security with Jit
To drive a development organization toward specific security and compliance objectives, security teams will need to set development guardrails to guide developers toward building systems that meet these objectives, but that’s the easy part.
Empowering developers to own the security of their code before production is the real challenge, since security controls often slow them down.
To enable fast implementation of these guardrails and seamless developer adoption of security controls, let’s explore Jit’s Security Plans and unique developer security user experience.
Align development organizations to quickly achieve security and compliance objectives with Jit’s Security Plans
Gaining compliance or meeting customer demands for security usually requires cobbling together separate tooling, integrations, and reporting – which can be time consuming.
Security Plans were designed to automatically implement all of these elements in a unified framework, so you can quickly set up the development guardrails needed to achieve security and compliance objectives sooner.
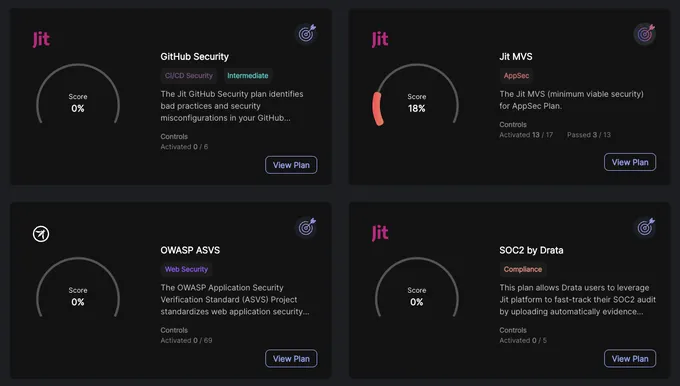
Security Plans start with an objective — such as passing a penetration test or achieving SOC2 compliance — and brings together all the security controls, a unified CI/CD integration, ownership, and reporting needed to achieve that objective. Find an out-of-the-box Security Plan for common security and compliance objectives, or build your own.
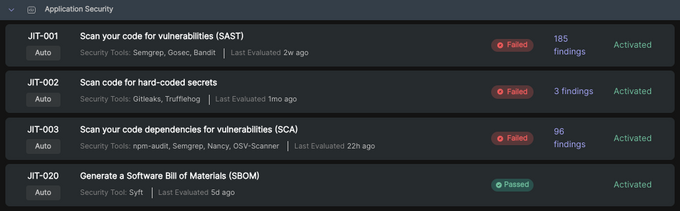
Jit’s security controls cover the full breadth of code-to-cloud security, including your source code with SAST, third party libraries with SCA, secrets, IaC, CI/CD misconfigurations, the cloud runtime environment, and the application runtime environment – providing a single platform and cost for code-to-cloud security.
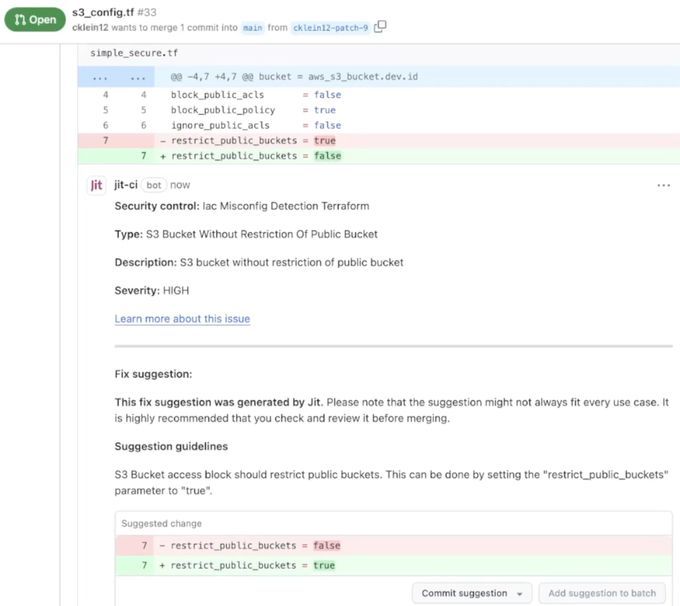
To implement a Security Plan, install Jit on the GitHub marketplace to integrate Jit with your repos, select which repos to monitor, and activate the relevant Security Plan. This will automatically scan all your repos with the desired security controls, while implementing continuous security feedback for all changes to those repos during the pull request.
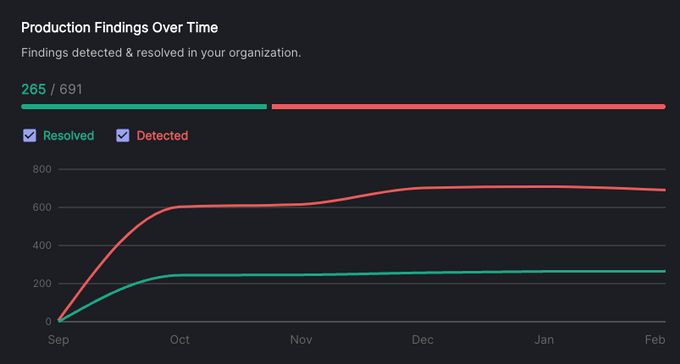
Once activated, Jit monitors progress toward your security or compliance objective. AppSec leads can monitor unresolved vulnerabilities on a per team, per repo, and per security control basis. They can also monitor DevSecOps metrics like exposure window, MTTR, and issues resolved before production.
With Security Plans, there are defined roles for every security pro, developer team lead, and developer, so everyone can get on the same page and work together. As a result, you can simplify and accelerate your path to gaining compliance, passing the next pen test, meeting customer requirements, or just to reduce your security risk.
>> Learn more about Jit’s Security Plans
Empower developers to own the security of their code, without slowing them down
As discussed, setting up security guardrails is the easy part. Enabling developers to consistently deliver code within those guardrails can be the greater challenge, since security controls usually slow developers down.
Jit delivers a unique developer security experience to quickly provide feedback on the security of each code change, so developers can easily own the security of their code.
- No more backlogs of unprioritized vulnerabilities: Jit provides immediate feedback on the security of the current code change, so developers can focus on what matters most – the code they’re about to push to production.
- No more context switching: Jit provides code security and remediation entirely within the PR and IDE, so developers never need to leave their environment to find and fix issues.
- Unified security UX: Jit unifies the UX for all security controls – listed earlier – making many tools feel like one.
- Automated prioritization: Jit’s Context Engine determines which vulnerabilities are exposed to the internet and are exploitable in production, making it easy to focus attention on the highest security risks.
>> Learn more about Jit’s developer experience
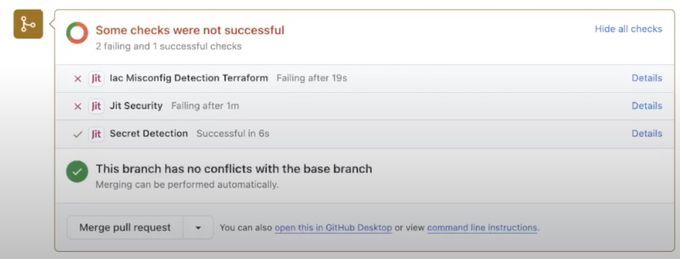
The guardrails discussed in the previous section manifest as lightweight security checks within the development environment for each code change, making it easy for developers to build systems that fulfill today’s security and compliance requirements.
Build a culture of shared responsibility for security
When security teams can own security guardrails and developers can own their code security, these teams can work together towards a common objective – like fulfilling customer or compliance requirements – which can unlock new business opportunities sooner.
Furthermore, by weaving security into every code change for developers, security starts to become a core principle of the development culture. Interested in trying Jit yourself? Start a free trial or schedule a demo to enable shared responsibility for product security across your development teams.