SOC 2 Compliance Checklist: A Comprehensive Guide
SOC 2 compliance is not just a checkbox exercise; it's a continuous process that requires a company-wide commitment to security and privacy.
Updated June 18, 2024

Did you know that 95% of companies are trying to build a culture of compliance, but they struggle to translate that culture into their day-to-day work? If you're developing an application interacting with client data, data protection, and code security should be baked in from day zero.
DevOps teams must continuously follow secure coding practices and use various security tools to conduct vulnerability assessments and testing. Product and security teams should also embed all the necessary tools and processes into their services, ensuring no gaps get to production.
To bridge the security gap, various frameworks can be used, with SOC 2 being the most popular framework for auditing organizations that develop SaaS products or offer online services. Although not mandatory, SOC 2 compliance helps companies improve and prove their security posture.
In this article, we focus on what it takes to achieve SOC 2 compliance and provide a downloadable checklist to help companies stay on track.
What Is SOC 2?
System and Organization Controls (SOC), is a set of frameworks developed by the American Institute of Certified Public Accountants (AICPA) to evaluate and improve the security, availability, processing integrity, confidentiality, and privacy of confidential customer data that organizations store and process.
There are three SOC frameworks available:
- SOC 1 covers accounting and financial reporting;
- SOC 2 and SOC 3 are more focused on cybersecurity, making them ideal for software development companies;
- SOC 3 is aimed at the general public and is much less detailed than SOC 2.
While it is an American standard, SOC 2 is globally regarded as a minimum requirement for online service providers, SaaS developers, and data processing and storage providers. Proof of SOC 2 compliance may be demanded by security-conscious customers and stakeholders looking to gain confidence in the information security practices of a business entrusted with sensitive customer data.
From a software and data security perspective, SOC 2 compliance can be a way to begin putting the Sec in DevSecOps and shifting security left in any growing software development business or initiative.
Even if your organization doesn’t immediately require a SOC 2 compliance certification, understanding and closing the security gaps in your SDLC is critical to improving your security posture.
» This is how your approach to security compliance is destroying dev culture
How Does the SOC 2 Audit Work?
SOC 2 typically focuses on security, and looks to analyze how vulnerable your systems are to cyber threats, the processes you use to secure your systems and customer data, and how you implement security best practices across your organization. The official audit comprises five criteria, which we discuss in detail below. Each measure has a set of controls, and you could look at between 80 to 100 controls.
SOC 2 audits may all look very different—there is also no one-approach-fits-all when preparing for it. However, you should take some common best steps to ensure you’re as prepared as possible and the official audit goes smoothly.
- Choose your SOC 2 type
- Understand the SOC 2 Trust Service Criteria
- Determine your scope
- Review your security controls
- Close control gaps
- Implement control maintenance
- Undergo the official SOC 2 audit
Once the audit is complete, you get a SOC 2 report which you can share with relevant stakeholders and customers and use internally to improve the safety and stability of your systems continuously.
The Complete SOC 2 Compliance Checklist
1. Choose Your SOC 2 Type
The first step on your SOC 2 compliance journey is selecting the type of SOC 2 audit your business needs. SOC 2 audit reports come in two flavors:
- Type 1: With SOC 2 Type 1, your auditor will review policies, procedures, and control evidence at a specific time to determine if controls suit the applicable SOC 2 criteria.
- Type 2: With Type 2, the process is more rigorous, and the report is more insightful as it considers your security controls' past and present effectiveness.
Though SOC 2 Type 1 is not a prerequisite for the Type 2 report, organizations typically complete a Type 1 audit before performing the more in-depth SOC 2 Type 2 audit.
2. Understand the SOC 2 Trust Service Criteria
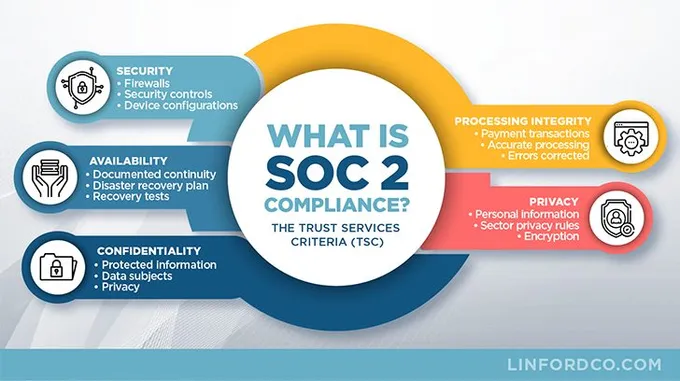
SOC 2 focuses on five distinct principles called Trust Service Criteria (TSC). Understanding which criteria apply to your organization and its processes is the first step to determining the scope of your SOC 2 audit. The criteria are:
- Security: Your systems and the information they store should be protected from unauthorized access, disclosure, or system damage that may compromise the availability, integrity, confidentiality, and privacy of sensitive data or information.
- Availability: Your system and data are available for use and operation by permitted parties to enable the organization to reach its business objectives.
- Processing integrity: Your organizational systems perform data processing in a complete, valid, accurate, and timely manner.
- Confidentiality: You gather, use, store, process, and properly dispose of non-personal data.
- Privacy: The personal information you collect is used, stored, disclosed, and disposed of properly.
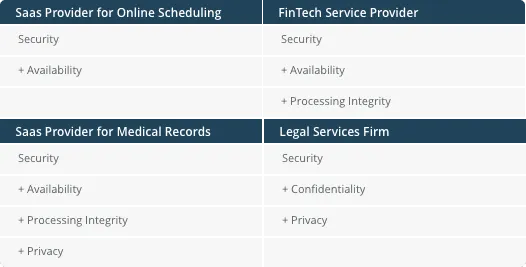
3. Determine Your Scope
Security is the most vital Trust Service Criteria for compliance, but SaaS organizations often include availability and confidentiality in their SOC 2 audit criteria. A broader scope means higher attestation costs but contributes to partner and customer trust and a more robust overall security posture.
Before determining the scope of your audit, consider what is included under each criterion and how it may relate to your organization and its business objectives.
For example, sub-criteria for Confidentiality include data classification and data access control. For Privacy, the sub-criteria of rules pertains to regulatory topics such as Data Subject Rights and Privacy Policies.
4. Review Your Security Controls: Gap Analysis
Now that you have a pretty good idea of what you should have to be SOC 2 compliant, it’s time to check how it compares to what you have.
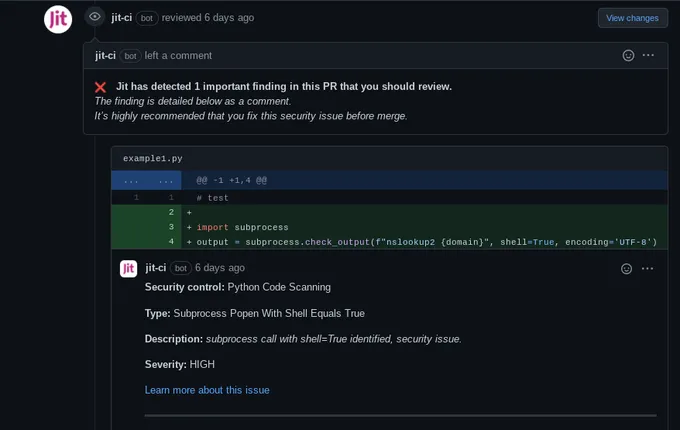
First, you need to understand where your gaps are so that you allocate your resources to the correct places. Gap assessment requires using security tools to scan and test your systems so you know exactly where the gaps lie, spot misconfigurations, manage vulnerabilities, and understand the risks you face regarding security threats.
This step involves the participation of multiple stakeholders across departments and must be coordinated and communicated efficiently. However, most crucially, you need the right tools and reporting features. Open-source SAST tools such as Semgrep, Bandit, or KICS can help you find vulnerabilities and compliance issues in your code.
Deploying various open-source security tools may be necessary for a comprehensive gap analysis. This usually comes with additional complexity, lack of clear visibility into your gaps, redundancy of tools, and alert fatigue. Using a single solution to deploy these tools and get reports could streamline the compliance process and save significant time and resources.
Jit allows you to manage open-source security tools under one platform, automate them for every new PR, and get detailed reporting with further insights and recommendations. Plus, you can build your Minimum Viable Secure Product with Jit, which provides exactly what you need to be SOC 2 compliant, speeding up and easing your SOC compliance journey without compromising development speed.
5. Close control gaps
The gaps you’ve discovered in the previous step of the process need to be remediated. To level up your security controls to meet the criteria of SOC 2, you will need to:
- Review policies
- Formalize procedures
- Employ services or software to streamline security processes
- Address any additional changes like deprecating old in-secure software or services
- Prove that you have addressed and solved all the gaps
This is a challenging undertaking, so automating as many steps as possible will save you time and stress. Jit can help you implement and collect evidence supporting dozens of SOC 2 security controls, so you can confidently close control gaps and prove that you met their requirements.
6. Implement control maintenance
With all the remediation and controls in place to reach SOC 2 compliance, now you must focus on maintaining these. Achieving continuous security requires considering security at every stage of the CI/CD and implementing tools and processes to secure your systems from development to deployment.
The common problem is that the more security tools you integrate into your CI/CD, the more complex its management gets - not what you’d want from DevOps. Automate security through a DevSecOps tool like Jit, so you can effectively maintain and monitor your controls with no developer overhead.
7. Undergo the official SOC 2 audit
Before you pick your auditor and provide them with the information and system access necessary for the audit, you should use a checklist to perform a self-assessment. You can use our comprehensive list, but remember to customize it to your audit scope and transparency demands.
» Ready for another checklist to boost the quality of your solutions? Check the AWS Foundational Technical Review Checklist
SOC 2 Compliance With Jit
While not mandatory, complying with SOC 2 is crucial to boost credibility, prove the security of your systems, and ensure you comply with all the standard data protection rules (which are requested by most official regulations). Plus, if you don’t thoroughly audit your systems at least once in a while, you’ll never really know how vulnerable you are.
Jit's control orchestration framework is vendor-agnostic, which means that you have the freedom to choose the security tools that you need for your complete tech stack. You can add more controls, policies, and tools whenever needed.
The Orchestration Framework employs a plug-in architecture that unites the execution and interfaces of any security control, making it easier for developers to use and ensuring hassle-free SOC 2 compliance throughout your SDLC. You can start using it for free.



![AWS FTR (Foundational Technical Review) Checklist [XLS Download]](https://entail.jit.io/en-assets/jit/fit-in/280x280/Security_Standards-1747040330047.png)

