Top 10 Dynamic Application Security Testing (DAST) Tools for 2025
Dynamic application security testing tools are a shift-left security approach that can help spot vulnerabilities in real-time. Knowing which to choose can be difficult, so here are the best options and their use cases.
Updated February 6, 2025.

In the quest to shift security left, it’s easy to lose track of security once your app goes live. But with cyber threats increasingly targeting live websites and apps, can businesses really afford to make post-production the end of the road for security testing? Well, half of the security professionals admit that developers fail to identify 75% of security vulnerabilities.
Enter DAST, a dynamic approach to security testing that analyzes apps in runtime, ensuring no gaps are left unattended. There are countless DAST tools available, but the last thing you need is to add yet another solution to your toolchain without understanding how it fits your DevOps team’s needs and integrates into your current stack. That's why we've listed the 10 best dynamic application security testing tools for 2025.
Top 10 DAST Tools for 2025 at a Glance
- Best open source DAST for web applications: OWASP ZAP
- Easiest to set up: Jit
- Best reporting: Veracode
- Best for large-scale enterprises: Checkmarx
- Best for leveraging AI-driven models and tools: Spectral
- Best for finding and fixing vulnerabilities fast: Acunetix
- Best for robust and comprehensive security testing: AppCheck
- Best for automated vulnerability scanning: Intruder
- Best for unified SCA and DAST in one platform: SOOS SCA + DAST
- Best attack surface management for AppSec & ProdSec teams: Detectify
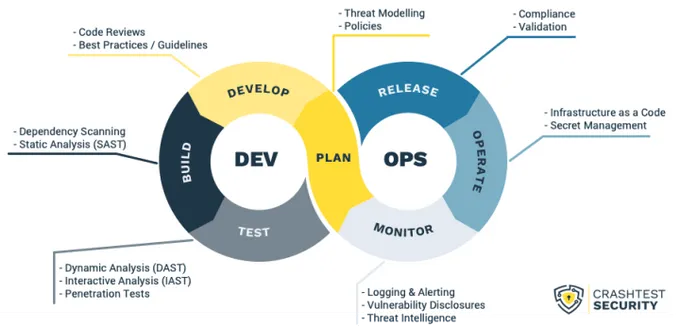
What Is DAST and How Does It Work?
The DAST framework analyzes apps from the "outside-in" by simulating attacks on the application. This “black box” testing method interacts with the running application without accessing its source code, mimicking how an attacker would interact with the app in a real-life scenario.
DAST is different from SAST, which analyzes the application’s source code and related dependencies.
It sends automated requests and payloads to the application (similar to what a malicious attacker would do). Then, it analyzes the app’s behavior and responses, looking for misconfigurations and vulnerabilities that may lead to attacks such as SQL injections and cross-site scripting (XSS).
Once vulnerabilities are found, DAST tools report their findings, which typically include a detailed overview of the vulnerability type, severity, and location to help developers address issues faster. Most of them are automated and never stop, similar to continuous security monitoring tools.
Pro tip: Since this type of testing doesn’t access the source code, it's most suitable for testing apps already in production. However, it can be used across various stages of the SSDLC, depending on business needs.
Adding other types of testing, such as SAST and SCA, can bolster the effectiveness of DAST testing. For instance, SCA security tools work like specialized static security testing, looking specifically into the system’s connected open-source libraries and frameworks. The more layered approach you can take to security testing, the more protected your apps are.
Benefits of Having a DAST Tool
- Real-world and real-time testing: Since DAST solutions simulate real-world attacks, you get real-time insights into how an application would fare against actual threats.
- Full application coverage: DAST tools interact with all exposed application interfaces, ensuring comprehensive coverage.
- Ease of use: Since DAST doesn’t require access to the source code, it is easier to use, especially across third-party applications where the source code might not be available.
- Detection of runtime vulnerabilities: DAST tools excel at finding vulnerabilities that only become apparent during runtime, such as authentication and server configuration issues.
- Scalability: These tools can be automated and integrated into the SDLC, making it easier to scale security testing efforts across multiple applications.
- Meeting regulatory compliance: Many industry standards and regulations, such as HIPAA, GDPR, and SOC2, require dynamic testing methods to ensure data protection and application security.
4 Key Features Your DAST Tool Should Have
- Complete automated coverage: Your tool should scan all exposed application interfaces continuously to identify any and all potential vulnerabilities.
- Integration: Ensure that your DAST tool can integrate seamlessly into your existing DevSecOps pipeline to help streamline your security testing process. DevSecOps platforms like Jit consolidate your security plan so you can automate and manage all your security tools and controls into one platform.
- Real-time insights: Your tool should provide detailed and accurate reports with remediation suggestions based on real-time data, allowing you to prioritize and automate an effective risk mitigation workflow that won’t cause disruption or operational overhead.
- Comprehensive data: Ensure that your DAST tool is comprehensive enough to minimize false positives, providing you only with accurate and actionable alerts.
» Take a look at our top open-source developer-friendly product security tools
Securing Every Part of Your Application at Every Stage
DAST tools support a proactive approach to identifying vulnerabilities, ensuring that web applications can withstand increasingly complex and dangerous cyberattacks. While essential to production environments, they are just one piece of the puzzle and must be added to an end-to-end security plan and toolkit that covers each stage of your SDLC.
If you want to combine development, security, and operations seamlessly, Jit can weave security checks into your CI/CD security process, making security more comprehensive and automated than ever.