CI/CD Security: 12 Tips for Continuous Security
Updated September 17, 2024.

Software development went from being a one-person show to a synchronized orchestra performing at the Sydney Opera House.
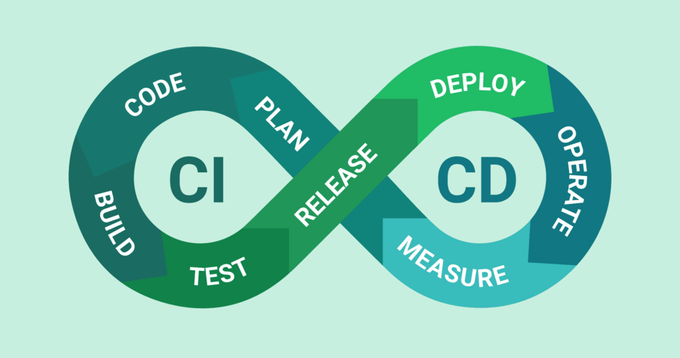
In other words, until recently, each developer would work independently on their tasks or branch. Continuous Integration and Continuous Delivery (CI/CD) have led a transformation, enabling dev teams to work together within a single pipeline and to automate their software delivery with the help of various built tools, application code, secrets, and third-party components.
However, the same automation and interconnection that make CI/CD so powerful also increase its security risks and potential vulnerabilities. With power comes attractiveness (for attackers, at least), so CI/CD security should be at the top of the list for your organization. This article explores how you can optimize your CI/CD for continuous security.
The security risks of CI/CD
The speed and automation of CI/CD can leave pipelines open to numerous security risks, such as misconfigurations, secrets, and malicious dependencies, making them a prime target for attackers.
CI/CD pipelines also tend to get less security attention than production environments, which adds even more fuel to the fire. Without proper security measures, common CI/CD vulnerabilities can lead to irreversible data breaches, service disruptions, and reputational damage for your organization.
You may be familiar with the supply chain attack on SolarWinds’ software in 2020, where hackers used a third party connected to SolarWinds’ systems to access data from thousands of its customers and partners. This attack was one of the largest ever recorded, but the number of attacks doesn’t seem to be slowing down. Gartner expects that by 2025, 45% of organizations will have suffered a supply chain attack.
Why CI/CD continuous security is non-negotiable
The more extensive and automated your CI/CD pipeline gets, the more urgent CI/CD security becomes. Your attack surface expands, giving attackers increasingly more possibilities to access your resources, whether directly or through a third party.
Continuous security, which goes hand in hand with a DevSecOps approach, includes adding security measures to every stage of your pipeline. The process involves various practices such as quality assurance, regulatory compliance, continuous monitoring, and automated scanning.
Many developers are apprehensive about security because it can slow software development and delivery, which is far from the truth. The more they shift security left, the more vulnerabilities they mitigate from the get-go, so they won’t have to deal with its potentially catastrophic consequences later. So without further ado, here are some tips and tricks you can use to implement or improve continuous security.
12 tips for continuous security of your CI/CD pipeline
1. Improve visibility
Improving visibility in a CI/CD pipeline refers to enhancing the ability to see and understand what is happening within the pipeline. By improving visibility, developers and security teams can quickly identify potential issues, such as unauthorized access or suspicious activity, and respond promptly and effectively.
Additionally, improved visibility can help teams identify bottlenecks and areas of the pipeline that need optimization, which can ultimately improve the overall efficiency and performance of the pipeline.
Once you have improved visibility into your pipeline, you can introduce security testing throughout all the stages. Embed and automate security testing such as vulnerability scanning, penetration testing, and security-focused test cases as part of your CI/CD process. By scanning everything continuously, you can catch issues early in pre-production and prevent insecure code from being deployed.
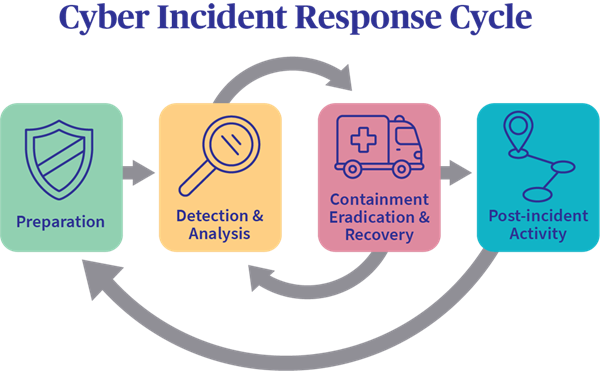
2. Security Incident Response
54% of companies admit their IT teams are not prepared to handle a cyber attack, and one thing is for sure - you don’t want to be a part of that percentage. Establish a security incident response plan that includes cloud-native security incidents. You should define processes and tools for monitoring, detection, containment, eradication, and recovery.
To understand what a Security Incident Plan looks like, you can check the NIST incident response framework, which includes detailed information on what to cover in your plan, including a communication plan and training.
3. Security Logging and Monitoring
Logging lets your team record security-related events continuously, making tracking your application’s performance and activity easier. Not only does this increase visibility over your application, but it also enables your team to pinpoint issues as they arise and solve them faster. Centralize and analyze logs using tools like ELK Stack or Splunk to detect and investigate security incidents promptly.
4. Manage security from one place
There is no lack of security automation tools to use. While often, the more, the merrier, you must also manage and monitor them efficiently without disrupting your team’s daily tasks. DevSecOps orchestration platforms like Jit enable you to integrate various security tools seamlessly into your pipeline and manage them all under one platform. You get a holistic view of your current attack surface and can quickly implement continuous security and remediate issues as they arise.
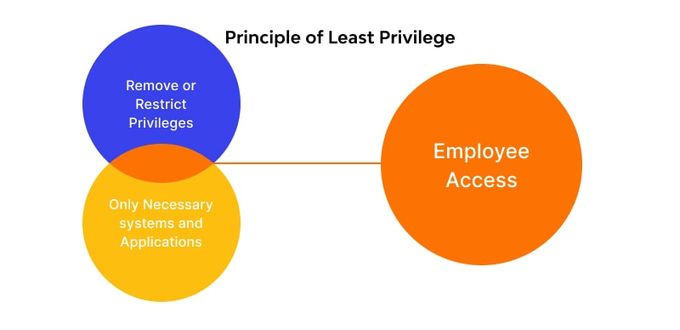
5. Implement a Least Privilege approach
Implementing a least-privilege strategy involves granting users and systems only the access they need to perform their intended functions within a CI/CD pipeline. This approach aims to minimize the risk of unauthorized access and reduce the likelihood of accidental or intentional misuse of system resources.
Establishing access controls is a vital part of implementing a least privilege approach. It involves defining policies that govern who can access specific resources, what actions they can perform, and under what conditions. Access controls include user authentication and authorization, role-based access control, and network segmentation. Access controls are essential in a CI/CD pipeline where sensitive data is often transmitted and stored.
6. Carry out checks before commits
Perform security checks and quality assurance tests before code changes are committed to the CI/CD pipeline. This process involves implementing automated checks, such as static code analysis, dependency scanning, and vulnerability assessments, to ensure that code changes do not introduce security vulnerabilities or degrade the overall quality of the codebase.
By carrying out checks before committing code changes, developers can catch potential issues early in the development process and prevent them from progressing further down the pipeline. This approach helps ensure that code changes are secure and high-quality and saves time and resources by catching issues early before they require significant rework or remediation efforts.
7. Continuous compliance
Ensure that all processes, workflows, and data handling within a CI/CD pipeline align with relevant policies, regulations, and industry standards. This step is essential for maintaining data privacy, protecting intellectual property, and complying with legal and regulatory requirements.
Legitify can help you automate policy compliance in a CI/CD pipeline. It checks policies against all the resources within a pipeline, including code changes, infrastructure components, and third-party dependencies, to ensure that all resources meet the defined regulations before they are deployed to production environments. And here are the good news: Jit can now orchestrate Legitify into your CI/CD pipeline, so you can implement it and manage it with zero effort required.
8. Store secrets safely
Keep sensitive information such as API keys, access tokens, and passwords secure and protected from unauthorized access. To store secrets safely, developers should avoid hardcoding sensitive information in code and instead use secure storage solutions such as key vaults or credential stores. These solutions allow for the safe storage and management of secrets, ensuring they are encrypted and accessible only to authorized users and applications.
9. Address CI/CD misconfigurations
One way to address misconfigurations is to establish transparent configuration management processes that include regular audits and reviews. You should also implement automated security testing, continuous scanning, and monitoring to get real-time feedback and quickly remediate any issues.
Additionally, addressing misconfigurations involves ensuring that all components in the pipeline are configured with appropriate security settings. For example, ensure all tools and applications are up to date, and access controls and permissions are correctly configured to prevent unauthorized access.
On the other hand, continuing with a misconfiguration can be a significant security threat. For example, a CI/CD pipeline misconfiguration invites attackers to inject malicious code into the production environment. Ultimately, this can lead to issues like theft of sensitive data, disruption of services, and damage to the organization’s reputation. Also, it can go unnoticed for an extended time, giving enough time to attack and cover their traces.
10. Secure the code repository
The code repository is where all application code is stored. Any security vulnerabilities in the repository can be exploited to gain unauthorized access to the code or even the entire pipeline. Ensure access controls and permissions are correctly configured to secure the code repository. Only authorized personnel should have access to it, and access levels should be carefully controlled.
11. Test all CI/CD resources
Ensure that every component and tool within the pipeline is secure, not just the application code itself but any third-party libraries, dependencies, and tools used throughout the pipeline. Some tools you could use to scan your resources for vulnerabilities include the SAST tools Semgrep and Gitleaks, which scans Git repositories to detect hardcoded secrets.
There are many more, but these are just some of the ones Jit can seamlessly integrate into your pipeline. With Jit, you can manage and monitor these tools under one platform - and remediate any issues that arise instantly.
12. Enforce software supply chain security
Verify that all third-party components are trustworthy, unmodified, and up-to-date, implement processes that track the origin and the changes made to third-party components, and verify their integrity. You can use Source Composition Analysis (SCA) tools such as npm-audit to identify third-party dependencies and mitigate potential issues.
Be proactive, not reactive
Your CI/CD pipeline holds an incomprehensive and invaluable amount of data, which shouldn’t get to the hands of attackers in any circumstances. The tips we shared will hopefully put you in a much stronger position to implement continuous security across all pipeline stages and be more proactive than reactive. If you want to make it even easier for your team to shift security left and embrace security rather than be overwhelmed by it, Jit can help. Get started for free.