8 Fundamentals for Cloud Native Applications Security You Shouldn't Overlook
Updated June 12, 2024.

Distributed, scalable, cost-effective, and infinitely flexible, cloud computing has rightfully earned its place as the industry standard for modern application development. Cloud computing empowers developers to build and deploy scalable applications that can be containerized, reused, disassembled into self-contained resource-efficient microservices, and use serverless functions.
But as the meme goes: with great power comes great responsibility. The authority granted to us by the innovative distributed virtualization technologies of Amazon, Google, and Microsoft requires that we take responsibility for our share of the efforts to protect the resources and assets we commit to the cloud. With half of all data breaches taking place in the cloud, we simply can’t afford to overlook the risks of taking to the cloud unprotected. In this article, we go over eight critical tips for protecting your cloud-native applications.
The Importance of cloud-native applications security in 2023
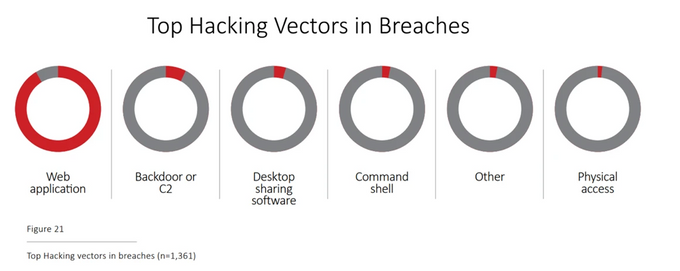
As sensitive data and mission-critical workloads migrated to the cloud, so did cybercrime. A recent survey among data security and IT professionals revealed that cloud assets are the most attractive targets for cyber attackers. Over a quarter (26%) said cloud-hosted applications were the most prominent attack targets, followed by cloud infrastructure (25%). Moreover, web applications are the most prevalent hacking vector in successful data breaches, leaving backdoors and remote desktop applications in the proverbial dust.
Securing cloud-native applications differs from securing on-prem servers or protecting static and isolated endpoints. It requires a different approach to how we build our applications and deploy and serve them in a way that ensures regulatory compliance, nurtures digital trust, and protects two of the most important assets your business holds - code and data.
8 fundamentals of cloud-native applications security
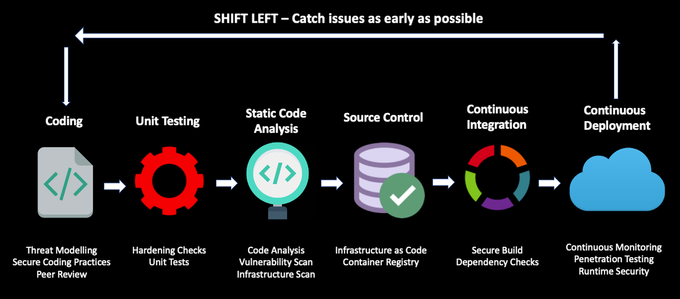
1. Shift security left
Code and data security must be integral to your software development lifecycle (SDLC) from day zero when relying on cloud services and resources. Developers must adopt a security-first approach without being security experts and without extensive operational overhead. To accomplish this and deploy secure code without compromising development velocity, they require a robust developer-centered toolchain to enable effortless orchestration of development security operations - DevSecOps.
Side note, if you're one for innovation, "born-left" cybersecurity is all the rage now. Born-left security solutions are designed with software developers in mind rather than being augmented. The theoretical and practical advantages of born-left security are clear for Cloud Native applications and are personified in projects like MVSP (minimum viable secure product).
2. Secure your infrastructure
The shift from owned and wholly controlled infrastructure to a distributed software-defined environment (the cloud) took infrastructure management and provisioning away from IT teams and placed them under the ownership of developers. With Infrastructure as Code (IaC) and the codified and containerized code-to-cloud application deployment architecture, detecting misconfigurations has become easier to automate. With open-source tools like KICS, Kubescape, and Prowler, you can seamlessly integrate IaC security scanning into your CI/CD pipeline.
3. Harden your access control policies
To ensure that only authorized users and services can access your cloud resources, you must implement robust IAM policies and controls across all cloud services. Some of the things you can do, for example, is employ least privilege and zero trust principles and enforce multi-factor authentication (MFA) to minimize the risk of unauthorized access. One of the built-in tools in the Jit DevOps orchestration platform is the aws-MFA-checker that enforces MFA for all AWS user accounts.
4. Protect your APIs
APIs are the primary channel cloud-native applications employ for communication between microservices. In addition to strong authentication and authorization mechanisms for all your API endpoints, you must validate and sanitize the API input and apply rate limiting and throttling to protect against API-based attacks.
You can passively scan your APIs for vulnerabilities with OWASP ZAP to detect an extensive (and expert-curated) list of weaknesses, misconfigurations, and security vulnerabilities that may be lurking in your APIs unbeknownst to you.
5. Encrypt everything
Protecting data from unauthorized access and most regulatory data privacy laws demand that sensitive data be encrypted in transit and at rest. White most cloud providers offer basic encryption features as part of their service; it’s worth considering the application of additional layers of encryption onto data that traverses public clouds.
6. Streamline security testing
To ensure your code is free of misconfigurations, vulnerabilities, and sensitive data (like code secrets and PIIs), you can employ automated security testing in your CI/CD pipeline. Tools like OWASP ZAP, GitLeaks, and Semgrep are just a few examples of open-source application security tools you can employ.
7. Implement continuous security monitoring
Continuous cloud security monitoring entails a cohesive, structured approach to logs and audit trails. Not only that, but it is imperative that you implement tools that can contextualize the errors and provide you with a clear picture of your cloud-native application security posture, including deviations in typical user or service behavior and emerging supply chain threats.
Identifying and remedying the gaps in your security posture must happen much faster in cloud-native environments. Hackers can exploit newly discovered vulnerabilities at the speed of the cloud, which can escalate into full-blown breaches all at once.
8. Own your shared responsibilities
The most crucial pillar of cloud-native application security is understanding the shared responsibility model employed in cloud computing.
The cloud-native software architecture significantly blurs the boundaries between application and infrastructure, de-facto making cloud infrastructure engineering the job of developer teams and DevOps practitioners. Since all Infrastructure as a Service (IaaS) is based on software virtualization, the only aspect of securing the infrastructure wholly owned by the cloud service provider is the physical security - protecting the metals that hold and process your data from unauthorized physical access. Everything else is, to one degree or another, under your responsibility and control.
Taking complete ownership of your side of the cloud-native application security bargain is critical to choosing the right processes, tools, and policies to safeguard your cloud-based data and workloads. Only once you understand which security controls are available to you, the cloud customer, and how you can manage and orchestrate your cloud-native applications' security posture can you begin to secure your applications and facilitate a cloud-native SSDLC.
Leveraging open source technologies to secure cloud-native applications
Cloud-native applications security is built on understanding the shared responsibility model and implementing DevSecOps methodologies to infrastructure and applications. The tools cloud vendors offer customers looking to secure their cloud-native application vary significantly between providers. They often have a steep learning curve and unique properties that make multi-cloud operations challenging to protect without the massive overhead and a specific cloud-native security skill set.
With Jit’s DevSecOps orchestration platform, high-velocity development teams can orchestrate OSS tools like OWASP ZAP, Semgrep, Gitleaks, and several more to leverage the power of community-supported open-source libraries and tools across cloud providers and throughout the SDLC.
Jit automates the frustrating process of selecting, implementing, configuring, and managing your Application Security toolchain (IDE-Code-Pipeline-Cloud-Runtime), empowering you to get full coverage in minutes with a developer-native user experience and auto-remediation capabilities. Start for free here.




![Application Security Policies to Automate Vulnerability Triage and Management [PDF download]](https://entail.jit.io/en-assets/jit/fit-in/280x280/Application_Security-1739896057069.png)
