10 Pros and Cons of GCP Security Command Center
Updated September 8, 2025
There is no doubt that Google is one of the most innovative companies. In fact, if you want to find or compare others, you'll likely Google it. From search engines to smartphones, it has shaped our digital lives. And with its cloud solution, Google Cloud Platform (GCP), its impact in the cloud arena is no different.
However, no amount of innovation can make GCP attack-proof. The cloud is home to increasingly more threats, and they come with a hefty price tag. A cloud breach costs businesses a global average of $4.35 million; if you narrow it down to US-only cloud users, this number skyrockets to $9.44 million. Not exactly peanuts.
To avoid paying a seven-digit fee for a cloud breach, you must detect threats faster and more accurately. Enter Security Command Center - GCP’s very own threat detection tool that continuously monitors your Google Cloud environment to spot threats and strengthen security.
In this article, we delve into Security Command Center, analyzing its advantages, disadvantages, and how you can fill in its gaps for a fully optimized security posture.
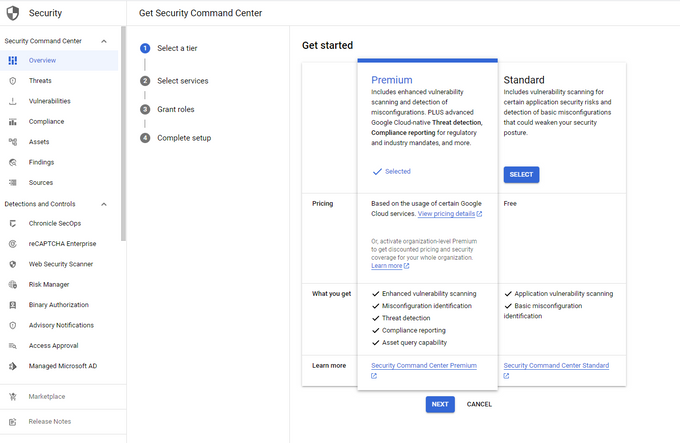
Unpacking the GCP Security Command Center (SCC)
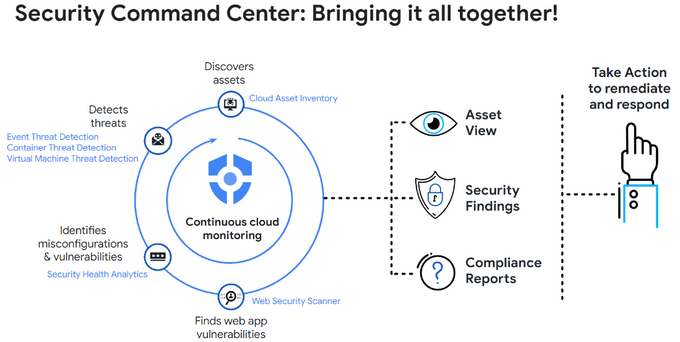
The GCP Security Command Center (SCC) is Google’s built-in security and vulnerability detection solution. It monitors your GCP environment to detect threats such as compromised identities (meshing with IAM), data exfiltration, and misconfigurations.
It also provides remediation suggestions and best practices to mitigate potential security issues and help you prove compliance with critical regulations. Lastly, it enables you to use attack path simulation to see where and how attackers could get into your system, understand your attack exposure, and shut down gaps before they are exploited.
5 Pros of GCP Security Command Center
1. Security Analytics and Intelligence
GCP Security Command Center (SCC) offers an advanced suite of log analysis and threat intelligence feeds used to understand security incidents and anticipate potential threats. Thanks to SCC's analytics, organizations can craft robust, adaptable defensive strategies tailored to the dynamic nature of cyber threats and remain proactive amidst an evolving cybersecurity landscape.
2. Continuous monitoring
The ever-present and vigilant nature of SCC is one of its core strengths. The platform persistently scans for vulnerabilities and misconfigurations within the cloud environment. Doing so provides a comprehensive, granular view of the organization's resources. This continuous vigilance enables organizations to promptly detect and address potential threats before they become substantial problems.
3. Centralized visibility
SCC offers centralized visibility across various Google Cloud Platform services, transforming the daunting task of managing multiple security platforms into a manageable process. It provides a unified snapshot of an organization's security posture. This panoramic view also assists with maintaining compliance with regulatory bodies such as PCI DSS.
4. Security recommendations
Leveraging Google's extensive security expertise, SCC delivers actionable security recommendations, such as timely patching of systems, closing unnecessary open ports, and restricting access rights to sensitive data. These insights aid in quickly remediating identified vulnerabilities, reducing response times, and preventing further exploitation.
5. Integrations with other GCP tools
SCC integrates effectively with various GCP tools, such as Cloud Security Scanner, Cloud DLP, and Cloud IAM, thus streamlining cloud security management within your GCP environment. Utilizing these integrations enables organizations to build more robust cloud security strategies and have an all-in-one platform to rely on. However, as shown below, faster and more seamless integrations are limited to GCP tools.
5 Cons of GCP Security Command Center
1. Lack of customization and extensibility
Despite its comprehensive features, SCC has limitations in customization and extensibility. For instance, it may not create custom detectors for organization-specific threat detection or customize the findings' severity levels. Extensibility, referring to its ability to connect with third-party solutions, might also be limited. These limitations necessitate a thorough evaluation of SCC's fit for an organization's unique needs.
For example, it might not adequately cater to the specific needs of Python applications, which is where a tool like Bandit can step in to provide Python-specific security analysis. Similarly, Gosec can be a valuable tool for those with Go applications.
2. Lack of real-time monitoring and response
While SCC provides continuous monitoring, it does not offer an automated incident response. This lack of real-time response might fall short of the needs of larger organizations or those with complex infrastructures that require instant actions to mitigate threats.
3. Complexity
SCC’s plethora of features can be a double-edged sword, causing complexity for teams lacking extensive security expertise. While the platform offers comprehensive security capabilities, leveraging all of them may require dedicated security professionals.
Tools like Legitify can streamline the process by automatically validating SCM hooks for CI/CD pipelines. This, coupled with Jit's easy access and integration to various tools, including cloud vulnerability and misconfiguration scanning tools like KICS and Prowler, allows for a more manageable security setup.
4. Integration challenges
Although SCC integrates effectively with other GCP services, organizations might need help connecting it with external security tools, such as SIEM solutions. While SCC has connectors for some non-GCP solutions, the support might only extend to some tools organizations use, necessitating careful compatibility evaluation.
For example, while SCC might not natively support a tool like Nancy, which identifies vulnerabilities in Golang dependencies, integration through APIs can make it possible.
5. Hidden costs
Using SCC may involve additional costs, particularly for large-scale deployments. For example, while some vulnerability scans are included in the basic package, other scans or enhanced services such as Web Security Scanner could increase costs. The pricing structure of SCC is layered and can be complicated, potentially leading to unexpected financial implications for organizations that aren't thoroughly familiar with the costs associated with specific features or usage levels.
Enhancing your GCP security
You can amplify SCC’s capabilities by incorporating additional practices and tools into your security management plan. For example, infrastructure scanning tools like Prowler and Trivy can help identify infrastructure misconfigurations and vulnerabilities in container images. Legitify can strengthen your CI/CD security to ensure the integrity of SCM hooks, and tools like Nancy and Bandit can provide additional application-level security checks.
Another solution lies in deploying cloud-native security tools. These tools explicitly address the unique security challenges of cloud environments. They offer features such as network monitoring, container security, and workload protection, which can complement SCC's existing capabilities.
That said, dev teams may prefer not to work with too many security tools that can slow down their development process. A solution like Jit effectively solves this problem, enabling teams to orchestrate all OSS tools and view their findings in a single dashboard.
In addition to the strengths and weaknesses discussed above, it is crucial to remember the importance of securing your software development process. Implementing a Secure Software Development Lifecycle (SSDLC) can significantly boost your organization's security posture, protecting against potential threats and vulnerabilities at every stage of the development process.
Should I deploy GCP Security Command Center?
GCP Security Command Center offers robust capabilities for continuous monitoring and threat detection. Is this the only tool you should use? Absolutely not. Security is highly multi-faceted, especially in the cloud. You need to ensure a streamlined security plan from the get-go (development phase) to the finish line (deployment) and beyond, which involves integrating various security tools like the ones mentioned above. If you want to try Jit, learn more here.

![How to Use AWS Secrets Manager in the CLI [With Examples]](https://entail.jit.io/en-assets/jit/fit-in/280x280/Blog_Thumnail_10-1709638263339.png)


