Vulnerability Assessments vs. Penetration Testing: Key Differences
Updated April 24, 2024.
Vulnerability Assessments vs. Penetration Testing: Key Differences
In the race for technological innovation, companies often sprint toward product launches but find themselves in a marathon when fixing vulnerabilities. This dichotomy poses a significant challenge, especially with the ever-increasing security loopholes.
CISA recommends addressing critical issues in less than 15 days, but it may be wishful thinking. IT teams are inundated with an ever-increasing volume of security alerts, making it challenging to prioritize and address each one effectively. Many vulnerabilities go entirely unaddressed, and those that get fixed take an average of 271 days.
This extended period exposes organizations to potential cyberattacks and highlights a significant cybersecurity responsiveness and effectiveness gap. There is a real need for more robust security assessments and testing, with vulnerability assessments and penetration testing emerging as critical strategies.
What is a Vulnerability Assessment?
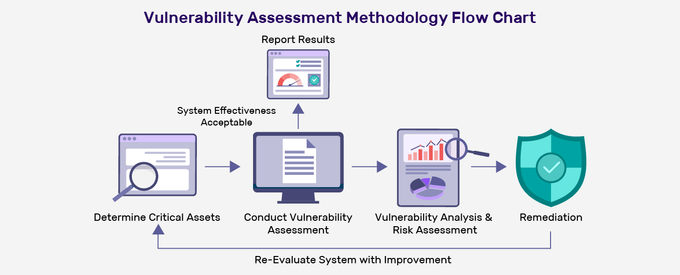
Vulnerability assessments are systematic evaluations to identify, rank, and address security vulnerabilities within software products and applications. These assessments are critical to any shift-left security strategy as they happen during the development and pre-deployment phases. The goal is to detect and mitigate security risks before they make it to deployment.
These assessments are essential in a field where data security is non-negotiable, such as the healthcare sector, which is under intense scrutiny to protect medical data. But really, they're vital for any organization that wants to safeguard its users' personal information. Jit's DevSecOps platform boosts the efficiency of these assessments by integrating security tools like Semgrep for static code analysis and Trivy for scanning container images. You can automate and manage all tools from a single interface, easing security management for your team.
Pros
- Spot Security Flaws Early – You can identify vulnerabilities in your systems and applications before they get to production, avoiding roadblocks down the SSDLC line and preventing significant attacks such as malicious code.
- Cost-Effective Prevention – Proactively addressing risks helps avoid the high costs associated with data breaches and system failures.
- Meet Compliance Requirements – Regular assessments help you to comply with industry regulations such as GDPR and SOC2, reducing the risk of fines and legal issues.
- Minimize time to fix findings - Vulnerability assessments help you avoid context switches, which happen frequently between developers, so you can address each vulnerability faster with the right remediation process.
Cons
- Potential for False Positives/Negatives – You might encounter false alerts or miss specific vulnerabilities, leading to misdirected efforts or overlooked risks.
- Lack of Exploit Context – Vulnerability assessments don’t usually provide insights into how an attacker could exploit identified vulnerabilities, leaving some uncertainty in your security strategy. However, DevSecOps platforms like Jit can give you the exploit context on each issue it finds.
- Limited Scope of Detection – Assessments typically focus on known vulnerabilities, potentially missing out on zero-day exploits or advanced persistent threats.
| Pros | Cons |
|---|---|
| Spot Security Flaws Early | Potential for False Positives/Negatives |
| Cost-Effective Prevention | Lack of Exploit Context |
| Meet Compliance Requirements | Limited Scope of Detection |
Penetration Testing
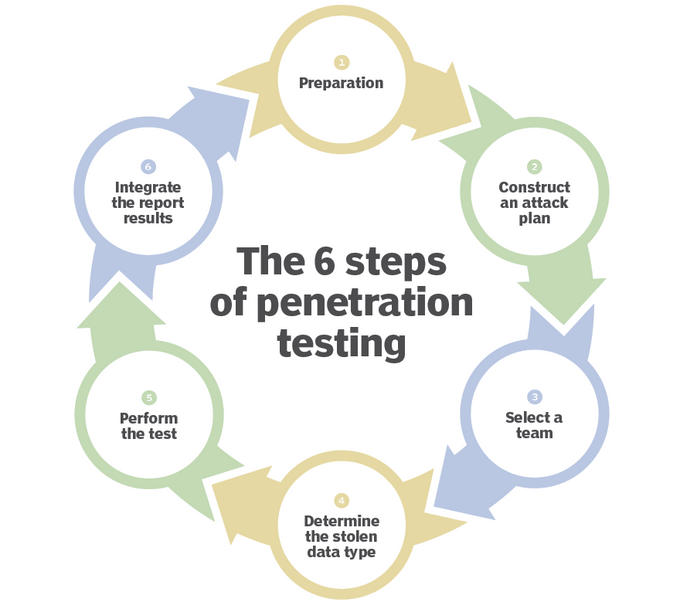
Penetration testing, or pen testing, is a systematic process designed to simulate a cyberattack against your system or software to identify vulnerabilities that could be exploited. Unlike vulnerability assessments, which are security check-ups listing potential issues, pen testing is about seeing how deep these issues go. It's typically done after you've built and deployed your software to ensure your defenses work when needed most.
Pen testing is most commonly handled by a cybersecurity professional who can poke and prod at your system defenses to try and find an unmitigated vulnerability – aka a backdoor. DAST tools can automate much of this manual work. Jit's platform offers integration with advanced tools like OWASP ZAP, which is highly effective for web application penetration testing.
Pros
- Real-World Attack Simulation – You get a hands-on understanding of how an attacker could exploit your system, revealing real-world vulnerabilities.
- Targeted Remediation – It provides specific, actionable insights, allowing you to prioritize and strengthen your defenses effectively.
- Testing Defense Mechanisms – Tests your security measures under pressure, showing how they perform in an attack scenario.
Cons
- Potential Disruption – It can be disruptive, risking temporary outages or performance issues, as it actively exploits vulnerabilities.
- Resource Intensive – Requires significant time, expertise, and financial resources, making it challenging for smaller teams.
- Requires Expert Interpretation – Pen testing results can be complex and often require expert analysis to translate findings into actionable remediation steps.
| Pros | Cons |
|---|---|
| Real-World Attack Simulation | Potential Disruption |
| Targeted Remediation | Resource Intensive |
| Testing Defense Mechanisms | Requires Expert Interpretation |
Vulnerability Assessments vs. Penetration Testing: Key Differences
1. Purpose
Vulnerability assessments aim to find and catalog potential weak spots across your SSDLC, particularly in the early stages. It's about creating an inventory of what might be vulnerable without trying to break in.
In pen testing, the objective shifts to actively exploiting the identified vulnerabilities. It’s about attacking your system to see how these weaknesses hold up under real stress, testing your defenses and the overall robustness of your security measures.
2. Scope/Depth of Testing
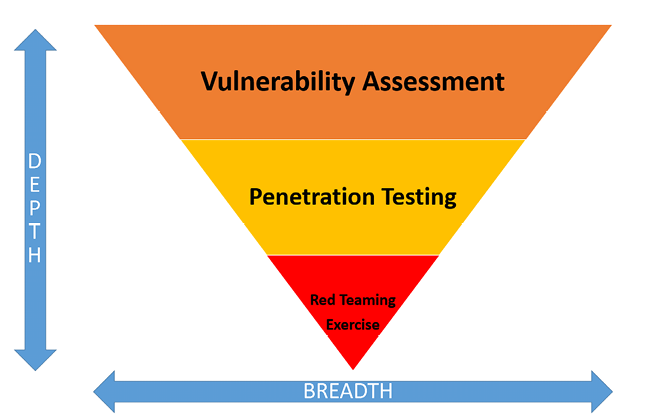
Vulnerability assessments cast a wide net, scanning various system components to identify potential issues. However, this method skims the surface, focusing on breadth rather than depth.
Penetration testing, on the other hand, adopts a more targeted approach. It concentrates on specific vulnerabilities or systems, probing deeply to exploit and understand the true impact of each identified weakness. While vulnerability assessments provide a broad overview, penetration testing offers a deep dive into selected high-risk areas, revealing the extent of potential security breaches.
3. Timing
Vulnerability assessments are typically woven into your security routines and conducted periodically throughout the development lifecycle. This regularity helps promptly identify new or emerging vulnerabilities, especially during early development stages. DevSecOps tools like Jit enable you to run vulnerability assessment tools on schedule so you can continuously monitor for vulnerabilities and strengthen your security posture management.
Penetration testing is more strategically timed. Often, teams would schedule it after significant milestones, such as launching a product feature or completing a development cycle, to ensure that their system is robust and ready.
4. Permissions
For vulnerability assessments, you typically need basic access to systems and networks. This permission level allows you to scan and identify potential security issues without disrupting normal operations.
However, penetration testing requires a higher level of access. Since pen testing involves actively attempting to exploit vulnerabilities, you often need explicit authorization, sometimes even legal clearance, particularly if the testing could impact live environments or access sensitive data.
5. Methodology
In vulnerability assessments, you use automated tools for a broad sweep of your systems, checking against a database of known vulnerabilities. This method is systematic, focusing on identifying what might be exploited.
Contrastingly, penetration testing involves a more dynamic approach. Here, you use automated tools and engage in manual, tactical probing. This method tests how vulnerabilities can be exploited in real-world scenarios, often requiring creative and critical thinking from a highly skilled cybersecurity expert to mimic potential hacker strategies.
6. Reporting
With vulnerability assessments, your report is more of a comprehensive list detailing the various vulnerabilities found in your system, often ranked by severity or potential impact. This report gives you a broad view of your security, highlighting areas that need attention.
In contrast, a penetration test report is much more narrative-oriented and detailed about specific exploits. It lists the vulnerabilities and describes how attackers could exploit them, the data they could access, and the potential damage each exploit could cause. This kind of report is invaluable for understanding the practical implications of each weakness.
7. Remediation Support
With vulnerability assessments, you receive a comprehensive list of potential security issues in your system, but the guidance for fixing them tends to be general. It's like getting a diagnostic report that identifies problems without specific instructions on mitigating each issue. DevSecOps platforms like Jit can add a specific suggestion to each finding, helping you solve each vulnerability more efficiently.
On the other hand, penetration testing offers more targeted remediation advice. Since pen tests actively exploit vulnerabilities, they provide detailed insights into each weakness and more specific, actionable recommendations on fortifying your defenses against similar real-world attacks.
| Vulnerability Assessments | Penetration Testing |
|---|---|
| Identifies and catalogs potential flaws in your system. | Actively exploit these weaknesses to test your system's real-world resilience. |
| Broad scope, surface-level analysis of various system components. | Narrow, in-depth focus on specific vulnerabilities or systems. |
| Systematic use of automated tools to identify potential exploits. | Dynamic, with manual and automatic processes approaches. |
| Regularly conducted throughout the development lifecycle. | Strategically timed, often post-major updates or feature launches. |
| Comprehensive list of vulnerabilities, usually ranked by severity. | Detailed narrative on how vulnerabilities were exploited and potential impacts. |
| Requires system access without disrupting operations. | Due to its intrusive nature, it needs higher access, often with explicit authorization. |
| General guidance on fixing listed security issues. | Specific, actionable advice based on how vulnerabilities were exploited. |
Balancing the Scales: Do You Need Both?
Deciding between a vulnerability assessment and penetration testing hinges on the current state and needs of your organization's cybersecurity. If you're just starting to shape your cybersecurity program or are unsure about your network's security status, a vulnerability assessment should be your first step.
You may not need pen testing as frequently if you have robust security tools and risk management workflows, like those offered by Jit, covering your entire SSDLC. But if it's been a year or more since your last penetration test, it's time to schedule another one.
Integrating both strategies into your security plan offers the most comprehensive protection, with assessments informing you about potential weaknesses and occasional pen tests validating your defenses against active threats.
Securing the Future with Jit
Vulnerability assessments and penetration testing are critical components of a solid cybersecurity plan. Ensure that you regularly review their scope and frequency to address all your security weaknesses and establish continuous monitoring so that all eyes are on your systems, even when no tests are running. To make security more manageable for your team, leverage security automation tools that cover every SSDLC stage and offer enriched reporting.
Jit’s DevSecOps platform brings together a range of best-in-class security tools, enabling you to easily integrate with these and manage them in your preferred environment. This type of orchestration makes security more comprehensive, as you can introduce new tools and controls into your CI/CD, but also much more seamless, as you can manage all solutions and get reporting and remediation guidance in a single platform. Explore more here.