7 Challenges & Solutions to Building a Modern (MVSP) Minimum Viable Secure Product
MVSP can reduce the risk of security breaches and potential loss of customer data. Therefore, investing in security can lead to a more successful and sustainable product. Here are some challenges and solutions to implementing this.
Updated February 28, 2024.
Collaborating with eleven global organizations, including the Australian Government and the National Security Agency in the US, CISA has developed a software security handbook, highlighting the pressing need for security in software development.
With cyber-attacks becoming more frequent and costly, businesses must establish a robust security posture to withstand the current threats. Waiting until 2027 to adopt human-centric security design practices, as predicted by Gartner, may be too late.
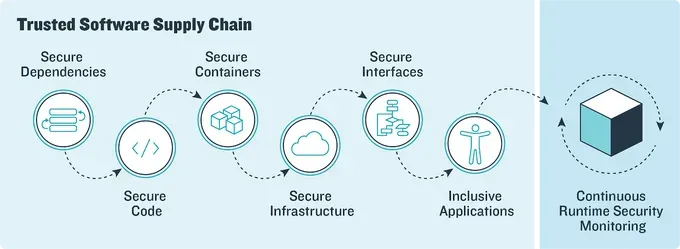
To address these challenges, the concept of the Minimum Viable Secure Product (MVSP) has been introduced. This approach prioritizes the development of a product with essential security features that safeguard its data and resources. This article explores the benefits of the MVSP approach and provides practical tips to overcome the challenges faced while implementing it.
What is a Minimum Viable Secure Product (MVSP)?
You might be familiar with a Minimum Viable Product (MVP)—a product with essential features to test the market. Similarly, the Minimum Viable Secure Product incorporates fundamental security measures to safeguard infrastructure and data and comply with regulations. In 2021, Google introduced its own MVSP checklist, setting a foundational security standard for developers.
This ensures that the ecosystem's products, codes, and libraries adhere to essential security practices. The checklist is a reliable developer starting point, even without extensive security expertise. Minimum Viable Security entails beginning with simple security measures and gradually enhancing complexity, just as one would approach any other product feature.
» MVSP is not to be confused with MVS: Here's what MVS is.
Minimum Viable Secure Product (MVSP) controls
While Google's MVSP checklist may not be a perfect fit for every product, it offers a generalized approach that suits most B2B software. The checklist comprises four essential security controls:
- Business controls Items include annual security testing for your product, compliance with relevant security standards such as ISO27001 and SSAE 18, and essential data protection such as the GDPR, PII and HIPAA protection, and NIST SP 800-88. Although the list may primarily focus on the US audience of software producers, the underlying principles apply regardless of your business's location or client base.
- Application design controls This list of rules applies to the design stage of your application. It involves patching any known issues with a severity of medium or higher, keeping meticulous logs, and protecting sensitive data in transit and rest using encryption. Also, have a password policy to apply a single sign-on, and use HTTPS to access your application.
- Application implementation controls This list pertains to the ongoing life of the application, addressing considerations for each sprint. It encompasses tasks like maintaining an up-to-date data flow diagram, prioritizing the resolution of application vulnerabilities within 90 days, and ensuring a fully scripted build with a generated provenance (SLSA level 1). In addition, proactively addressing well-known application vulnerabilities to prevent potential exploits. Adhering to these practices will help ensure your application's continuous security and robustness throughout its development lifecycle.
- Operational controls These controls focus on IT and operational security concerns for your application. They include all the basics of Cloud Identity Management, such as securing physical and logical access to your servers (or any other vital facilities), being transparent about third-party contractors using your data/API, and having a clear backup and recovery plan in case of disaster.
» Make sure you're on top of the IaC security essentials
Why build a Modern Minimum Viable Secure Product (MVSP) now?
Comprehensive SDLC (Software Development Life Cycle) security is crucial in today's threat environment. Like seeking a security expert's audit after completing your app or conducting penetration testing without considering security from the outset, neglecting security until your software is operational would be akin to closing the barn doors after the horses have escaped.
The CISA guide and the NIST 800-218 (SSDF) that preceded it make security one of the (if not THE) primary considerations when planning and building your app. Security transparency also helps build customer trust, which has been wearing thin lately with each company hiding information or misleading the public about significant security breaches they have suffered.
7 Challenges and Solutions to Building a Modern Minimum Viable Secure Product (MVSP)
If the information we've shared has piqued your interest and you are contemplating adopting an MVSP framework for your application's development, that's fantastic! However, before you proceed, it's essential to be aware of potential challenges and how to address them:
1. Accessing security risks
To effectively implement a Minimum Viable Secure Product (MVSP), it is crucial to possess a basic understanding of the potential security pitfalls, attack surfaces, and security gaps that may exist within your application. Additionally, you must be able to assess the potential risks associated with each vulnerability and prioritize their resolution accordingly.
If you find yourself unsure of where to begin or lack a security expert on your team, seeking the assistance of a security specialist can be highly advantageous. They can help you categorize and address potential issues and fixes.
While many security resources are available online, consulting with an expert during this critical stage is prudent rather than adopting an "it'll be fine" approach. Collaborating with a cybersecurity professional will enhance the security of your product and reduce the risk of overlooking important security considerations.
2. Balancing security and velocity
Balancing the urge to launch your product early to gain a competitive edge with the importance of security is critical. Rushing the development process can lead to severe issues, including costly refactoring and delays.
By prioritizing safety from the outset, you can avoid misconfigurations that may expose vulnerabilities and potential security breaches down the line. Proper security measures ensure a more robust and secure product, safeguarding your market share and reputation in the long run.
To strike a balance between speed and security, consider adopting the approach of MVS plans-as-code. Incorporate the desired security features based on pre-made plans into your regular R&D sprints. Building security into your product from day zero enables faster feature sprints and adaptability.
Jit's pre-made MVS for AppSec plan utilizes various security tools to streamline and expedite security implementation for your R&D team. This way, you can maintain a competitive edge while ensuring a secure and efficient product development process.
3. Identifying what tools to use
Setting up and integrating security tools into your development pipelines is a significant and ongoing task. The constant emergence of new threats requires regular reviews of your toolchain.
To optimize time and effort, the goal is to automate as much security work as possible by using code and managing it centrally within a framework with built-in security capabilities.
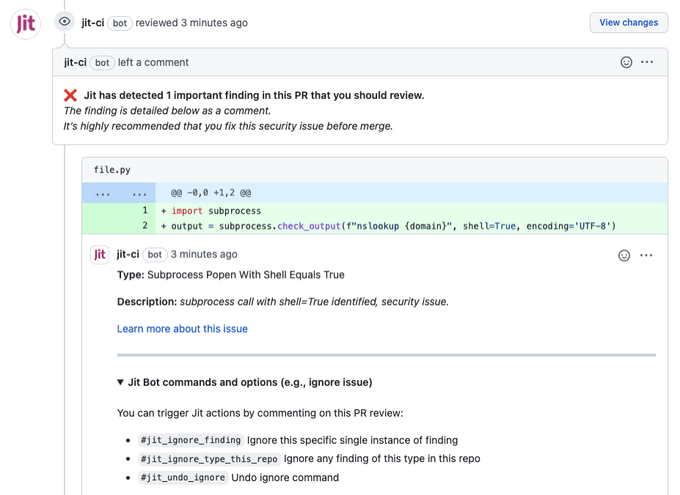
With Jit, you can achieve this streamlined approach. Jit combines a comprehensive array of security tools like KICS, Prowler, and npm-audit into a single platform, allowing you to work with them seamlessly using code within your GitHub development environment.
Additionally, Jit offers risk prioritization, enriched findings, and real-time suggestions for remediations, empowering you to manage security tasks and bolster your application's protection efficiently.
4. Comprehensive reporting
Comprehensive logging is a crucial aspect of the MVSP. However, using multiple tools can lead to overwhelming scattered information, making it challenging to identify meaningful and actionable insights.
Jit solves this problem by consolidating all the tool's logs into a single location, simplifying navigation and comprehension. This centralized approach ensures that your records and provenance meet the requirements for various regulations.
By establishing robust logging practices early on with Jit's assistance, you can effectively manage and access essential data, benefiting your product's security and regulatory compliance in the long run.
5. Thorough security testing
After implementing the security features per your plan, assessing their effectiveness is essential. Traditional testing is crucial, including unit and security tests on specific features.
However, to ensure continuous security validation, it's beneficial to incorporate security testing into your build pipeline. This way, every build and new version undergoes security testing automatically.
Tools like Semgrep or Bandit, which Jit seamlessly integrates with, are valuable for running scanning tests. These tools help uncover vulnerabilities within your code before it reaches production. Using such solutions gives you a comprehensive and detailed insight into your code's health, going beyond the tests you can write and run manually. This approach enhances your ability to identify and address potential security issues, bolstering the overall security posture of your application.
6. Lack of expertise and training
Many developers have a basic understanding of security issues but are far from security experts. The last thing you want is for a critical vulnerability to go unnoticed until your product reaches production.
Avoid such pitfalls through the following:
- Seek help from security experts when needed.
- Build a step-by-step implementation plan with a strong foundation.
- Take a systematic and careful approach to identifying and solving security challenges.
This slow and steady approach helps prevent burnout and allows developers to learn valuable security lessons.
By being cautious and methodical, you can enhance the security of your product and avoid potential risks that might have otherwise been overlooked. Prioritizing security throughout the development process and cultivating a security-aware culture within your team is essential. You can create a more robust and secure product for your users with the right approach and mindset.
7. Continuous security monitoring
Like the continuous nature of integration and delivery, security should also be an ongoing process. Continuous Security Monitoring (CSM) is a proactive approach that empowers organizations to detect and resolve security issues before they lead to any harm. By seamlessly integrating security tools and tests into their CI/CD pipeline, CSM enables swift and preemptive actions against potential threats.
The implementation of CSM can be simple. DevSecOps tools like Jit provide a user-friendly platform to integrate with diverse security tools and automate the monitoring process. This ensures complete visibility into each pipeline stage and offers detailed findings if any vulnerabilities are identified in real-time.
With DevSecOps tools like Jit, organizations can maintain a vigilant and secure development process, safeguarding their applications and data from potential risks.
» Check out these tips to foster continuous security.
Minimum isn’t maximum, but it’s a good place to start
At this point, you might be saying: “But I want more than the minimum! Why should I put in all this work to get the minimum result?”. However, Starting with an MVSP is a practical and essential step, even if you lack the resources or expertise for a comprehensive security audit plan or vulnerability assessment.
The MVSP approach lays the groundwork for enhancing security measures, serving as a stepping stone for implementing more robust security checkups, testing, and features in the future. Crafting a plan and executing it efficiently with the available resources and tools are the critical components of the MVSP approach.
Jit can help build your MVS by facilitating seamless integration with essential security tools, enabling efficient management and consolidation of their findings in a centralized location. Embracing MVSP and getting started for free by utilizing Jit's capabilities establishes a solid foundation for bolstering your product's security over time. This additionally contributes to a more robust and secure application.