Security as Code: 7 Building Blocks to Get You Started
Updated December 31, 2024.

It’s all up in the proverbial air as businesses and whole industries shift operations to the cloud with not nearly enough confidence in their ability to secure it. With a global cyber skill shortage and increasingly sophisticated attacks targeting software supply chains and cloud-based workloads, more infosec responsibilities fall on the shoulders of developers.
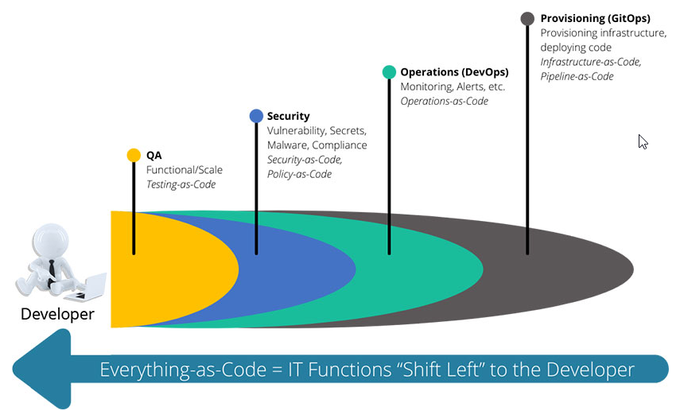
51% of businesses state that preventing cloud misconfigurations is their main cloud security priority for 2023. The trend of shifting left IT functions is fueled by transforming IT tools into developer tools - the codification of everything. One of the functions that’s shifted left is security.
Security as Code offers to streamline DevSecOps to address potential risks and vulnerabilities as early as possible in software development. This article defines what Security as Code means, how it works, why you need it, and the seven key components you should consider when integrating SaC.
What is Security as Code, anyway?
Security as Code is a foundational element of continuous security. It involves building security into DevOps tools and workflows by mapping out how changes to code and infrastructure are made, and identifying where you can include security checks, tests, and gates. All without introducing unnecessary costs or delays. McKinsey describes it as the most effective approach to securing cloud workloads with speed and agility.
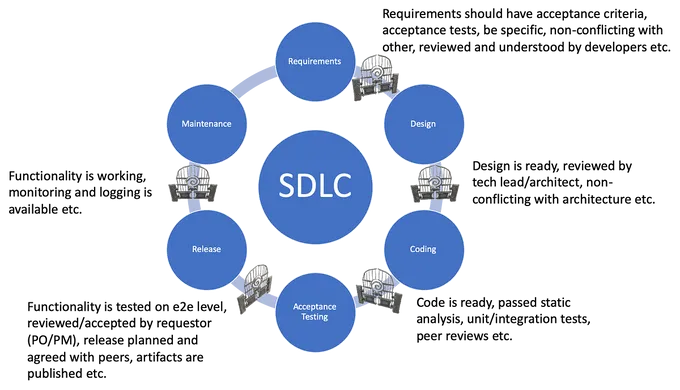
Let's look at it from a broader perspective and consider the trend of codifying everything that stemmed from introducing Infrastructure as Code in DevOps practices. It’s pretty clear that Everything-as-Code practices and methodologies are seen as fancy buzzwords for different types of automation in software development processes. This includes Security as Code. Therefore, a simple way to define SaC would be: a methodology for automating security measures in the software development lifecycle (SDLC).
What are the key components of Security as Code?
One common misconception about SaC is that it is another name for DevSecOps. However, SaC focuses on three specific components of the DevSecOps framework:
Security Testing
Security testing automation in DevSecOps means codifying the process of identifying and mitigating software vulnerabilities in code - including application code and infrastructure. The focus of security testing strengthens the CIA triad of an application: its confidentiality, integrity, and availability. Security testing also helps uncover accidental malfunctions, common misconfigurations, and unintentional exposure of sensitive information (like code secrets) and prove compliance with regulations such as SOC2.
Vulnerability Scanning
Often confused with security testing, vulnerability testing focuses on exploitable weaknesses in your application and cloud infrastructure that malefactors can leverage in an attack. Vulnerability scanning in SaC practices entails employing tools like OWASP ZAP to scan your code and its dependencies for known vulnerabilities and offer insights on how to remedy them.
Vulnerability scans can help you quickly identify, prioritize, and resolve common vulnerabilities like cross-site scripting (XSS) and SQL injection attacks. Jit’s DevSecOps orchestration platform lets you easily integrate security testing and vulnerability scanning into your CI/CD pipeline by leveraging and automating various open-source security tools.
Access Control and Policy Management
Access control and policy management are critical Identity Governance and Administration (IGA) components. Access control specifies and limits user or service access to specific application data, resources, or functionalities. At the same time, policy management enables businesses to simplify how access is granted, denied, or revoked, making it easier to track who is accessing what and update access controls as user needs change. Automating these processes enables dev teams to focus on functionality while adhering to IAM best practices.
Why Security as Code is vital for DevSecOps
Since Security as Code entails the automation of security assurance processes within the CI/CD, it is at the core of DevSecOps practices. The only way to shift security left is to define the requirements when starting a project and codify the processes for consistent, repeated use and reuse.
With code security codified and integrated throughout the SDLC, you can empower developers to deliver secure code in a self-service approach with zero impact on development velocity. In addition, DevOps engineers and developers are bound to feel right at home with SaC tools and practices since many are already proficient at managing infrastructure as code in cloud-native environments.
Last but not least, the codification of security policies provides an opportunity for collaboration between DevOps and InfoSec teams in designing the policies to align with regulatory demands and organizational data privacy policies.
Security as Code: 7 Building Blocks to Get You Started
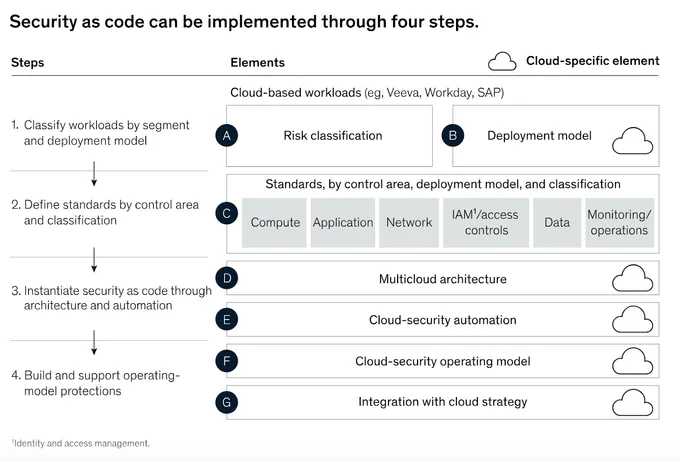
There are numerous ways to approach the integration of SaC into your SDLC, and how you approach it depends significantly on the needs of your organization, the application, and its users. For example, the McKinsey model for SaC implementation considers cloud-native workloads and has only four (very complex) steps.
Regardless of your cloud maturity level or organization size, here are seven building blocks for a successful Security as Code implementation:
1. Define the scope and security requirements
Understand your security requirements first. Before you consider how to approach Security as Code, it’s crucial to map out, classify, and define the level of security required for all cloud-based and on-prem assets, libraries, and third-party tools used in your SSDLC. With new projects, ensure that the planned application and infrastructure architecture align with your requirements for SaC implementation.
2. Ensure continuous feedback loops
Build a process where actionable and insightful feedback is delivered to the developers as quickly as possible to address potential security risks as soon as they appear. Automating testing and scanning, introducing Policy as Code throughout the CI/CD, implementing continuous monitoring, and integrating feedback directly into the development environment make it easier to establish effective feedback loops.
3. Automate security scans and tests
Developers don’t like writing and executing tests and traditionally opt to push bugs and security vulnerabilities down the pipeline to QA, making resolving each issue more costly and time-consuming. One of the critical components of SaC is the codified automation of testing and scanning.
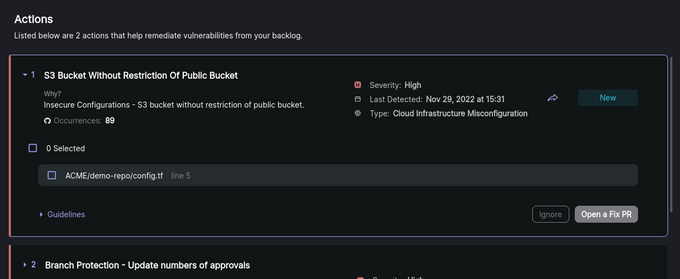
Adding automated pentesting, SAST, and DAST to your pipeline reduces human involvement and saves resources. Jit integrates various open-source security tools, such as Semgrep for SAST and OWASP ZAP for DAST, into your CI/CD, covering every pipeline stage. All tools run automatically for every new PR, and you also receive automatic alerts, enriched findings, and remediation suggestions on a single platform. For example, the Actions page suggests solutions to remediate vulnerabilities from your backlog promptly:
4. Standardize and reuse
Most businesses don’t focus on developing one application alone. Even SaaS businesses that ship a hosted application tend to have microservice architectures composed of many owned and third-party codes. With SaC, you can reuse patterns and templates across multiple projects, codebases, and applications, saving time in preparing a cybersecurity envelope from zero for every new project.
5. Monitor logs for irregularities and violations
Integrating monitoring and automated “red flag” alerting helps you stay on top of predefined policy violations. In addition, logging is essential for maintaining an audit trail that may be necessary for regulatory compliance. It helps maintain accountability and traceability for all operations involving the security of the application, its code, and its infrastructure.
6. Build checks and gates into automated policies
You can’t fully trust machines when protecting sensitive information and code secrets from human error. Therefore, you must build relevant reviews and gates into the process to enable you to evaluate security policies for any application, in any environment, and at any stage of development.
7. Promote secure coding practices
Developer collaboration and buy-in are the most critical and challenging building blocks of a successful SaC implementation. SaC helps bridge the gap between information security teams with the teams of developers and DevOps engineers by “translating” security policies into code developers can read, understand, and write. However, it’s up to you to prioritize security for DevOps teams and developers while providing them with the knowledge and tools to practice secure coding continuously.
Orchestrating Security as Code with Jit
Getting started with codifying security policies and automating DAST, SAST, and pentesting may sound daunting. It can be if you start from zero and find yourself jumping over the moon in slow motion - taking time to select and integrate tools and processes, only to discover you’ve missed essential gaps while extending your cybersecurity envelope beyond what is needed.
With Jit, you can automate and orchestrate Security as Code in one dev-friendly environment, enabling you to easily and quickly customize trusted open-source security tools to your requirements. Jit automates testing at all the stages of development, understands your applications’ security posture, and creates your own customized Security as Code protection plan. Start for free,