12 Pros and Cons of Microsoft (Azure) Sentinel
Updated September 17, 2024.

Let’s keep it real: security compliance often makes your DevOps team feel strained. This burden spans multiple security sub-domains, such as information, network, and endpoint security, and specific security configurations, such as Identity and Access Management (IAM).
Restraining budgets and ambitious expansion plans make it even more tempting to brush security under the rug until it becomes a challenge too big to ignore. With 71% of companies using Microsoft Azure to run at least some workloads, this leading cloud provider is taking matters into its own hands - enabling automated threat intelligence for its users.
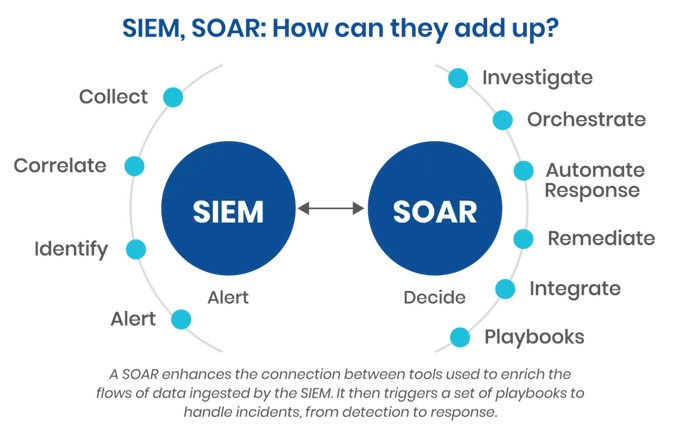
Microsoft Sentinel, previously known as Azure Sentinel, is a cloud-native security intelligence platform for the Microsoft Azure cloud. It manages the entire spectrum of Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) workflows to manage and mitigate security threats across the enterprise.
This article will uncover the trade-offs of Microsoft Sentinel to help you understand its value proposition and additional considerations to improve the security posture for enterprise-wide workloads.
12 Pros and Cons of Microsoft Sentinel
The 6 Pros of Microsoft Sentinel
1. Easy integrations with Azure services
Microsoft Sentinel integrates seamlessly with Azure security services to capture data. For example, you can capture syslog data from the VMs using the Azure Monitor agent. This data is forwarded to Azure Log Analytics workspace and ingested into Microsoft Sentinel.
Similarly, you can integrate other Azure services that provide event and diagnostics logs about the Azure platform for possible security impacts, such as Azure Activity Log and Azure Event Hub. It also supports integrations with a multi-tenant deployment via Azure Lighthouse.
2. Fully Cloud Native architecture
Microsoft Sentinel is built on cloud-native architecture. The platform is immensely scalable to handle massive amounts of data and analytics. It is also elastic to ensure optimum utilization of resources based on the demand at a given time.
3. Centralized monitoring
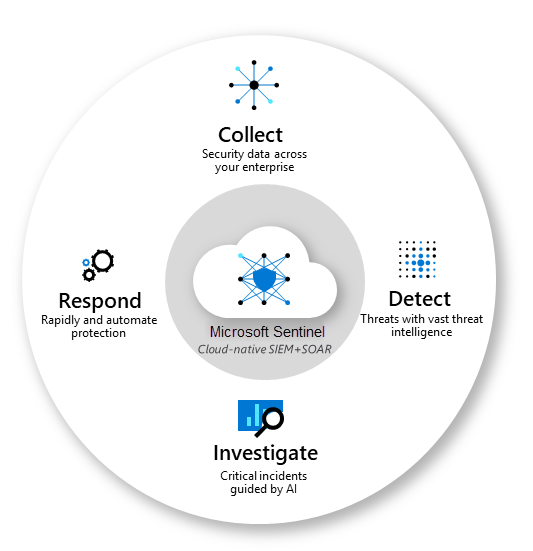
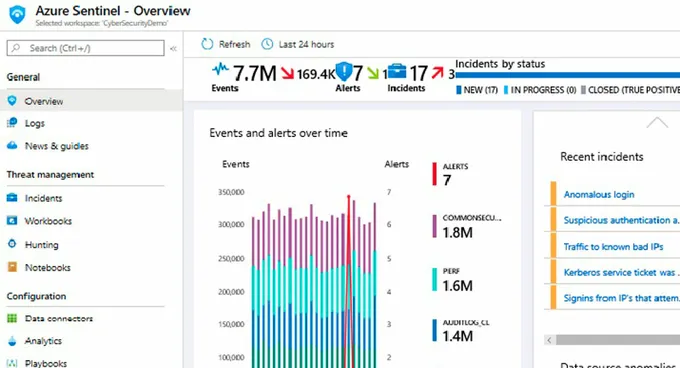
Microsoft Sentinel is an umbrella platform providing security visibility across the entire enterprise. It ingests security data from all enterprise workloads to manage the security incident analysis workflow, from detection to remediation, helping you implement continuous security across your cloud. On top of that, it supports AI-powered threat intelligence and a rules engine to detect and investigate critical incidents.
Overall, Microsoft Sentinel offers you a bird's-eye view across the enterprise, alleviating the stress of managing security attacks, increasing alerts, and extending resolution time frames.
4. Automated Incident Response
Azure Sentinel uses playbooks for automated response to threats. A playbook is a collection of procedures that can be run from Azure Sentinel in response to an alert. It is a way to automate responses to a specific type of security incident. Azure Sentinel’s playbooks are based on Azure Logic Apps, meaning they can interact with various services and systems.
5. High Customizability
Microsoft Sentinel presents immense customizations across all security incident handling workflow stages. Some of the critical customization options include:
- Data Connectors: It offers a host of internal and external data connectors, including Microsoft and Azure service connectors, vendor-specific connectors for ingesting data from external hardware and software, and supports the creation of custom data connectors using third-party tools.
- Custom Analytics Rules: It enables the creation of custom analytics rules to help discover threats and abnormal behaviors in any deployment environment.
- Custom Playbooks for Incident Management: Microsoft Sentinel can be customized for incident response handling. It can build automated, templatized responses, from simple actions like sending an email to more complex procedures involving settings changes in accounts or environments.
6. Real-time advanced threat detection
Microsoft Sentinel can detect real-time threats thanks to its near Real Time (NRT) analytics rules. It provides highly responsive threat detection by running its query at intervals just one minute apart.
This feature is further augmented with support for advanced multistage attack detection using Fusion. Fusion is a correlation engine based on scalable machine-learning algorithms that work with Microsoft Sentinel to automatically detect advanced persistent threats that are otherwise very difficult to detect.
The 6 Cons of Microsoft Sentinel
1. Dependency on Microsoft software and cloud
Like every platform hosted on a cloud service provider, Microsoft Sentinel also suffers from the drawback of vendor lock-in. Being a Microsoft product, it works seamlessly with Microsoft Azure cloud services. However, the support for third-party cloud services becomes very complex to manage, making security orchestration a painful process.
2. Cost Considerations
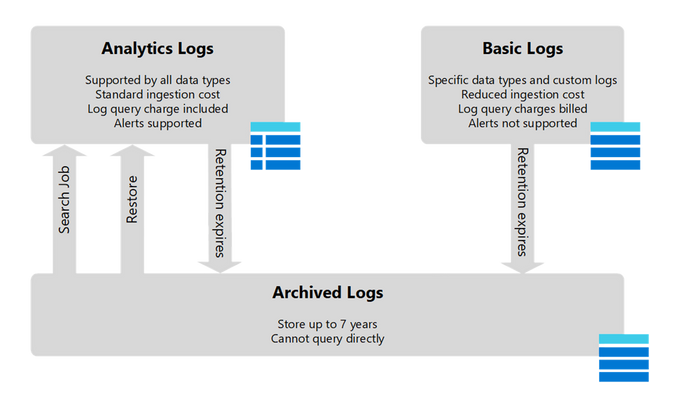
Microsoft Sentinel's pricing is based on the ingested data volume and data processed for log analytics. Both are measured in GB, and the pricing is structured in tiers with increments of 100 GB. Unless appropriately moderated, the costs can escalate, nearly doubling the bill with every 100 GB of additional data. However, Microsoft Sentinel offers a Pay-as-you-go tier, which is charged per GB basis, along with a free trial of 31 days.
3. Difficulty in data ingestion and parsing logs
Microsoft Sentinel offers many Microsoft and partner-supported data connectors and community-authored connectors. However, for ingesting data from non-supported sources, Microsoft Sentinel relies on third-party tools, such as Codeless Connector Platform (CCP) for SaaS and Logstash for on-premise or cloud-hosted infrastructure. It becomes increasingly complex to integrate with these sources due to the configurations and settings that must be maintained to make the connector work.
Also, Microsoft Sentinel log analytics works on Kusto Query Language (KQL), which differs from the widely adopted SQL and entails some learning curve.
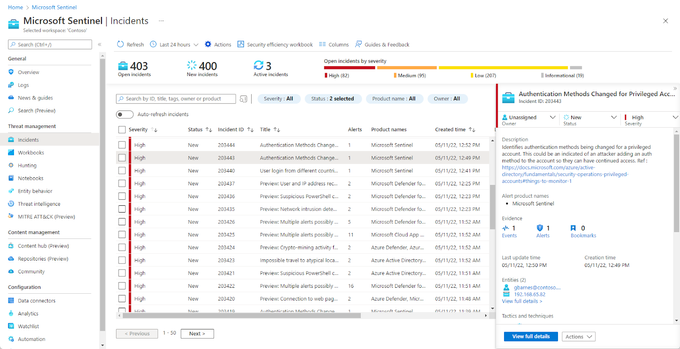
4. False positives generation
Like any security analysis platform, you need to tune Microsoft Sentinel progressively to reduce the number of false positive alerts. This process is time-consuming and requires ongoing effort as the enterprise’s environment and threat landscape evolve.
5. Complexity in fine-tuning analytics
While machine learning-powered threat intelligence can significantly reduce the cases of false positives, there are constantly evolving trends in cybersecurity that manifest in the form of unknown vulnerabilities. Keeping the Microsoft Sentinel platform updated on the newer threats requires importing external threat intelligence feeds, an ongoing effort involving additional integrations, and fine-tuning. It may incur additional costs if the threat intelligence feeds are from paid, third-party services.
6. Reporting Friction
Microsoft Sentinel offers several built-in dashboards, but these are basic. There is an option to build custom dashboards, which also entails building KQL scripts leading the frictions in custom report generation. Time-consuming report creation due to complex KQL queries involving significant data manipulation exacerbates this problem. Reporting friction also applies to building custom workbooks and notebooks within Microsoft Sentinel.
What do you need from a SOAR and SIEM solution?
As a full-cycle security intelligence solution, Microsoft Sentinel offers a feature-rich platform for managing SOAR and SIEM-related workflows. However, it has some limitations, like most of the standard SOAR and SIEM platforms. For one, it focuses on operational security. That is the security posture of a deployed application or workload while under operation. Secondly, it is intricately tied to the Azure ecosystem.
Considering that many of the security vulnerabilities are due to anomalies discovered within the source code of an application, it makes more sense to enhance the security posture to consider developmental security risks, such as code, pipeline, runtime app, and API security.
Therefore, a strong SOAR and SIEM platform like Microsoft Sentinel requires a robust DevSecOps process integration to gather threat intelligence across the SDLC (software development lifecycle). With Jit, you can effortlessly embed security controls across the DevOps pipeline and make the reports available on Microsoft Sentinel to expand the security posture of self-developed applications.
Another consideration for SOAR and SIEM is multi-could deployment. Most enterprises would want to spread their workloads across multiple cloud service providers as an essential risk mitigation measure to guard against service outages. Considering the close coupling of Microsoft Sentinel with Azure Cloud and the limited support for ingesting data from other cloud providers - you need additional security tools to protect your system across providers.
With tools like Prowler, it is possible to perform security audits on other cloud services like AWS and GCP and integrate the audit reports with Microsoft Sentinel to increase its scope across multi-cloud deployments.
Additionally, with the rise of the Infrastructure as Code (IaC) approach to deployment, many security vulnerabilities also emerge in the infrastructure misconfiguration. KICS is one of the popular open-source tools for auditing IaC configurations to report security vulnerabilities and compliance issues. By ingesting data from Prowler and KICS into Microsoft Sentinel, you can expand the horizon of its SOAR and SIEM capabilities to manage the security landscape for enterprises, covering multi-cloud infrastructure.
Jit enables you to deploy security tools such as Prowler and KICS easily. However, by deploying with Jit, the developer experience is streamlined to offer the broadest possible coverage for security posture and help you leverage the power of Microsoft Sentinel. Get started for free.