Pulumi vs. Terraform: The IaC Showdown
Updated March 5, 2024.

Remember the days of manual infrastructure provisioning before Infrastructure as Code (IaC) tools existed? Hours upon hours wasted on managing and configuring on and offsite infrastructure deployments? How about the high costs, manual errors, security vulnerabilities, and limited stack scalability that came with it?
These are unpleasant memories for DevOps and site reliability engineering (SRE) practitioners. So it’s no wonder IaC solutions have become vital for cost-effective cloud engineering as organizations transform and grow their infrastructure stacks. Driven by the mass migration of enterprises to the cloud, the infrastructure as code market size is projected to grow from 0.8$ billion in 2022 to 2.3$ billion by 2027.
Two of the most popular IaC tools for provisioning, managing, and configuring infrastructure at scale by using code are Terraform and Pulumi. Both open-source solutions offer similar features and functionalities for managing your virtualized infrastructure. However, when choosing the right solution for your IaC needs, it’s essential to understand the unique benefits and limitations.
Terraform by Hashicorp
Hashicorp’s Terraform, released initially in 2014, enables infrastructure automation to provision, comply, and manage almost any cloud, data center, and service. It is an open-source IaC solution that uses declarative configuration files written in HashiCorp’s Configuration Language (HCL) to let you define your desired infrastructure state and automate its application.
Terraform can provision low-level cloud and on-premises infrastructure components, including networking, computational resources, storage, and higher-end resources like DNS entries across multiple providers and SaaS features.
Terraform employs Terraform Providers to create and manage resources across all popular cloud platforms through the platforms’ APIs. In 2019, Terraform introduced the paid version called Terraform Enterprise for larger companies with complex IaC needs.
Why choose Terraform?
The main benefits of Terraform stem from its age on the market - the platform has extensive documentation, as well as an avid community. Terraform offers a broad range of resources for provisioning and managing diverse and complex infrastructure deployments.
Terraform’s developer community makes it easy to find and use ready-made code in its registry of Terraform Modules to automate the provisioning of almost any type of infrastructure.
A proven and robust solution for large organizations, Terraform offers scalability, reliability, and stability to those willing to learn the DSL (domain-specific language) required for advanced functionality - HCL.
Pulumi
Launched in 2018 by a company under the same name, Pulumi dubs itself an Infrastructure as Code solution for engineers. An open-source tool for designing, deploying, and managing cloud resources, Pulumi offers support for more than 60 public, private, and hybrid cloud providers.
With Pulumi, you can configure your cloud infrastructure in your preferred programming language (TypeScript, Go, .NET, Python, and Java) or markup language (YAML, CUE).
Why choose Pulumi?
The main advantage of Pulumi is its flexibility and ease of use. With support for the most popular programming and markup languages, Pulumi lets you write and reuse code without learning a new language to write your infrastructure configuration files and tests.
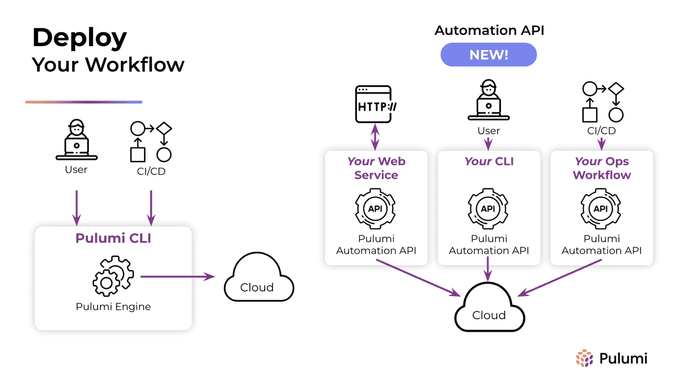
In addition, Pulumi claims that its Automation API is the industry's first and only fully programmable infrastructure-as-code technology. The Pulumi Automation API lets you embed Pulumi into your application code to execute your deployment workflows programmatically and, according to the company, scale 10x the amount of infrastructure managed per engineer.
It’s also worth mentioning that in terms of CI/CD security, Pulumi offers built-in secret and state encryption, policy enforcement, complete change visibility, and comprehensive infrastructure auditing.
The IaC Showdown: Terraform vs. Pulumi
Now that we’ve introduced our competitors, it’s time for the showdown, drilling down into the specifics of each category. It’s worth noting that because both tools are open-source and increasingly popular with infrastructure engineers and DevOps practitioners, their features and capabilities morph and evolve to serve the needs of their respective communities.
Core functionality and features
The common goal of both tools is to provision infrastructure, but they have slightly different approaches to achieving it.
Tool paradigm
Both Terraform and Pulumi are essentially declarative tools. However, while Terraform automatically generates the infrastructure based on the written code, Pulumi demands that you write code that implicitly describes the infrastructure deployed and turns imperative code into a declarative graph.
Language support
Terraform configuration must be written in HCL / JSON. Pulumi offers flexibility by supporting Python, TypeScript, JavaScript, Go, C#, F#, Java, and YAML.
That said, it is possible to make Terraform use familiar programming languages to let you define and provision infrastructure with the Cloud Development Kit for Terraform (CDKTF) that adds support for TypeScript, Python, Java, C#, and Go.
State management
The state in IaC tracks the metadata of the cloud infrastructure. Pulumi and Terraform take different approaches to state management in cloud resource provisioning.
With Terraform, the state is self-managed and stored in a local file named “terraform.tfstate.” This file can be hosted locally or on your cloud platform of choice. If you want to offload the worries of hosting your tfstate files, you can subscribe to Terraform Cloud, Hashicorp’s SaaS subscription.
Pulumi, on the other hand, employs a backend Pulumi Service by default. It can be self-hosted or cloud-based and even self-managed like Terraform. In it, the desired state can be expressed with code in general-purpose languages and shared across teams.
Debugging and testing
Terraform supports integration testing through third-party tools (Terratest and Kitchen-Terraform), unit tests, contract tests, and end-to-end testing with HCL.
With Pulumi, you can use general-purpose programming languages to write your tests or employ native testing frameworks to perform automated tests of your infrastructure. Pulumi provides unit tests, property tests, and integration tests.
Unique features
Terraform allows for the provisioning of third-party and custom applications, while Pulumi emphasizes the capabilities of its automation API.
Licensing & costs
Terraform uses Mozilla Public License 2.0, while Pulumi open-source projects use Apache License 2.0. Both Terraform and Pulumi offer a free tier for their service and subscription services for enterprises.
Integrations & compatibility
Having a tool that doesn’t play nice with other tools in your pipeline is more of a hindrance than a benefit. Terraform and Pulumi offer extensibility, support for templates, and import and export of your IaC configuration files. However, they take slightly different approaches to integration and communication with cloud service providers.
Provider support
Pulumi supports over 60 cloud providers and cloud SaaS offerings and has native providers for AWS, Azure, Google, and Kubernetes that enable same-day support for new releases directly from the CSP’s API. With Terraform, the community usually supplies support for cloud provider APIs, so it may take longer to become available to the general user base.
One of the advantages of Pulumi in this context is its integration with Terraform Providers, which allows Pulumi to cover all Terraform cloud providers. This integration lets you combine Terraform and Pulumi to make the most of your infrastructure management.
Adopting existing resources
Both Pulumi and Terraform support importing infrastructure, but Pulumi sets itself apart by generating the code to match the imported resource. Terraform only supports importing state and requires you to edit the configuration in HCL manually.
Security
Misconfigurations and exposed code secrets are among the most common causes of breaches and abuse of vulnerable cloud infrastructure. Regardless of the IaC tool you choose, you must take steps to secure it as part of your CI/CD. Learn more about using the open-source KICS tool as part of your DevSecOps Jit security plan.
Policy-as-code
Both solutions offer policy-as-code functionality. Pulumi offers its free, open-source CrossGuard framework, whereas Terraform employs Sentinel, a closed-source solution limited to Terraform Enterprise and Terraform Cloud subscriptions.
Secrets and encryption
By default, Terraform stores all secrets in plain text in the tfstate file, visible to anyone with access to it. To protect your code secrets, you can manage your secrets through Vault, a separate Hashicorp product. However, it’s worth noting that when pulled from the Vault, secrets in Terraform are still stored as plain text.
Pulumi takes a more proactive approach to secret protection by encrypting all secrets during transmission and storage. Pulumi also supports encrypting sensitive values like database passwords, SaaS tokens, and credentials files for added security.
Developer experience
While Terraform is geared more toward DevOps practitioners, Pulumi is a tool aimed at platform and cloud engineers. Regardless of your role in your team and organization, ensuring that the tool you use is comfortable and compatible with your workflows and has the community and documentation to help you if you encounter any challenges is vital.
IDE support
Terraform can be integrated with your IDE of choice through community-supplied plugins. In contrast, Pulumi offers robust IDE support for commonly used IDEs (Visual Studio, JetBrains IDEs, and more) due to its support for standard programming languages in IaC configuration and provisioning.
Pulumi lets you do everything without leaving your IDE, including code completion, strong typing, error squiggles, and rich resource documentation. With Terraform’s HCL, you will have no choice but to turn to documentation resources and DSL syntax references.
Ease of use & learning curve
Because of its built-in support for standard and common programming languages, Pulumi is far easier to adopt, learn and integrate with your CI/CD pipelines. Yet, Terraform is still considered very easy to master with its human-readable HCL and 3p support.
Documentation
Having detailed and comprehensive documentation is critical for successfully implementing any solution. Terraform has a slight advantage in breadth and scope because it has been around longer. However, Pulumi is very aware of this, so they’ve invested heavily in recent years in expanding and optimizing their knowledge base.
Community
When documentation and reference don’t supply the answers or resources you need, it’s up to the user and developer community to pick up the slack. Terraform has a massive and established community, while Pulumi’s is still growing but very active across discussion forums and StackOverflow questions and answers.
Which should you use in 2023: Pulumi or Terraform?
The choice comes down to the requirements of your application and of those working with the tool. When choosing between Terraform and Pulumi, the answer might be, as the known meme says: “Why not both?”
Suppose you want to make the most of your infrastructure management and aren’t deterred by the additional effort initially required to integrate both tools. In that case, you can benefit from the strengths of Pulumi and Terraform.
With Pulumi, you can consume both local and remote Terraform states and use Terraform for subsets of your virtual infrastructure. So, for example, you can keep low-level network definitions in Terraform and employ Pulumi for high-level infrastructure design.
Regardless of the solution you implement for IaC, it’s important to remember that neither tool was built to protect and secure your codified infrastructure. So as you integrate IaC into your workflows, be sure to complement it with IaC security.