Compare the Top 10 SAST Tools for Maximum Code Security
Static application security testing (SAST) tools are essential for detecting vulnerabilities early in the development process. By integrating SAST into your workflow, you can catch security flaws before they reach production. Choosing the right tool can be challenging, so here are the top options and their best use cases.
Updated September 15, 2025

AI Summary
In Code Complete (1993), Steve McConnell emphasized writing code for people first and computers second to improve readability. At the time, cyber threats were nearly non-existent. Fast forward to today, developers face a greater challenge—writing code to defend against hackers first and users second.
This challenge is amplified by rising cybersecurity incidents stemming from insecure code. With an average of 21 minutes needed to fix a single vulnerability, manual remediation is unsustainable. Static application security testing (SAST) tools address this by automating code analysis, detecting vulnerabilities early, and enabling developers to write secure code from the start.
» Not sure about SAST? Compare SAST vs. DAST
10 Best SAST Tools for Securing Your Custom Code at a Glance
- Best overall: Jit
- Easiest to get started: Semgrep
- Best reporting: BlackDuck Coverity
- Best for Go developers: Gosec
- Best for small teams: Codiga
- Best for large codebases: SonarQube
- Best for companies with larger budgets: Snyk
- Best for cloud-native security: Spectral
- Best AI-powered SAST tool: DeepSource
- Best for multiple integrations across CI/CD and SCM tools: Checkmarx SAST
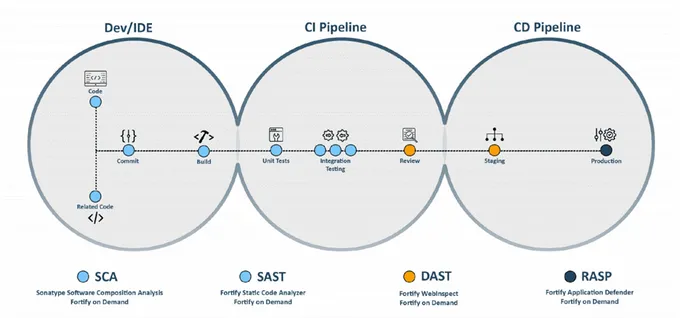
How Static Application Security Testing (SAST) Works
SAST verifies the source code of software to unearth possible security vulnerabilities and loopholes that could be later exploited at runtime. Unlike DAST tools, which simulate attacks from the outside in, SAST is a white-box testing method that integrates within the developer workflow and periodically scans the source code.
These scans happen in multiple ways. For example, a developer can run the SAST scans within the IDE or trigger them as code commit operations on the version control system or DevOps pipeline.
The SAST approach complements testing and vulnerability scanning methods such as DAST and software composition analysis (SCA). Each tool addresses different security aspects at different SLDC stages, so they should work together as part of a robust and scalable application security testing strategy.
Critical Vulnerabilities Detected by SAST Tools
- Cross-site scripting (XSS)
- Buffer overflows
- SQL injections
- Insecure cryptography
- Broken authentication
- Vulnerable and outdated components
Key Features to Look for in SAST Tools
- Programming language support: Ensure the tool supports all programming languages your team uses to prevent security gaps in your codebase.
- CI/CD & IDE integration: Choose a tool that integrates seamlessly with CI/CD pipelines for automated scans and provides real-time security feedback within IDEs.
- Rule sets & vulnerability classification: A strong SAST tool should have a comprehensive rule library for detecting common security flaws and integrate with databases like OWASP and CVE.
- Remediation guidance: The tool should offer actionable, real-time remediation suggestions to help developers fix vulnerabilities as soon as they are identified.
- False positives rate: High false positives create unnecessary work; instead, opt for a tool that minimizes noise and prioritizes genuine security risks.
Top 10 SAST Tools for Maximum Code Security
Beyond Code Quality: Why Do You Need a SAST Tool?
A SAST tool does more than just find vulnerabilities—it streamlines the entire security workflow, from detection to remediation. It also scans infrastructure as code (IaC) and dependent modules to ensure complete security coverage. By automating security-as-code practices, SAST enforces security rules and minimizes human error.
Key Benefits of SAST
- End-to-end security workflow: Detect, report, and remediate vulnerabilities efficiently.
- Expanded security coverage: Scans IaC configurations and dependent modules.
- Automated security enforcement: Codifies best practices and prevents critical risks.
- Faster, safer development: Reduces manual code review efforts without slowing teams down.
» Learn how IaC security can protect your applications from vulnerabilities
Shift Left Your Application Security Checks with SAST
“Shift left” is more than a strategy—it's a proactive approach to embedding security within development rather than leaving it for later stages. Integrating SAST early fosters a security-first mindset, reducing risks before they escalate.
With cyber threats growing more sophisticated, adopting SAST is no longer optional—it’s essential for maintaining secure, reliable software. Jit empowers dev teams to seamlessly integrate SAST and other security tools across the entire SDLC, simplifying security processes without slowing development. Start securing your code today.