Full-Stack Product Security Scanning with Jit’s built-in scanners
Unify every layer of your product security — from code to cloud — in one platform that detects, validates, and remediates real risks with AI Agents.
Book a DemoLanguage & Environment Support
Static Application Security Analysis (SAST)
Software Composition Analysis (SCA)
IaC Security
Scanning
Scanning
Secrets
detection
detection
Serverless + K8s Cluster Scanning
Dynamic Application Security Analysis (DAST)
Cloud Security Posture Management (CSPM)
CI/CD Misconfiguration Detection
Container
Scanning
Scanning
OSS License
Scanning
Scanning
Software Bill of Materials (SBOM)

Detect a broad range of issues in all common environments
Language Support
Including Javascript, Typescript, Java, Python, Go, Rust, Ruby, Swift, Scala, PHP, Kotlin, C, C#, C++, and more.
Cloud and IaC support
Coverage for AWS, Azure, GCP, Terraform, Pulumi, AWS CDK, K8s manifest files, K8s clusters, Helm Charts, serverless manifest files, and more.
IDE, SCM, CI/CD and Container Registry Support
Scan code in GitHub, GitLab, BitBucket, Azure DevOps, VS Code, Cursor, and IntelliJ. Integrate scanning with GitHub Actions, GitLab CI/CD, Jenkins, CircleCI, AWS ECR and more.
Detect code security flaws with Static Application Security Testing (SAST)
Daily scanning detects a wide range of code security flaws
Activating Jit SAST continuously scans your codebase for security flaws, which are analyzed by Jit’s AI Agents to filter false positives, provide proof of exploitability, auto remediate issues, and automate ticketing/SLA management.
Integrate continuous SAST scanning for every code change in the developer environment
Developers never need to leave their environment for immediate SAST results for every code change, which are explained in plain english and in the context of their environment with auto remediation to resolve issues quickly.
Detect a wide range of code security flaws
Including injection vulnerabilities, buffer overflows, XXS, SSRF, CSRF, broken authentication flows, weak or missing encryption, sensitive data exposure, unsafe logging practices, and many more.
Detect open source security risks with Software Composition Analysis (SCA)
Continuously monitor open-source dependencies for known vulnerabilities
Jit’s SCA scanner continuously tracks vulnerabilities across all open source packages and dependencies, enriched by AI validation to focus on reachable CVEs with direct dependencies — focusing triage on exploitable issues with easy fixes.
Detect vulnerable or outdated dependencies before release
Embedded in your CI/CD workflow, Jit’s SCA runs automatically with every PR, providing developers with clear, contextual feedback and safe version or patch recommendations before code reaches production.
Correlate CVEs across multiple authoritative databases for wide coverage
Jit’s SCA correlates data from multiple trusted sources — including NVD, GitHub Security Advisories, and OSS Index — to accurately match CVEs to the relevant open-source components in your codebase.
Detect infrastructure security issues early with IaC Scanning
Continuously detect misconfigurations and security drift across cloud environments
Jit’s IaC scanner continuously analyzes Terraform, CloudFormation, Helm, and Kubernetes manifests to identify misconfigurations and insecure defaults — catching risks like overly permissive IAM roles, open security groups, and unencrypted resources before deployment.
Integrate IaC scanning directly into developer workflows
Developers receive real-time IaC findings in their IDE or CI/CD pipeline with clear, contextual explanations and auto-remediation guidance — ensuring issues are resolved early without breaking deployment velocity.
Validate findings against real cloud context for accurate risk prioritization
Jit’s AI Agents correlate IaC misconfigurations with live cloud data from integrations like AWS, GCP, and Azure, confirming whether detected issues are actually exploitable.
Flag hard-coded secrets with Secrets Detection
Continuously detect hardcoded secrets across code, configs, and pipelines
Jit’s Secrets Detection scanner continuously monitors repositories, config files, and CI/CD pipelines to identify exposed API keys, credentials, and tokens — before they can be committed or pushed to production.
Integrate real-time secret scanning into every developer workflow
Secrets are detected instantly as developers code or commit, with inline feedback and auto-remediation guidance to revoke and rotate credentials quickly — without leaving their environment.
Correlate detected secrets with cloud and runtime context for true risk validation
Jit’s AI Agents validate whether exposed secrets are active and accessible in the environment, cross-referencing cloud integrations and identity providers to prioritize real risks and eliminate false positives.
Detect application vulnerabilities in runtime with Dynamic Application Security Analysis (DAST)
Continuously detect misconfigurations and security drift across cloud environments
Jit’s DAST scanner dynamically probes your live web applications and APIs to uncover exploitable vulnerabilities in real runtime conditions, such as injection flaws, authentication weaknesses, and misconfigurations.
Provide developers with actionable, environment-specific remediation guidance
Findings are explained in plain language and linked to the affected components, with recommended fixes and contextual proof of exploitability to help developers remediate quickly and confidently.
Validate and prioritize findings with AI-driven exploit simulation
Jit’s AI Agents automatically validate detected vulnerabilities by simulating real exploit paths, filtering false positives and surfacing issues that can actually be exploited in your environment.
Detect infrastructure security issues in runtime with Cloud Security Posture Management (CSPM)
Continuously monitor cloud environments for misconfigurations and policy drift
Jit’s CSPM scanner continuously evaluates your AWS, GCP, and Azure environments against best practices and security baselines — detecting misconfigurations, overly permissive access policies, and compliance gaps in real time.
Correlate cloud misconfigurations with real exploitability for accurate prioritization
Jit’s AI Agents cross-reference CSPM findings with runtime and identity context to determine which issues are actually exploitable — reducing alert noise and helping teams focus on risks that matter.
Continuously enforce compliance with frameworks like CIS, SOC 2, and ISO 27001
Compliance violations are automatically mapped to industry frameworks and continuously tracked, giving AppSec and cloud teams clear visibility into posture gaps and the evidence needed for audits.
Detect supply chain security risks with CI/CD Misconfiguration Detection
Continuously detect security misconfigurations across your CI/CD pipelines
Jit’s CI/CD scanner continuously audits your build and deployment pipelines — detecting insecure permissions, exposed credentials, missing validations, and unsafe job configurations that could be exploited to compromise releases.
Correlate pipeline vulnerabilities with code and cloud context for accurate risk insight
Jit’s AI Agents map CI/CD findings to affected repositories, identities, and cloud resources, validating which misconfigurations are actually exploitable in your environment — reducing noise and false positives.
Start scanning with one-click activation
Connecting Jit with GitHub enables one-click activation, which runs daily scans of your codebase and CI/CD pipelines.
Surface security issues in ephemeral infrastructure with serverless and K8s cluster scanning
Continuously scan serverless and Kubernetes environments for misconfigurations and vulnerabilities
Jit continuously scans Kubernetes clusters, Helm charts, and serverless configurations to detect insecure permissions, exposed secrets, and unpatched dependencies to ensure workloads are secure from code to runtime.
Correlate cluster and function risks with runtime context to identify real attack paths
Jit’s AI Agents connect IaC, container, and runtime telemetry to validate whether misconfigurations or vulnerabilities are actually exploitable — surfacing real attack paths instead of static findings.
Deliver clear, contextual remediation guidance for every environment
Findings are explained in plain English and mapped to their affected pods, services, and functions, providing developers and DevOps teams with accurate, environment-specific fixes to close gaps fast.
Inventory your open source components with Software Bill of Materials (SBOM)
Automatically generate and maintain a continuously updated SBOM
Jit automatically builds and refreshes your SBOM across every repository and environment, giving you real-time visibility into all open-source and third-party components used in your software supply chain.
Correlate SBOM data with live vulnerability intelligence for proactive risk management
Jit’s AI Agents cross-reference SBOM components with live CVE data from sources like NVD, GitHub Security Advisories, and OSS Index — ensuring you’re instantly alerted to new vulnerabilities that affect your dependencies.
Simplify compliance and third-party risk reporting with one source of truth
Continuously updated SBOMs map dependencies, versions, and licenses across all services — giving AppSec, compliance, and engineering teams a unified, audit-ready view of software composition and security posture.
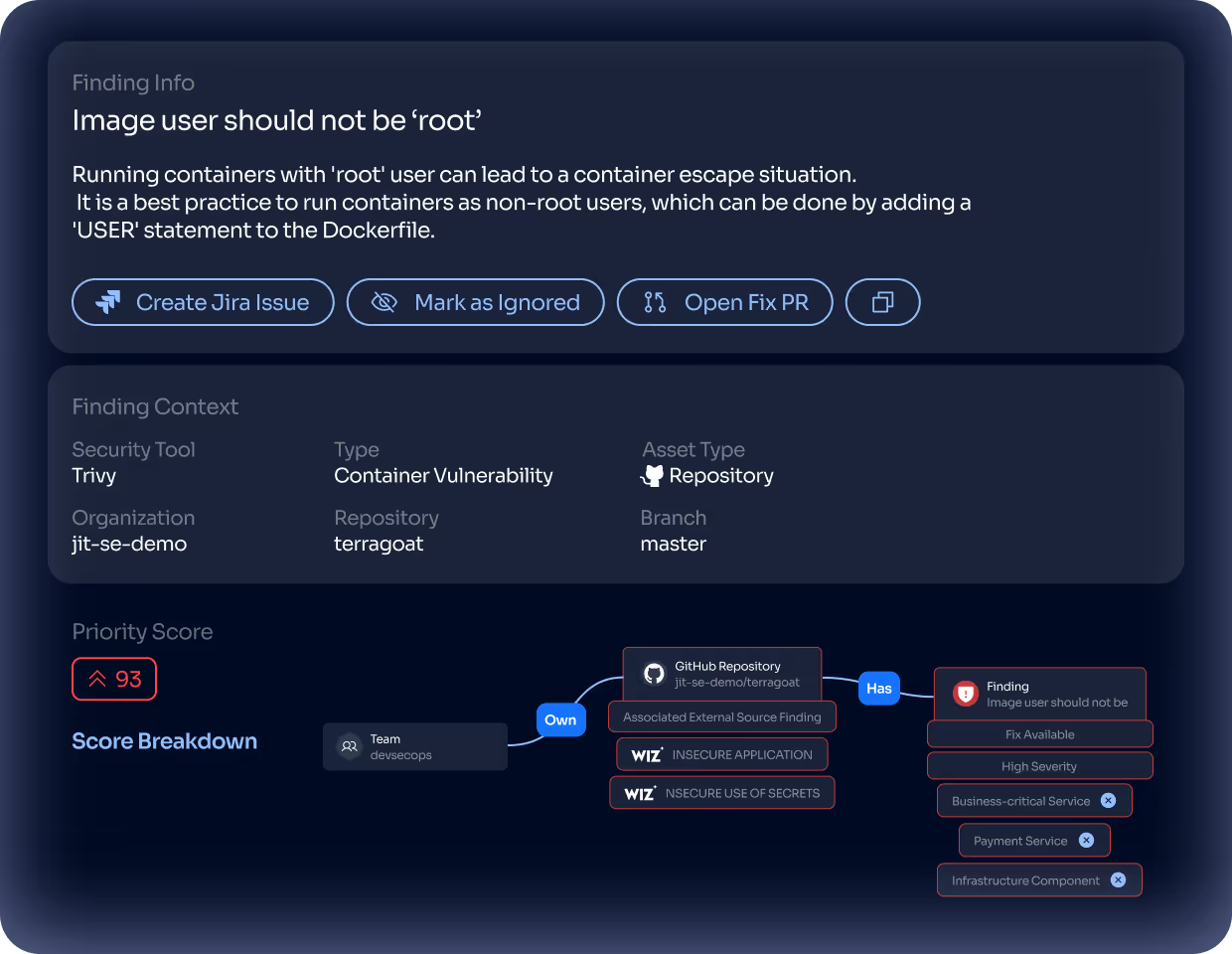
Detect security issues in your Dockerfiles and images with Container Scanning
Continuously scan container images for vulnerabilities and misconfigurations
Jit’s container scanner automatically inspects images across registries and pipelines to detect vulnerabilities in base images, packages, and configurations.
Correlate container vulnerabilities with runtime and IaC context for precise prioritization
Jit’s AI Agents connect container findings with the underlying infrastructure and live runtime data, validating which vulnerabilities are actually reachable or exploitable.
Provide developers and DevOps teams with clear, contextual remediation guidance
Findings are enriched with exploit evidence and plain-language explanations, offering targeted remediation steps that integrate seamlessly into existing CI/CD workflows.
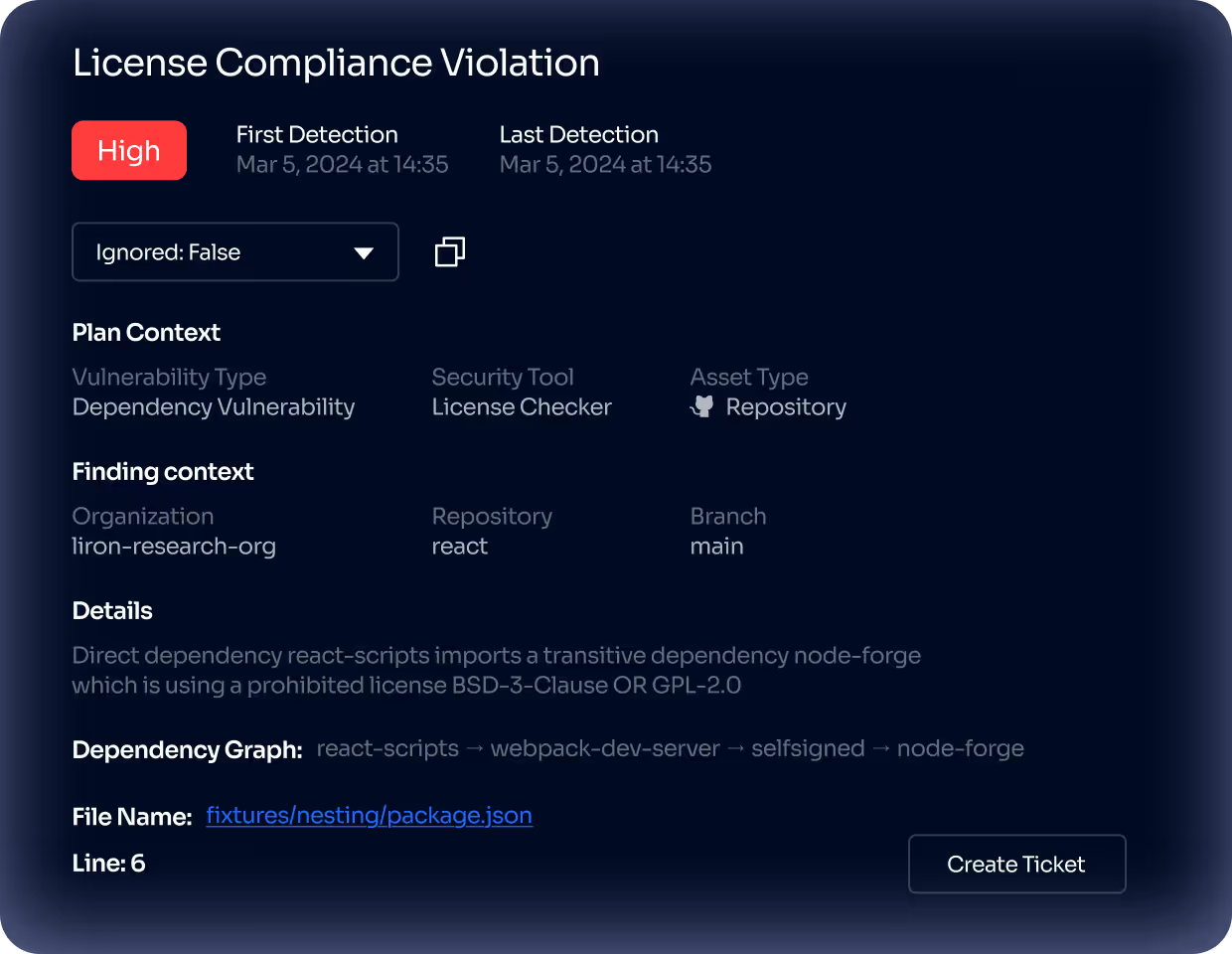
Highlight legal risks with Open Source Licensing Scanning
Continuously detect and track open-source license usage across all dependencies
Jit’s OSS License Detection scanner automatically identifies and catalogs licenses for every open-source dependency in your codebase — providing real-time visibility into license types, obligations, and potential conflicts.
Correlate license data with business and compliance requirements
Jit’s AI Agents cross-reference license findings with organizational policies and compliance frameworks to flag components that violate internal or third-party use restrictions.
Get a single, continuously updated view of your organization’s license posture
License insights are automatically included in your SBOM and continuously refreshed, giving AppSec, legal, and compliance teams a unified, audit-ready view of license exposure across all projects and environments.